Hello @Ajeet Singh ,
Welcome to Microsoft Q&A Platform. Thank you for reaching out & hope you are doing well.
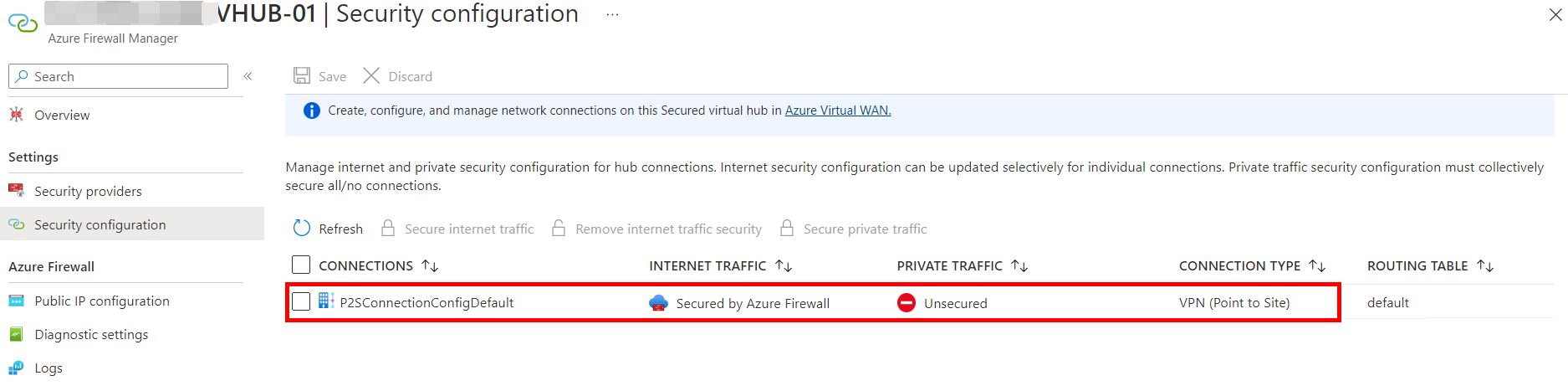
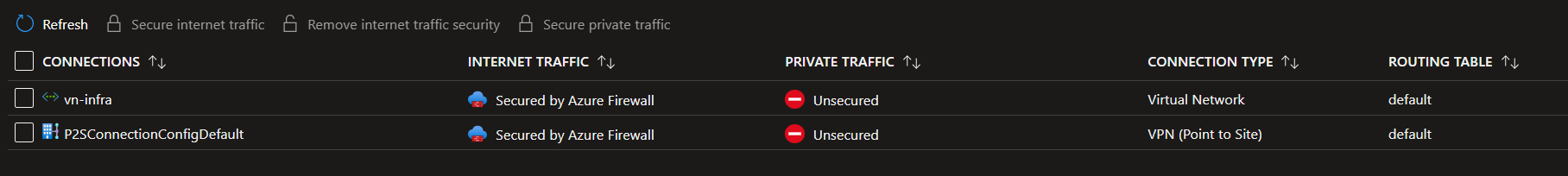
Yes, you can do forced tunneling for your P2S clients.
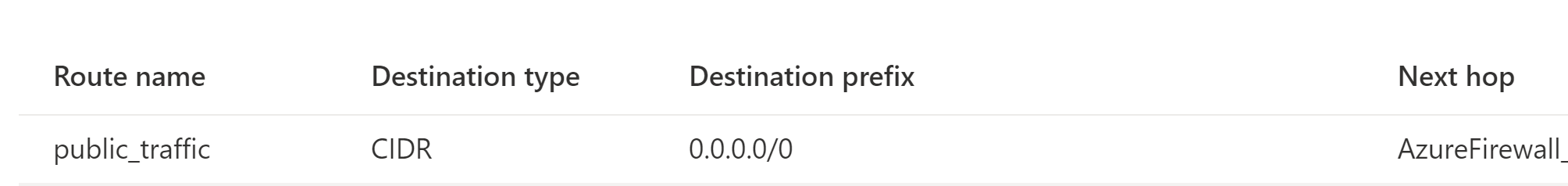
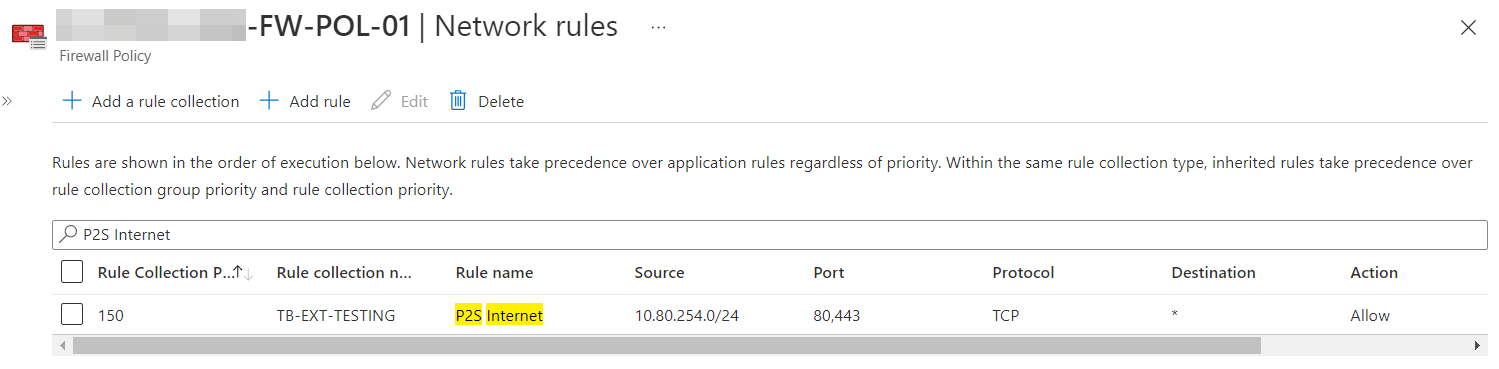
If you secure internet traffic via Firewall Manager you can advertise the 0.0.0.0/0 route to your VPN clients. This makes your clients send all internet bound traffic to Azure for inspection. Then, firewall SNATs the packet to the PIP of Azure Firewall for egress to Internet.
Kindly let us know if the above helps or you need further assistance on this issue.
----------------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.