Hi all I have the following setup
2x RRAS servers running Windows Server 2019 Using EAP-TLS for SSTP and IKEv2 authentication
1x NPS Server ( Server 2016) on prem for the RADIUS authentication (working)
1x NPS Server (Server 2016) in Azure for backup RADIUS authentications (broken)
I am trying to create a backup NPS server in Azure (we have a VPN connection to Azure) but im having problems with the authentication.
The client's connection times out and I get the following error in the client's event viewer:
CoId={E4FD7873-208A-0000-4B26-00E58A20D701}: The user SYSTEM dialed a connection named Always On VPN - User which has failed. The error code returned on failure is 812.
On the RRAS side I get the following: }:
The user user@mathieu.company .com connected from 1.2.3.4 but failed an authentication attempt due to the following reason: The connection was prevented because of a policy configured on your RAS/VPN server. Specifically, the authentication method used by the server to verify your username and password may not match the authentication method configured in your connection profile. Please contact the Administrator of the RAS server and notify them of this error. and CoId={E4FD7873-208A-0002-CA27-FFE48A20D701}: The following error occurred in the Point to Point Protocol module on port: VPN1-499, UserName: user@mathieu.company .com. The connection was prevented because of a policy configured on your RAS/VPN server. Specifically, the authentication method used by the server to verify your username and password may not match the authentication method configured in your connection profile. Please contact the Administrator of the RAS server and notify them of this error.
Both NPS servers have identical configuration but on prem one works and Azure doesn't.
I ran wireshark on the broekn NPS server and saw a lot of fragmentation:
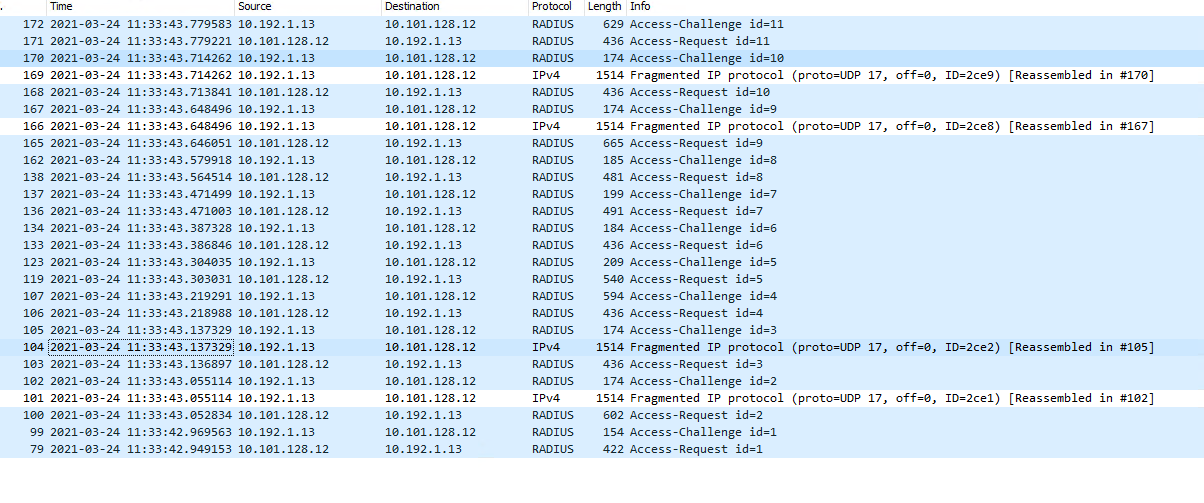
A capture on the working server shows no fragmentation, and then I see the "Access-Accept" and the client gets connected:
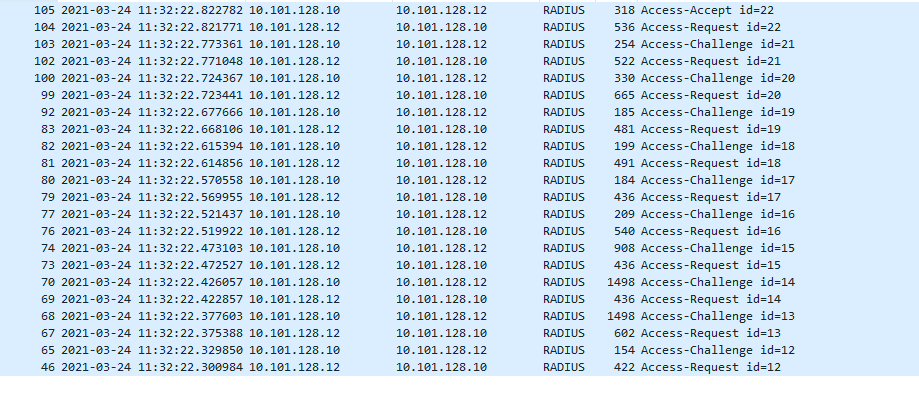
I never see "Access-Accept" on the broken server.
I tried adjusting the MTU on the NPS server and using the "Framed-MTU" setting inside the NPS network policy set to 1344 but neither helped.
Does anyone have any ideas?
I read online that EAP-TLS doens't work properly with fragmentation and this is really the only clue of the solution I have...

