Hi @Johnny Humphrey ,
Thanks for your response and additional details. I believe the confusion here is the difference between Azure RBAC (RBAC at Azure Synapse resource in Azure Portal - refer to image 1 below) and Synapse RBAC in Synapse Studio (Refer to image 2 below).
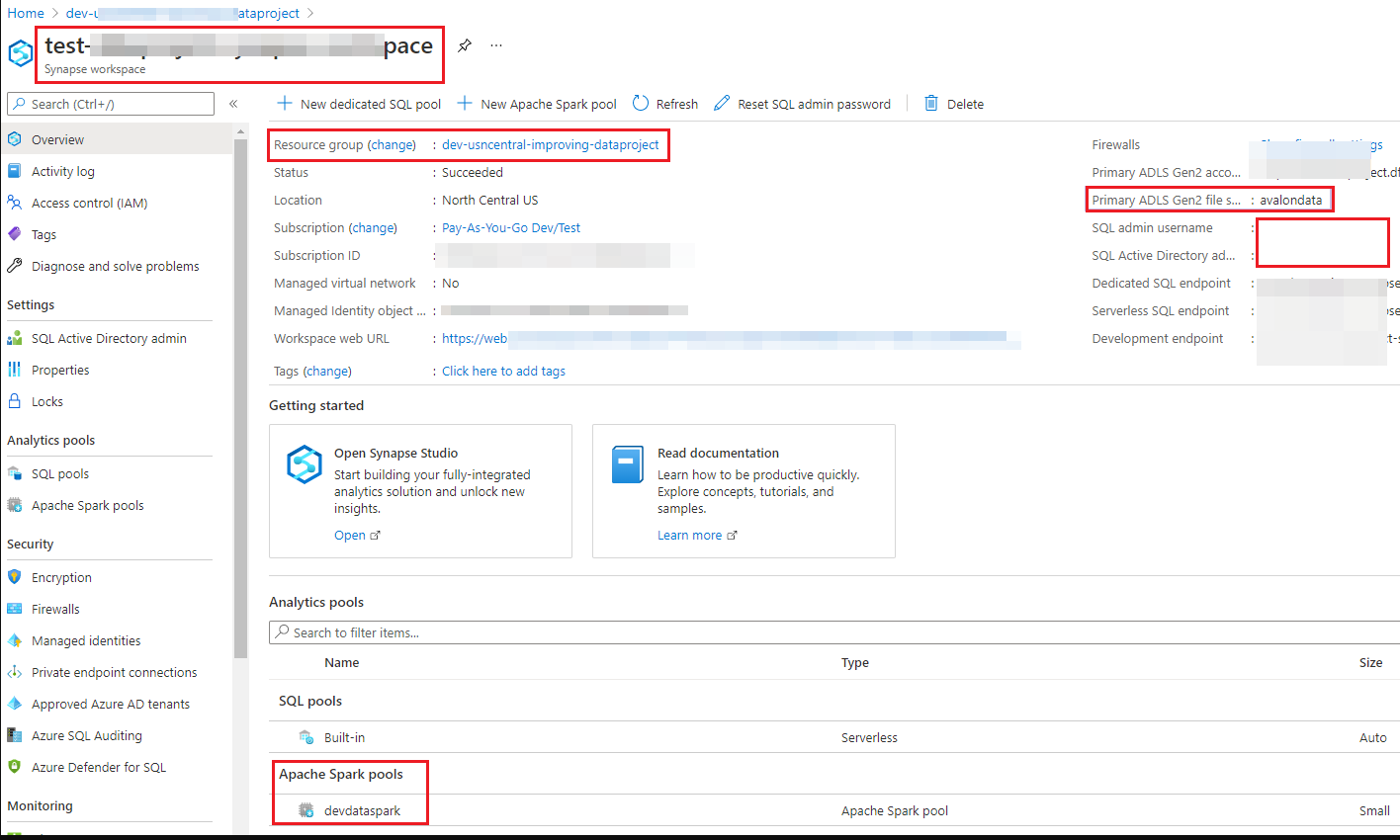
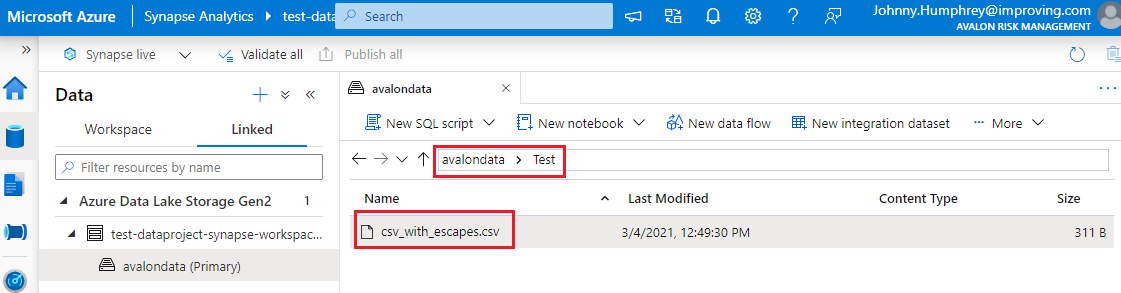
Image 1: Azure RBAC on Azure Synapse resource in Azure Portal
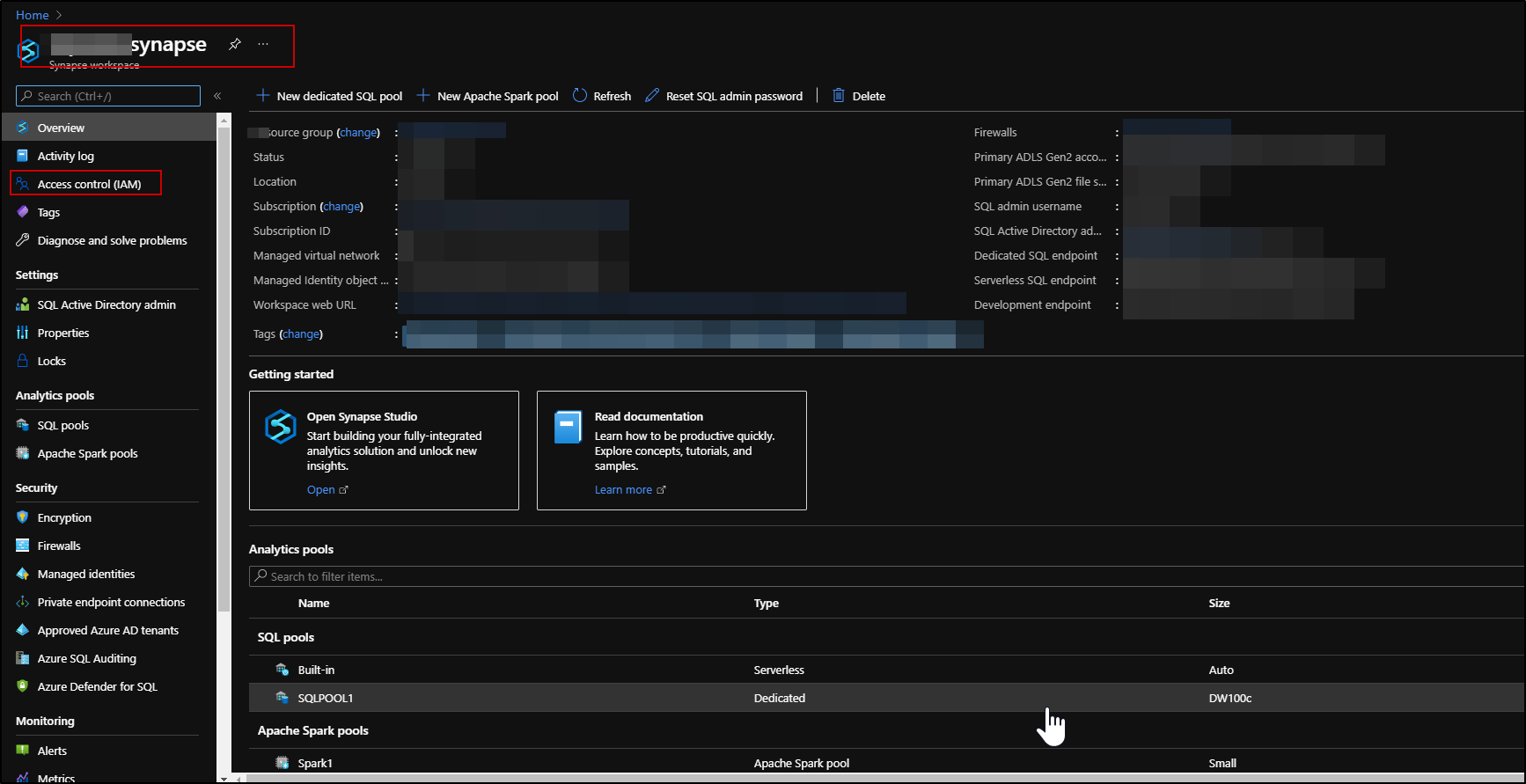
An Azure RBAC is used to manage who can create, update, or delete the Synapse workspace and its SQL pools, Apache Spark pools, and Integration runtimes.
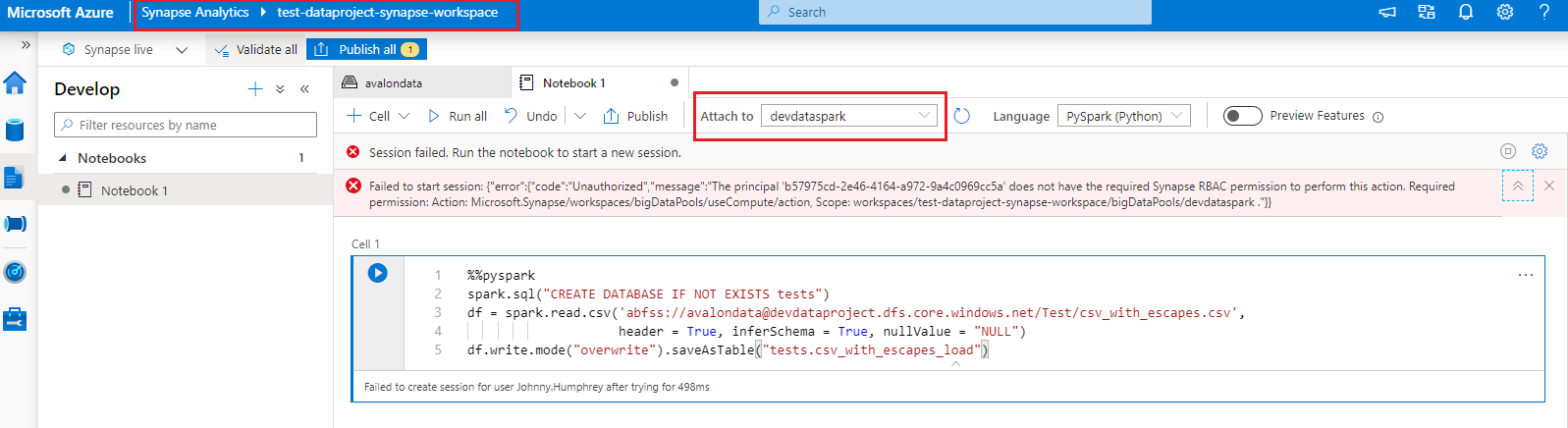
Image2 : Synapse RBAC in Synapse Studio
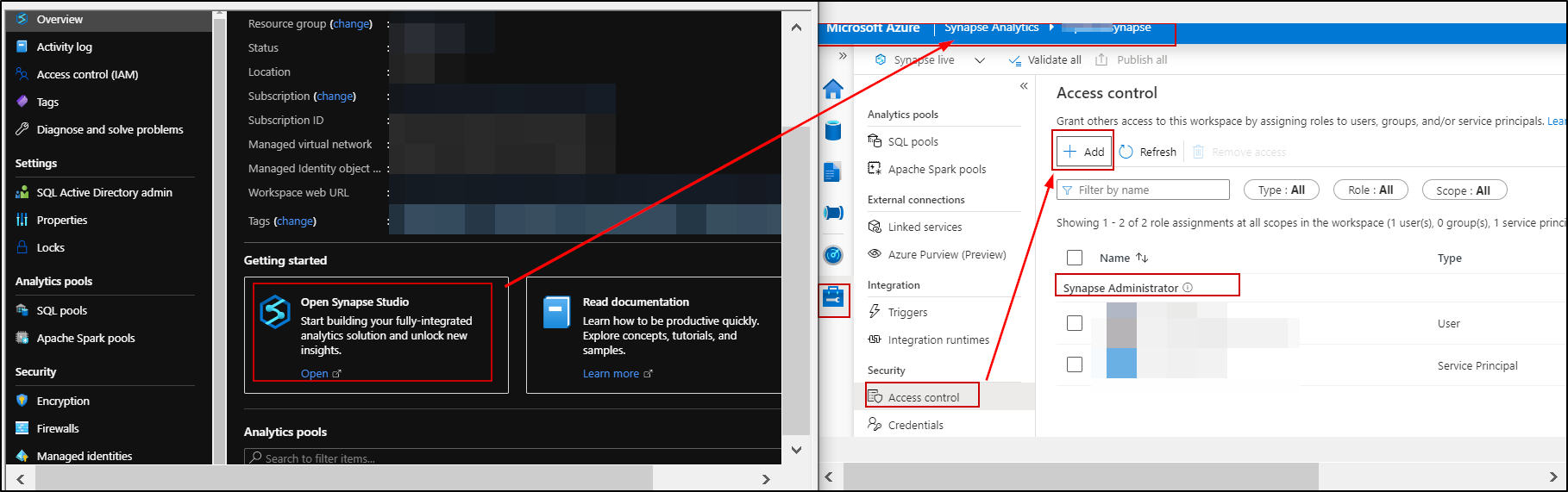
A Synapse RBAC is used to manage who can:
- Publish code artifacts and list or access published code artifacts,
- Execute code on Apaches Spark pools and Integration runtimes,
- Access linked (data) services protected by credentials
- Monitor or cancel job execution, review job output, and execution logs.
Synapse RBAC is managed from within Synapse Studio using the Access control tools in the Manage hub.
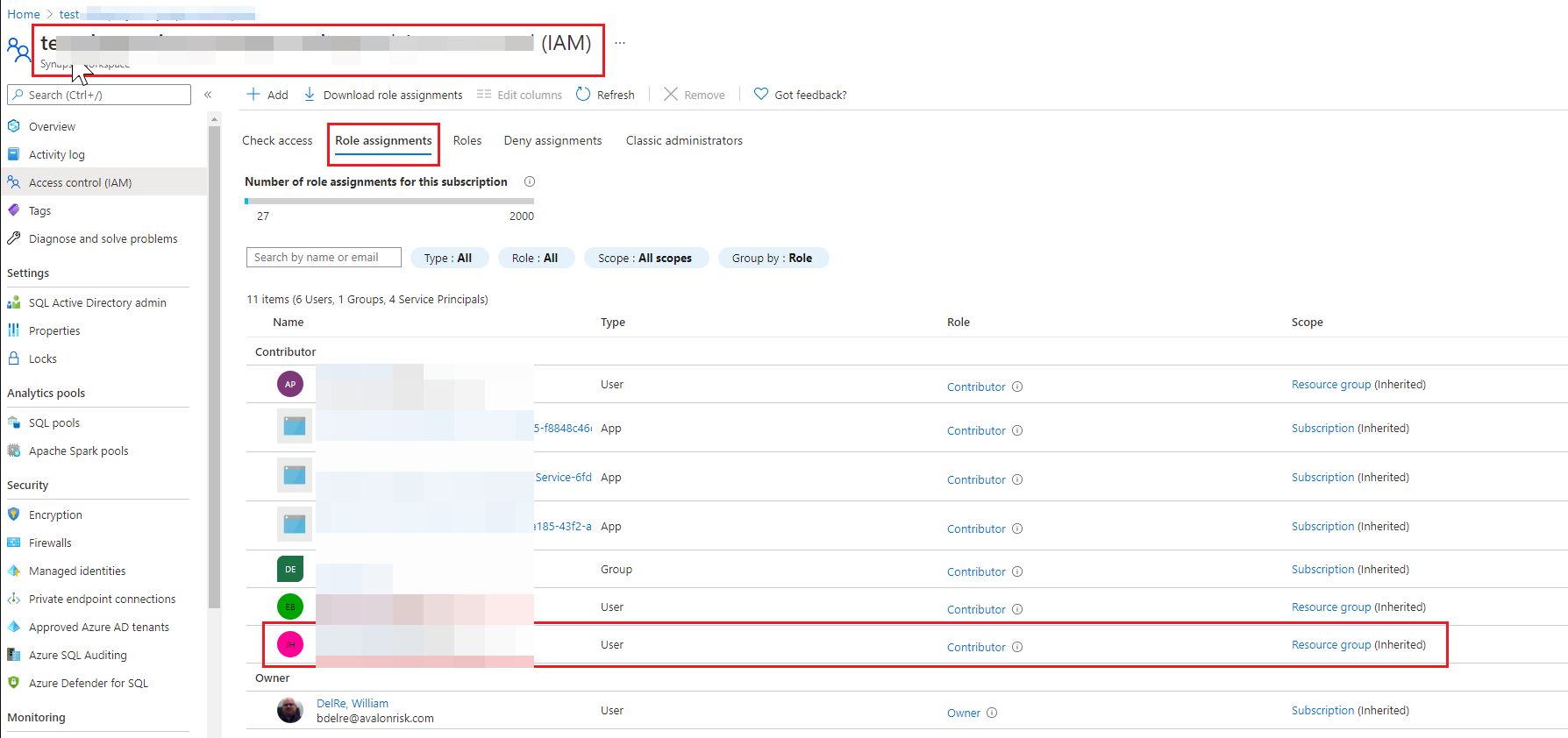
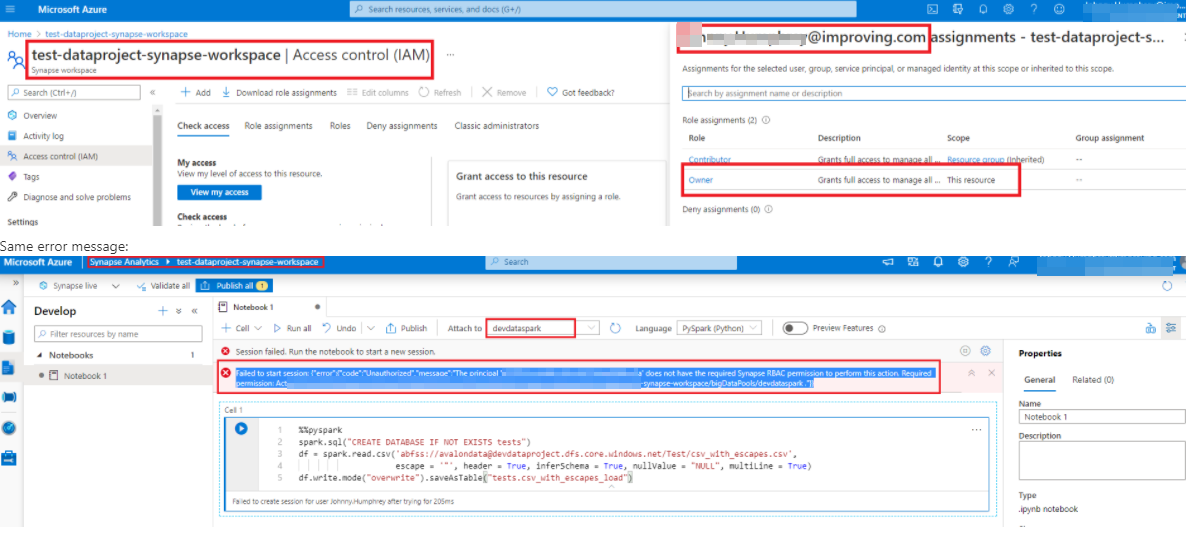
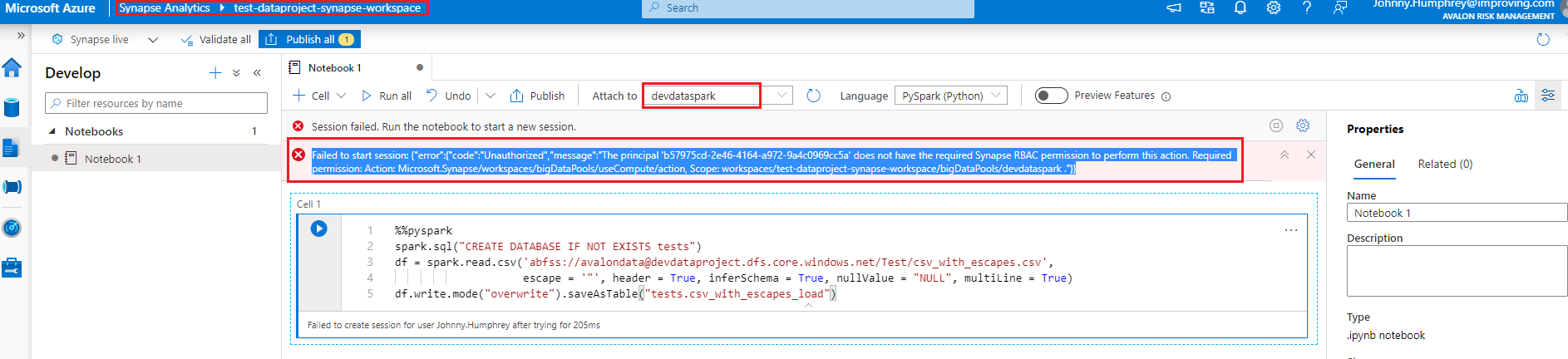
Based on the above details you have shared, I have noticed that the your user has been granted Azure RBAC in Azure Portal but not the Synapse RBAC in Synapse Studio. Which is why authorization error is thrown. A user with Synapse Administrator has to grant your user either of these roles - Synapse Administrator or Synapse Contributor or Synapse Compute Operator within the Synapse Studio -> Manage Hub -> Access control (i.e within Workspace) in order to perform workspaces/bigDataPools/useCompute/action actions.
> 2 other things to note: > > I have another subscription in a different directory, and I'm the one who created the Synapse workspace, resource group, storage account, and Spark pool, so I am of course the Owner there, and I have no problems running things.
Since you are the user who had created Azure Synapse resource, by default you will have Synapse Administrator role (Synapse RBAC permission) on Synapse Studio. Hence you haven't noticed any permission issue as you have full privilege on the Synapse studio.
> In the workspace above, where I get the error, I am a Guest on that subscription. I would think that wouldn't make a difference, since it is called Role-Based Access Control, and not Role-and-User-Type-Based Access Control, but could the fact that I am a guest in the subscription be affecting things?
Since you are a guest user on that resource, a user with 'Synapse Administrator' role have to grant your user either of these permission - Synapse Administrator or Synapse Contributor or Synapse Compute Operator within the Synapse Studio -> Manage Hub -> Access control (i.e within Workspace) in order to perform workspaces/bigDataPools/useCompute/action actions.
Here are couple of helpful docs about Synapse RBAC:
Hope this info clarifies. Do let us know if you have further query.
Thank you Please do consider to click on "Accept Answer" and "Upvote" on the post that helps you, as it can be beneficial to other community members.