
Hello @DaveC ,
Thank you for your patience.
After my research, for external trust, there is some conditions for Kerberos to be used.
Table 1 External vs. Forest Trusts
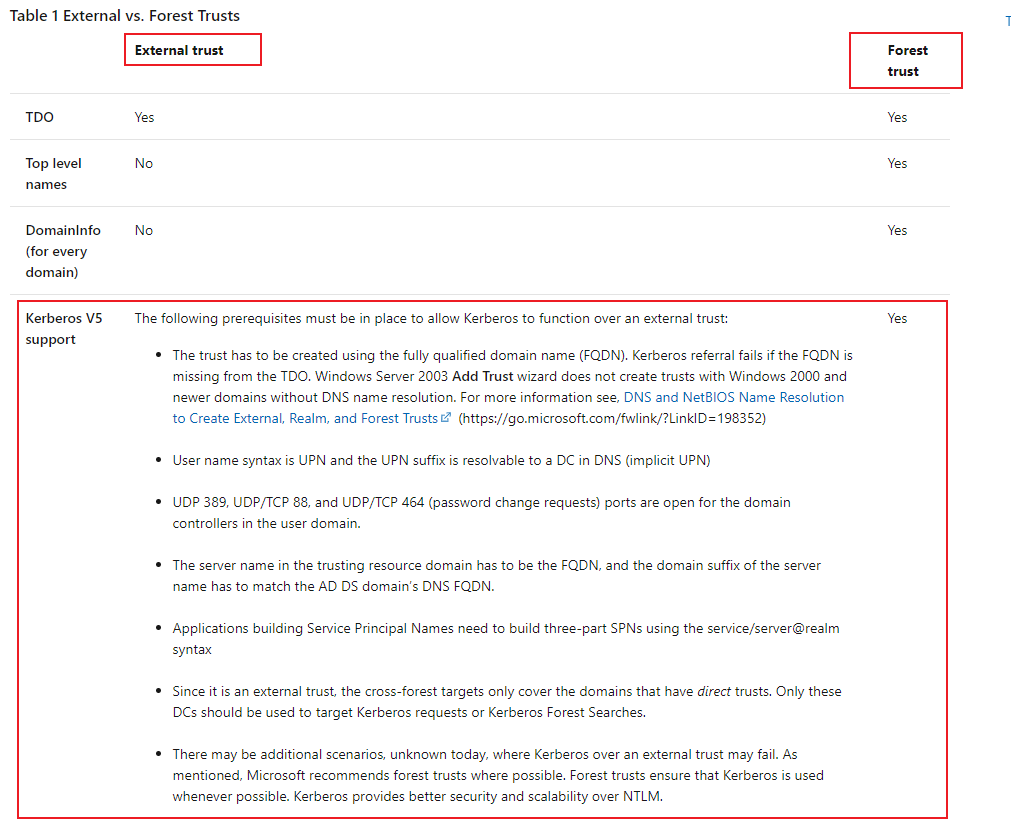
Conditions for Kerberos to be used over an External Trust
https://learn.microsoft.com/en-us/archive/blogs/activedirectoryua/conditions-for-kerberos-to-be-used-over-an-external-trust
Technologies for Federating Multiple Forests
https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2003/dd560679(v=ws.10)?redirectedfrom=MSDN
Q:Are there any other suggestions for implementing the desired delegation scenario which do not weaken the security of an admin workstation?
Suggestion: A forest trust enables a transitive trust between all of the domains in two forests. Microsoft recommends a forest trust be created between forests rather than an external trust. A forest trust ensures that Kerberos is used whenever possible. Kerberos provides better security and scalability over NTLM.
Should you have any question or concern, please feel free to let us know.
Best Regards,
Daisy Zhou