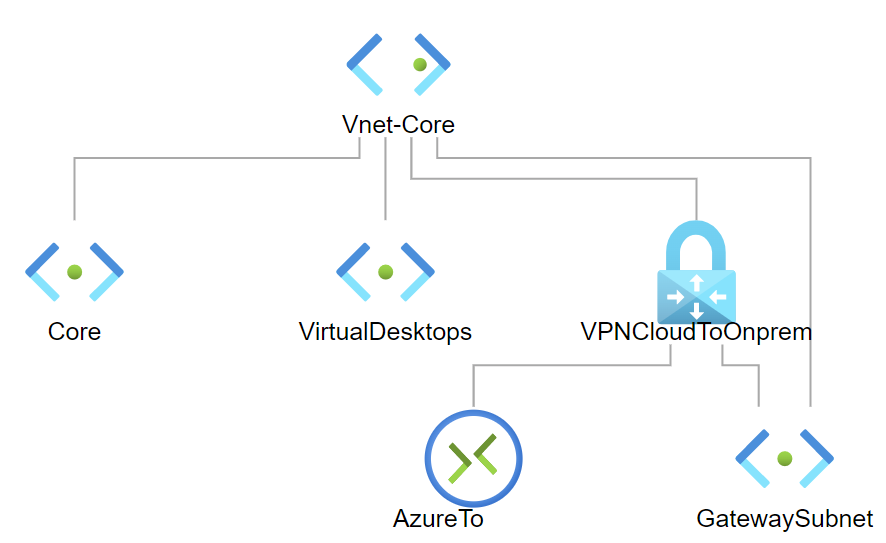
I have a single VNet in Azure with the address space 10.2.0.0/16
It has 3 subnets,
GatewaySubnet: 10.2.2.0/28
Core: 10.2.1.0/24
VirtualDesktops: 10.2.3.0/24
I have an on prem network that is connected with a S2S VPN using a route based virtual network gateway. The on prem network has an address space of 10.0.0.0/24 with a static route for all addresses in 10.2.0.0/16 to be sent over the VPN
If I create a VM in the Core subnet, I can RDP to it with its private IP address from my on prem system no problem. If I move that same VM into the VirtualDesktops subnet, I can't connect to it. If I spin up a new VM in that subnet I can't connect to it.
There are no NSGs stopping traffic. I even created one that allows everything from 10.0.0.0/24 to 10.2.3.0/24 in case something was being blocked.
I thought that all subnets could communicate with each other by default. Is there something I'm missing to communicate with the VirtualDesktops subnet?
Thanks