Hi @Tom
Thanks for reaching us.
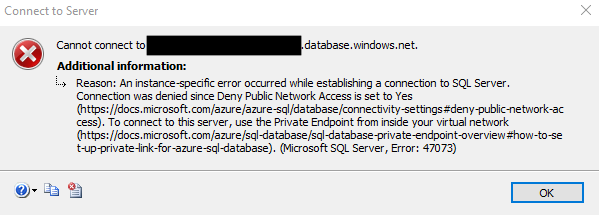
DNS plays a major role for the resolution of the FQDN.
Do nslookup for the FQDN and see is it resolving to the private IP of the private endpoint or not if it resolves to private Ip, then it takes point to site connection if not it will take internet route to reach SQL, if you see public IP then it is not reaching via private endpoint hence the error message.
- Testing : You can have host entry on your point to site client machine for the private endpoint with IP 10.1.0.4
ex: 10.1.0.4 sqldbname.privatelink.database.windows.net - Use your DNS forwarder : For on-premises workloads to resolve the FQDN of a private endpoint, use a DNS forwarder to resolve the Azure service public DNS zone in Azure. A DNS forwarder is a Virtual Machine running on the Virtual Network linked to the Private DNS Zone that can proxy DNS queries coming from other Virtual Networks or from on-premises. This is required as the query must be originated from the Virtual Network to Azure DNS.
DNS scenarios : https://learn.microsoft.com/en-us/azure/private-link/private-endpoint-dns#dns-configuration-scenarios
Hope this was helpful. Please let us know in case of any additional questions or concerns.
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.