I have these same files on my server and I have the same question.
HAFNIUM and aspx files
Hi All,
We have run scanner on both of our exchange 2016 servers and one came back positive and the other negative.
However, on both servers, these files are .aspx files in %PROGRAMFILES%\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth:
errorFE.aspx
ExpirtedPassword.aspx
frowny.aspx
logoff.aspx
logon.aspx
OutlookCN.aspx
RedirSuiteServiceProxy.aspx
signout.aspx
Are these file normal in exchange 2016?
Also these files were created way before the attack.
5 answers
Sort by: Most helpful
-
-
Ben Langers 1 Reputation point
2021-03-09T23:12:17.837+00:00 I have got those same files on an Exchange 2019 machine.
There is one extra: getidtoken.htm
Looks a bit out of place, there...
Will run a restore of a version before this exploit to verify and post back... -
Joyce Shen - MSFT 16,641 Reputation points
2021-03-10T05:54:40.223+00:00 I have checked in my environment, and found the same files under the path.
These files should be nomal files for Exchange. For security reasons, I would suggest you use the MSERT.exe tool to scan your server.
For more information: Microsoft Exchange Server Vulnerabilities Mitigations – updated March 9, 2021 ,mainly refer to the part Microsoft Support Emergency Response Tool (MSERT) to scan Microsoft Exchange Server.
If an Answer is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.
-
Ben Langers 1 Reputation point
2021-03-11T08:04:09.02+00:00 I can confirm I have the exact same files with the same creation dates and sizes on a restore of that box from before the exploit. Seems legit...
-
Goran Sladakovic 1 Reputation point
2022-05-06T06:26:08.873+00:00 The files you pointed out exist on my exchange also however I also had a recent incident where Backdoor shell script was installed in the ecp\auth virtual directory that looked like this:
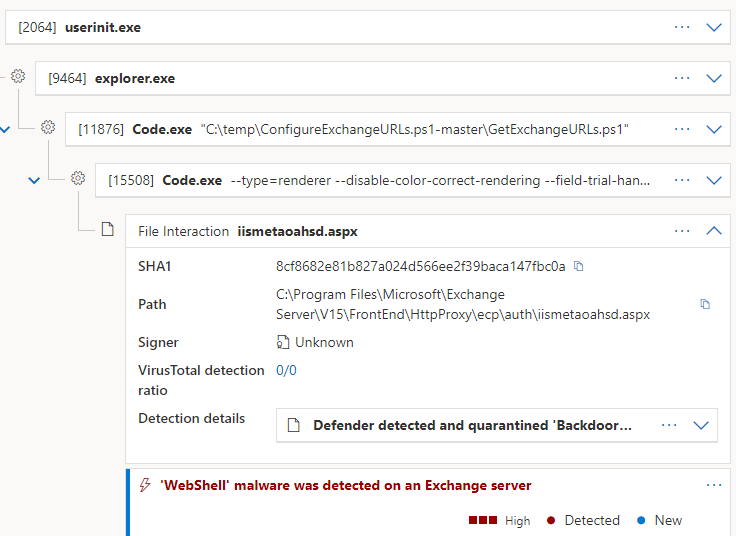
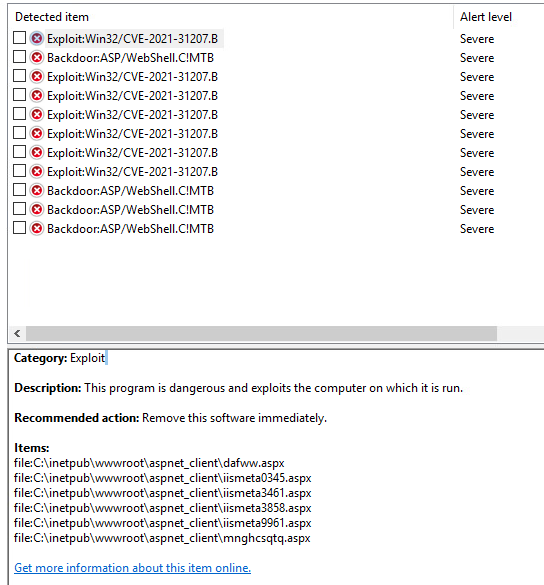
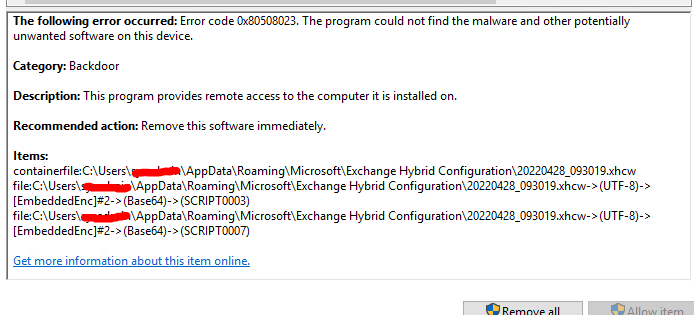
Here are some useful links that helped me narrow down the issue and remove them:
https://www.microsoft.com/security/blog/2020/06/24/defending-exchange-servers-under-attack/