Hi,
Sorry for my late reply since I was taking a holiday since last Friday.
Regarding of specific IP which was blocked by Windows Firewall, if you enable the firewall log, then we could check the firewall log to see if the traffic was blocked by Windows Firewall. In firewall log, if we find the traffic was dropped, the rules for blocking specific IP was initiated successfully in our firewall.
Attaching my test result for your reference. As you can see in the firewall log, we could receive traffic from the specific IP, once received, the traffic was dropped by windows firewall.
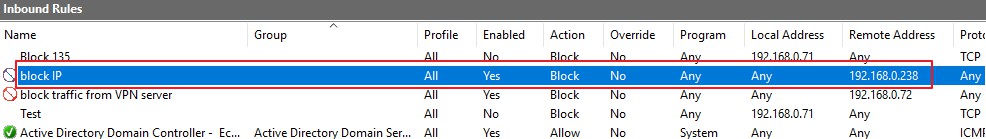
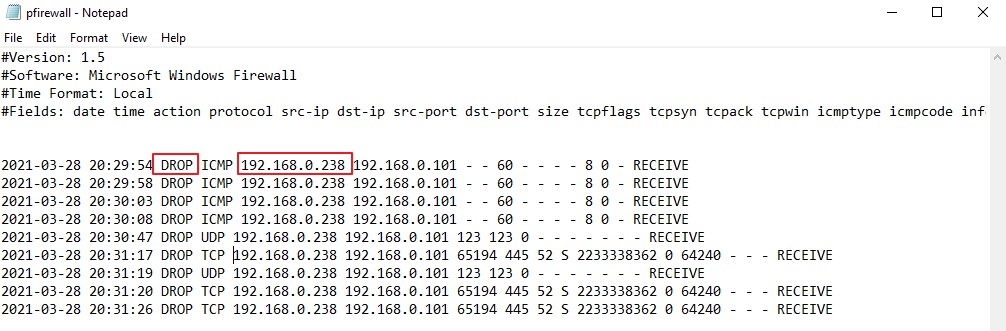
Best Regards,
Sunny
----------
If the Answer is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.