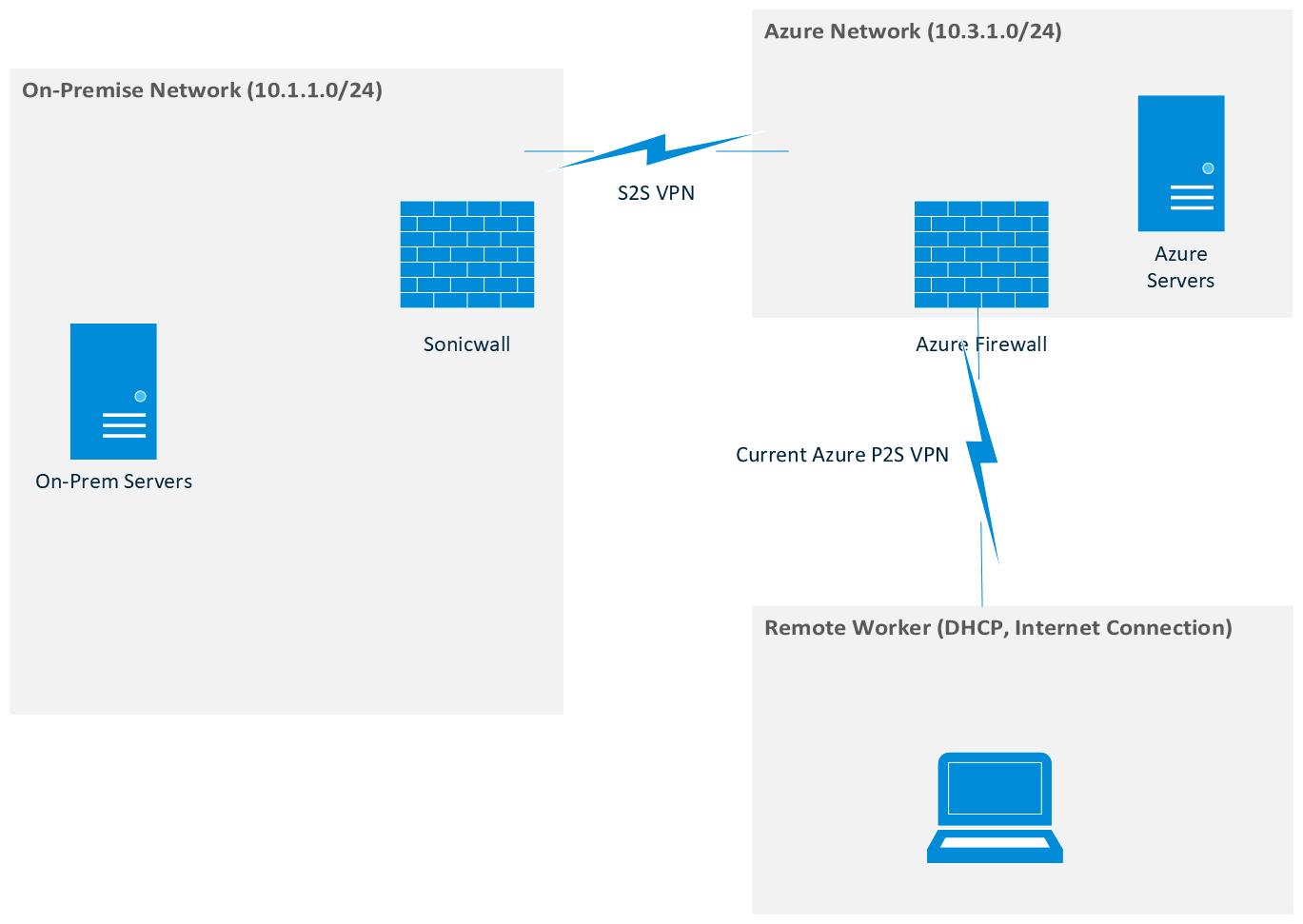
Hello @Garrett Wengreniuk ,
In order for you to be able to access your on-prem network (which is connected to Azure VPN by site to site connection) from your Point to site VPN client/laptop, your Site-to-Site VPN connection should be running BGP.
If your site to site connection between Azure and On-prem uses BGP, then you can just manually add the routes for your on-prem network to the Windows P2S client and will be able to access the on-prem network from your point to site connection/client. For non-windows clients, you do not need to add the manual routes as BGP is enough for the routes to be propagated.
To manually add the On-prem network route, you can browse to %AppData%\Microsoft\Network\Connections\Cm*yourGuid\routes.txt (C:\Users\userID\AppData\Roaming\Microsoft\Network\Connections\Cm*VPNGuid*\routes.txt)* in your client machine and add the route in this text file.
Please refer : https://learn.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-about-point-to-site-routing#vnetbranchbgp
Kindly let us know if the above helps or you need further assistance on this issue.
----------------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.