anonymous user, Thank you for reaching out. Since you are using Logic Apps, hence the OAuth flow that would be used here would be the Client_Credentials flow and not Authorization_Code_Grant Flow of OAuth.
To explain this further, for your Logic App to fetch a token from AAD, and then use that token further to call any api, for eg: Microsoft Graph API, the token would be requested by the application in its context and then use that token to call further APIs. It would be completely a non-interactive logon session and hence client_credentials flow of OAuth would be used here. The main steps to use Logic Apps and to get a bearer token from AAD would be:
- Register an application in AAD.
- Add the necessary permission for your API in that App Registration.
- Create a client secret and copy it.
- Copy the client ID/application ID for the app registration.
Now for the logic app you can configure follow the steps below:
- In your Logic App click Add step
- Choose the standard HTTP action
- Set the values as follows:
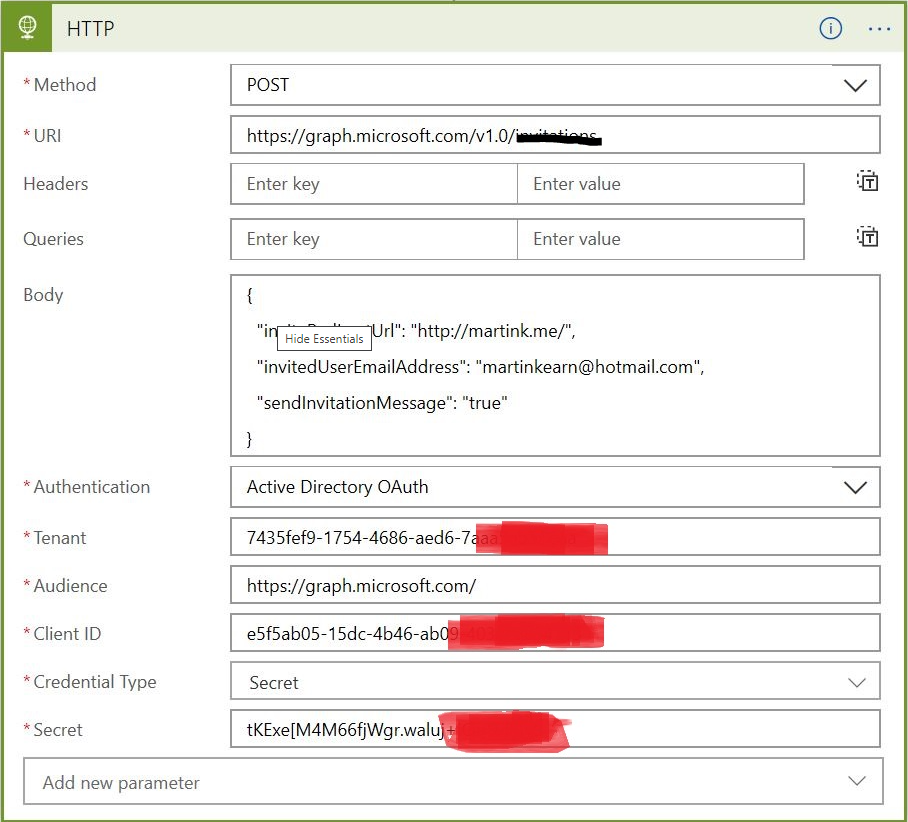
- Save the Logic App a. Run the Logic App
Hope this helps. Do let us know if this helps and if there are any more queries around this, please do let us know so that we can help you further. Also, please do not forget to accept the response as Answer; if the above response helped in answering your query.