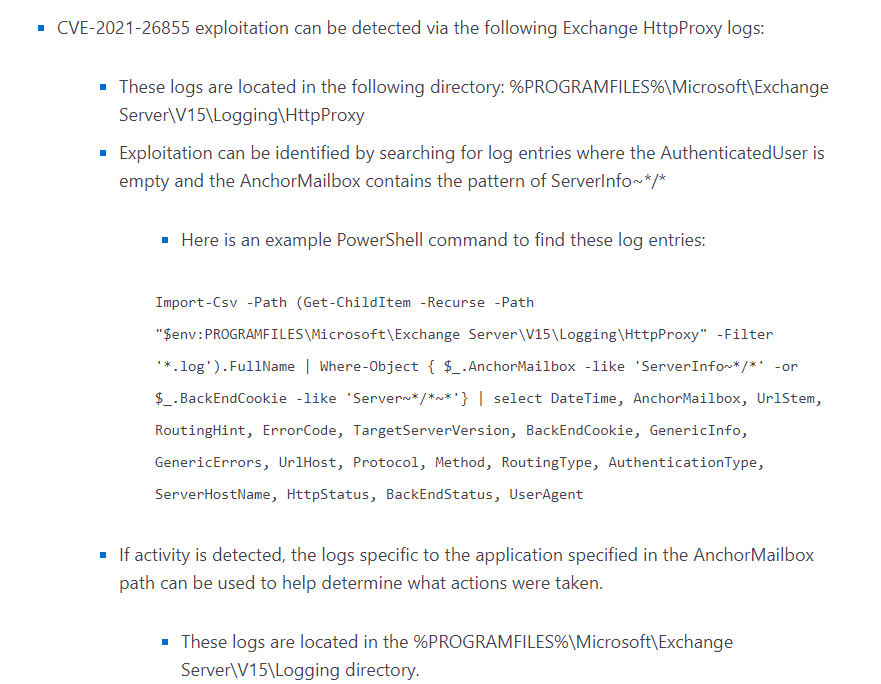
Hello everybody,
a german customer is running Exchange 2016 and installed CU19 and the Hafnium patch on 2021-03-04. Running the then current version of the Test-Hafnium.ps1 script, which the Exchange team put on GitHub, showed:
"DateTime","AnchorMailbox"
"2021-03-03T08:06:05.126Z","ServerInfo~a]@sn .customerdomain.de/autodiscover/autodiscover.xml?#"
"2021-03-03T11:33:18.593Z","ServerInfo~a]@sn .customerdomain.de/autodiscover/autodiscover.xml?#"
"2021-03-03T13:39:33.153Z","ServerInfo~a]@sn .customerdomain.de/autodiscover/autodiscover.xml?#"
"2021-03-03T13:39:36.546Z","ServerInfo~a]@sn .customerdomain.de/mapi/emsmdb/?#"
"2021-03-03T13:39:38.925Z","ServerInfo~a]@sn .customerdomain.de/ecp/proxyLogon.ecp?#"
"2021-03-03T13:39:42.650Z","ServerInfo~a]@sn .customerdomain.de/ecp/DDI/DDIService.svc/GetObject?msExchEcpCanary=-OlNq08-d06AaYApbaSPFtoynh_c39gIS35a8dhtli23cZk8G1r--7R0C8P_ce8LqCfENIZYkg0.&schema=OABVirtualDirectory#"
I would interpret this as the effort to use an eventually already installed Hafnium backdoor, but not as a sign of a successfull attack, neither for the installation of the backdoor nor to a successful exploitation. So there was someone who tried if that server had the backdoor installed, but I feel it was never installed. IIS logs were available down to early January 2021.
Would you agree or is this a sign that the server had been compromized?