Hello @Akr ofly ,
Thank your update and patience.
I took the time to deploy NDES in my test environment. Here are the detailed deployment steps for your reference (I use the built-in domain Administrator account instead of any service account).
AD domain
Domain name: fabrikam.com
Enterprise root CA server is installed on one domain member server (CA2.fabrikam.com).
It is an existing CA server: CA2.fabrikam.com
Deploy NDES steps
Step1
On CA server, add Domain Administrator account---fabrikam\Administrator to local IIS_IUSRS group.
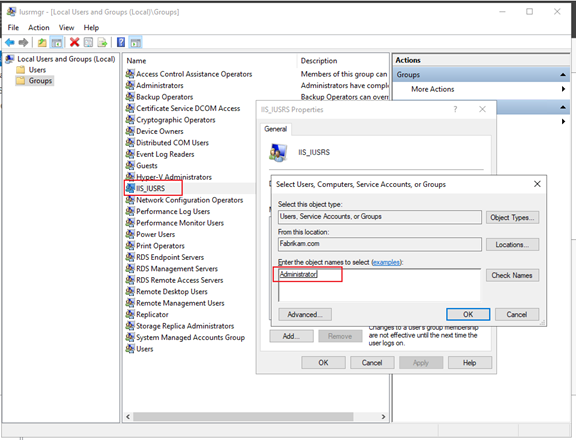
Step2
Give built-in Domain Administratorthe read and enroll permissions on the following three certificate templates.
And issue the three certificate templates on CA server.
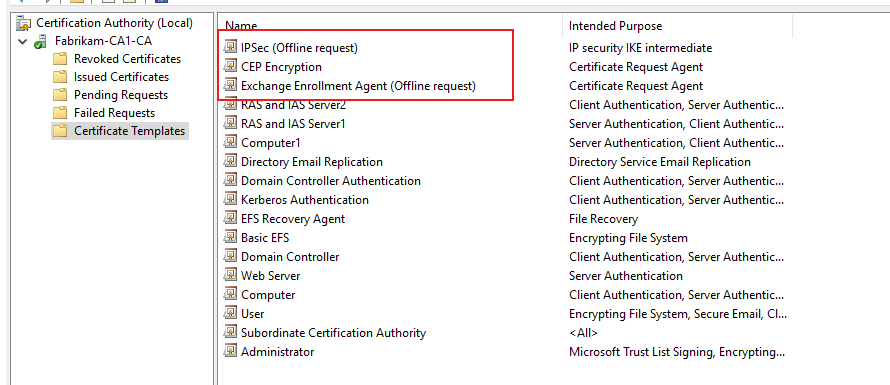
Step3
Installed NDES on the same server as CA server.
1.Add NDES role.
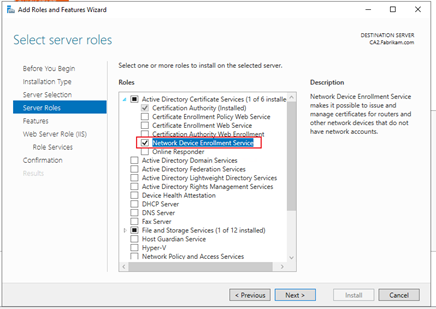
2.Install NDES.
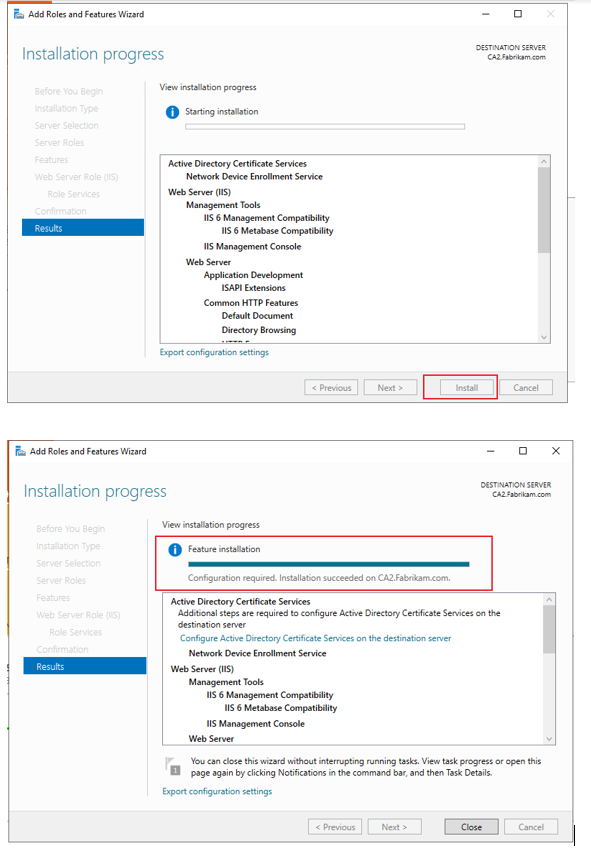
3.Configure NDES.
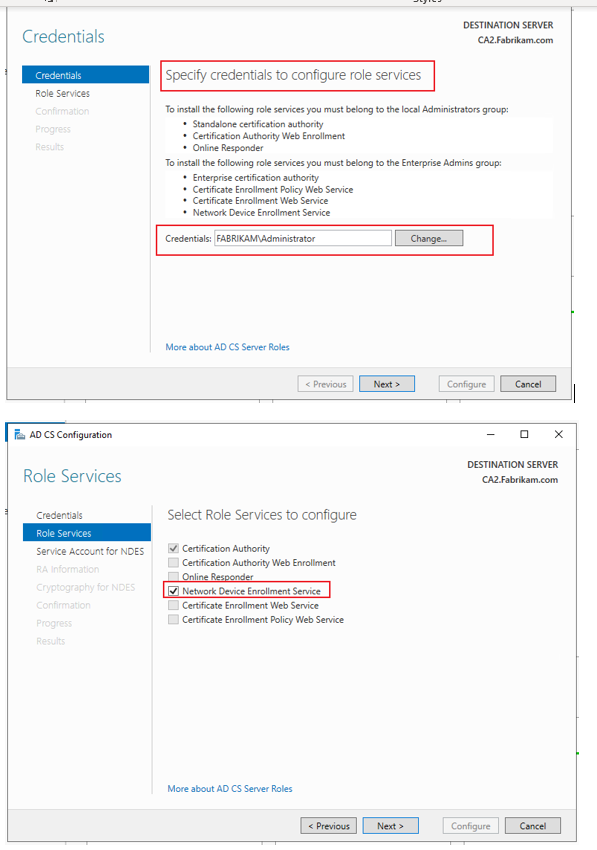
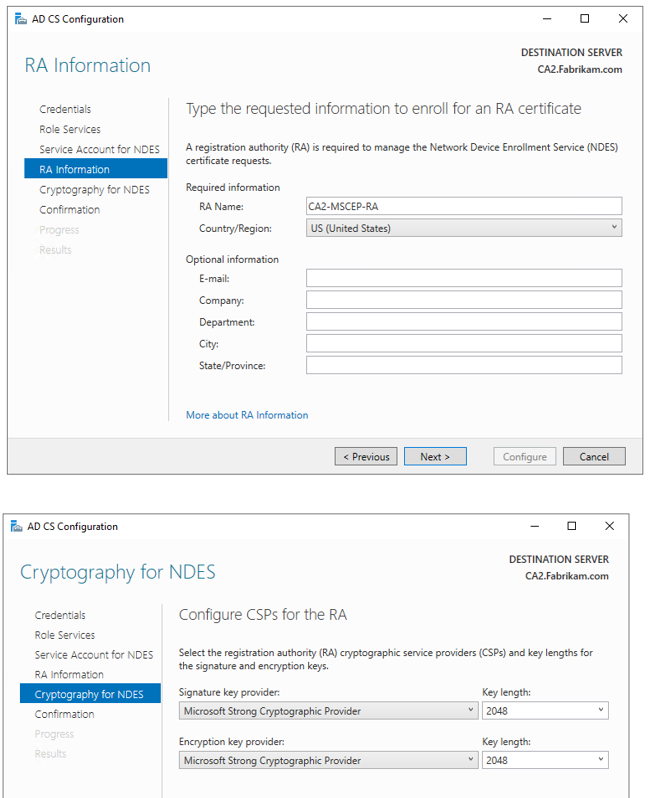
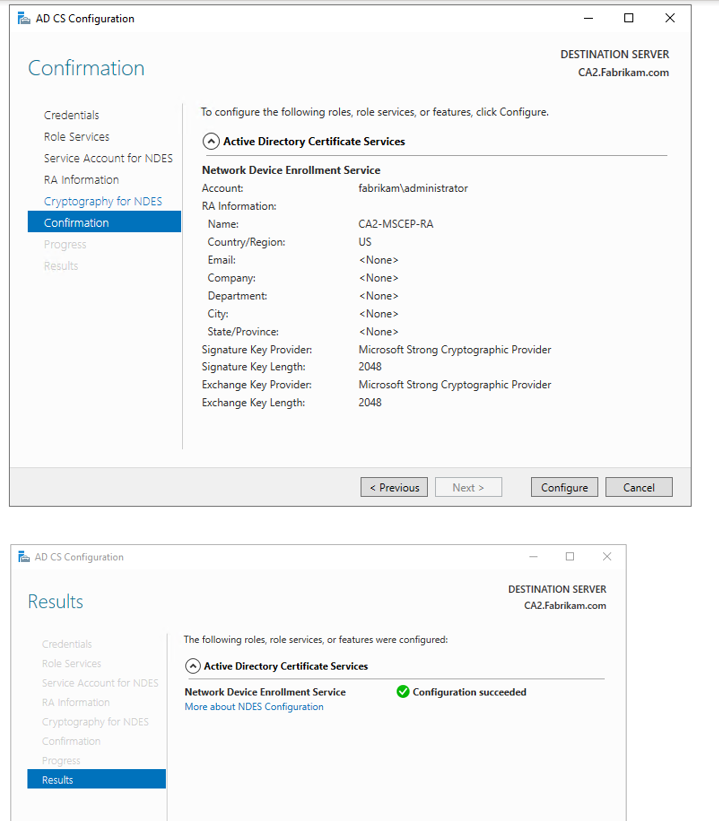
Step4
Access mscep webpage in IE.
http://ca2.b.local/certsrv/mscep/
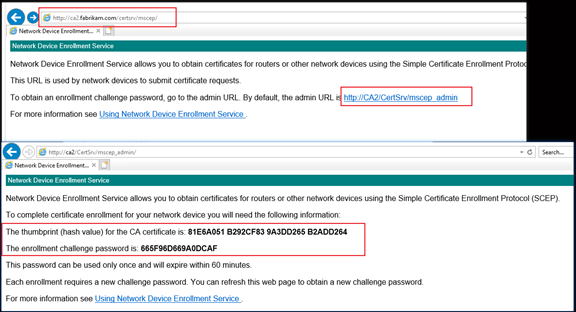
OR http://ca2/CertSrv/mscep_admin/
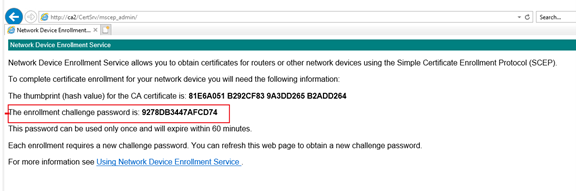
Hope the information above is helpful. If anything is unclear, please feel free to let us know.
Best Regards,
Daisy Zhou








