Hello @Nick Erdos ,
Thanks for reaching out.
Could you please confirm, what type of HTTP call being used by your application to sent SAMLRequest (aka AuthNRequest) to Azure AD, either HTTP-Redirect or HTTP-POST ?
You can identity this by looking at SAMLRequest from HTTP call which done by your application, if you see HTTP 302 call and SAMLRequest sent in query string then your app using HTTP-Redirect which is most commonly used scenario.
Example: https://login.microsoftonline.com/tenant-id/saml2?SAMLRequest=###SAMLRequst####
Instead, you see HTTP POST call and SAMLRequest sent in body then your application using HTTP POST.
Here are sample for both of them:
This is my AuthRequest for test app:
<samlp:AuthnRequest xmlns="urn:oasis:names:tc:SAML:2.0:metadata" ID="F84D888AA3B44C1B844375A4E8210D9E" Version="2.0" IssueInstant="2021-10-07T08:10:24.669Z" IsPassive="false" AssertionConsumerServiceURL="https://adfshelp.microsoft.com/ClaimsXray/TokenResponse" xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" ForceAuthn="false"><Issuer xmlns="urn:oasis:names:tc:SAML:2.0:assertion">https://localhost:3000/saml/metadata</Issuer></samlp:AuthnRequest>
HTTP-Redirect- binding:
First, AuthenRequest need to be Deflate + Base64 Encode and then URLEncode. I used onlinetool to get Deflate + Base64 Encode value and then used URL Encoder.
Deflate + Base64 Encode value:
jZHLasMwEEV/xWgfS340UYRtcF4QSKEkaSndCWeCTfVwNXJo/76Ki1eF0u0wc7jnToFSq17Ug2/NET4GQB99amWwJIMzwkrsUBipAYVvxKl+PIg0ZkKDlxfpJYn2m5LseL7hnNd1tsrzdbLieZ4tHup8y9OEbZZbEr2Aw86akoTjcIM4wN6gl8aHEUuTWcJmbHFmXCRMpHk8ny/f7ntPErG7QUmuUiGQqEYE5wNpbQ0OGtwJ3K1r4Pl4KEnrfY+CUnm5Yguqj3XXOIv26uPGarpWstP46uQXPdt3CLrYB0qgjsJibOJv7d5ZbxurSLSzroGxtSlbVYxa7j/1yUmDVFNoZRupWoteZIwxeg9Dp5YL+oOuCvr7XdU3
URLEncoded above value:
jZHLasMwEEV%2FxWgfS340UYRtcF4QSKEkaSndCWeCTfVwNXJo%2F76Ki1eF0u0wc7jnToFSq17Ug2%2FNET4GQB99amWwJIMzwkrsUBipAYVvxKl%2BPIg0ZkKDlxfpJYn2m5LseL7hnNd1tsrzdbLieZ4tHup8y9OEbZZbEr2Aw86akoTjcIM4wN6gl8aHEUuTWcJmbHFmXCRMpHk8ny%2Ff7ntPErG7QUmuUiGQqEYE5wNpbQ0OGtwJ3K1r4Pl4KEnrfY%2BCUnm5Yguqj3XXOIv26uPGarpWstP46uQXPdt3CLrYB0qgjsJibOJv7d5ZbxurSLSzroGxtSlbVYxa7j%2F1yUmDVFNoZRupWoteZIwxeg9Dp5YL%2BoOuCvr7XdU3
Final result would be added in SAMLRequest HTTP query string as shown below:
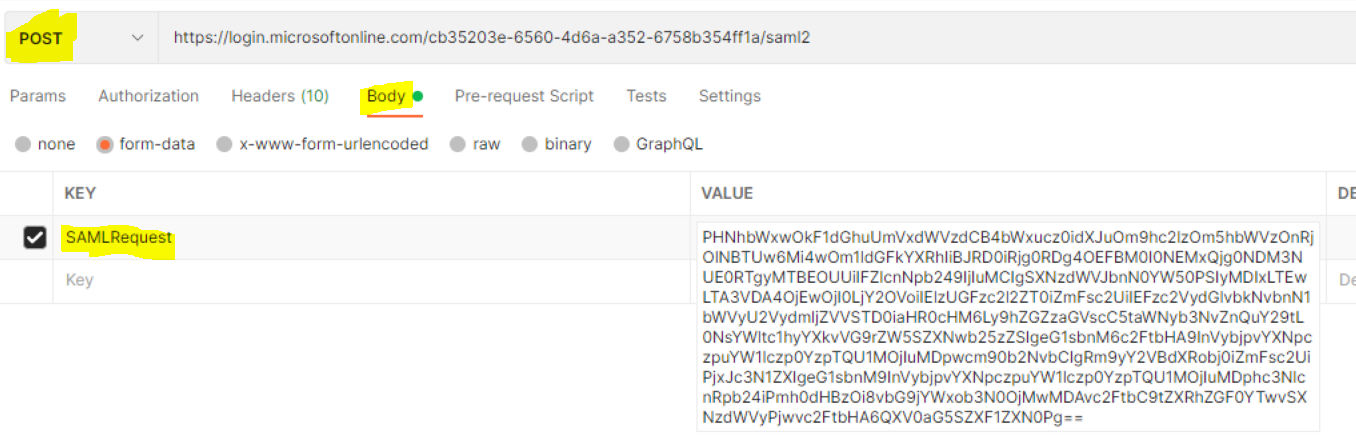
HTTP-POST- binding:
AuthnRequest need to be Base64 Encode directly and sent in HTTP POST call.
PHNhbWxwOkF1dGhuUmVxdWVzdCB4bWxucz0idXJuOm9hc2lzOm5hbWVzOnRjOlNBTUw6Mi4wOm1ldGFkYXRhIiBJRD0iRjg0RDg4OEFBM0I0NEMxQjg0NDM3NUE0RTgyMTBEOUUiIFZlcnNpb249IjIuMCIgSXNzdWVJbnN0YW50PSIyMDIxLTEwLTA3VDA4OjEwOjI0LjY2OVoiIElzUGFzc2l2ZT0iZmFsc2UiIEFzc2VydGlvbkNvbnN1bWVyU2VydmljZVVSTD0iaHR0cHM6Ly9hZGZzaGVscC5taWNyb3NvZnQuY29tL0NsYWltc1hyYXkvVG9rZW5SZXNwb25zZSIgeG1sbnM6c2FtbHA9InVybjpvYXNpczpuYW1lczp0YzpTQU1MOjIuMDpwcm90b2NvbCIgRm9yY2VBdXRobj0iZmFsc2UiPjxJc3N1ZXIgeG1sbnM9InVybjpvYXNpczpuYW1lczp0YzpTQU1MOjIuMDphc3NlcnRpb24iPmh0dHBzOi8vbG9jYWxob3N0OjMwMDAvc2FtbC9tZXRhZGF0YTwvSXNzdWVyPjwvc2FtbHA6QXV0aG5SZXF1ZXN0Pg==
Hope this helps.
------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.
