Hello,
we deploy autopilot machines with standard users(not local adminsitrators), Intune only and everything is in Azure AD.
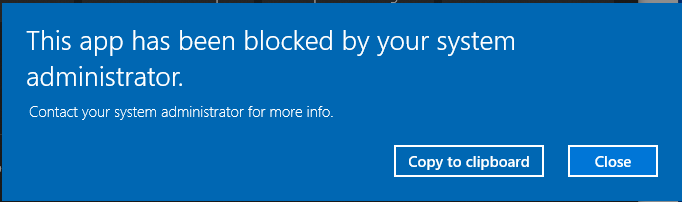
When user has to install something UAC secure desktop prompts for credentials. I would like to disable secure desktop and then user will be able to do copy/paste of local admin password.
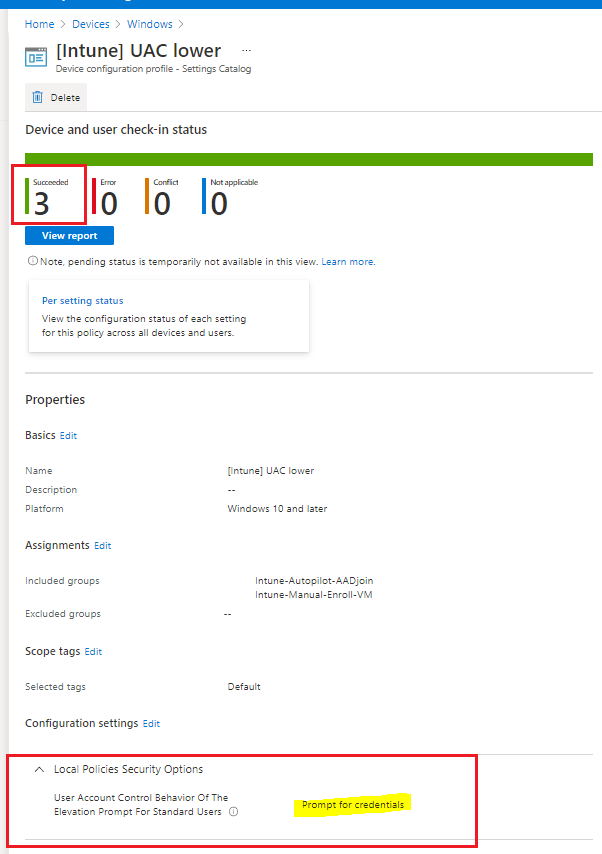
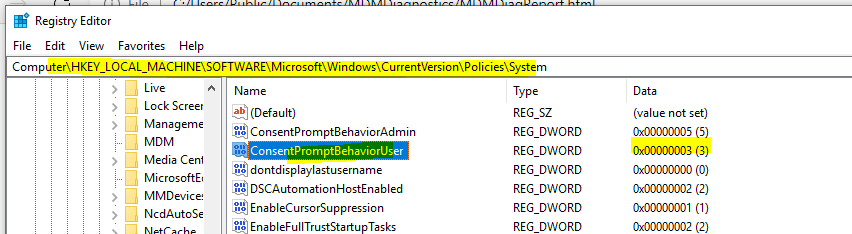
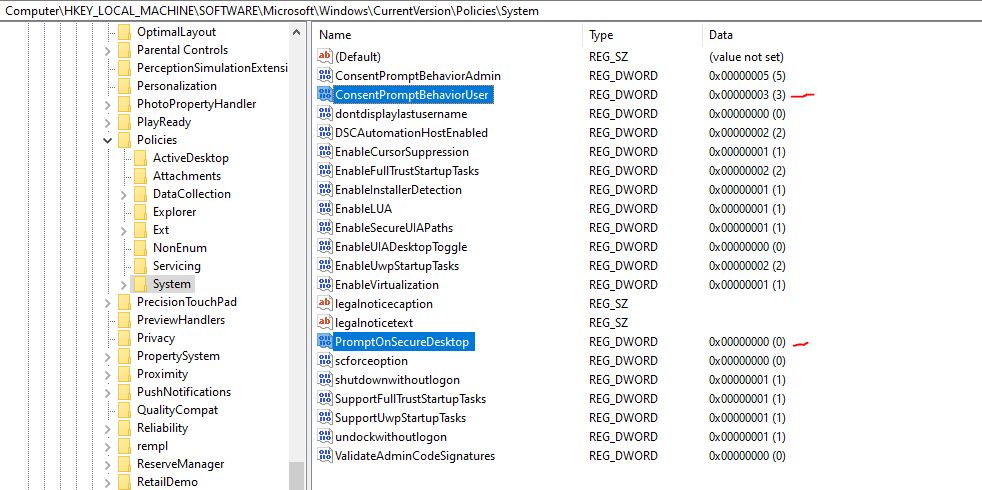
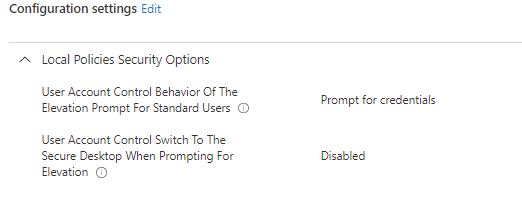
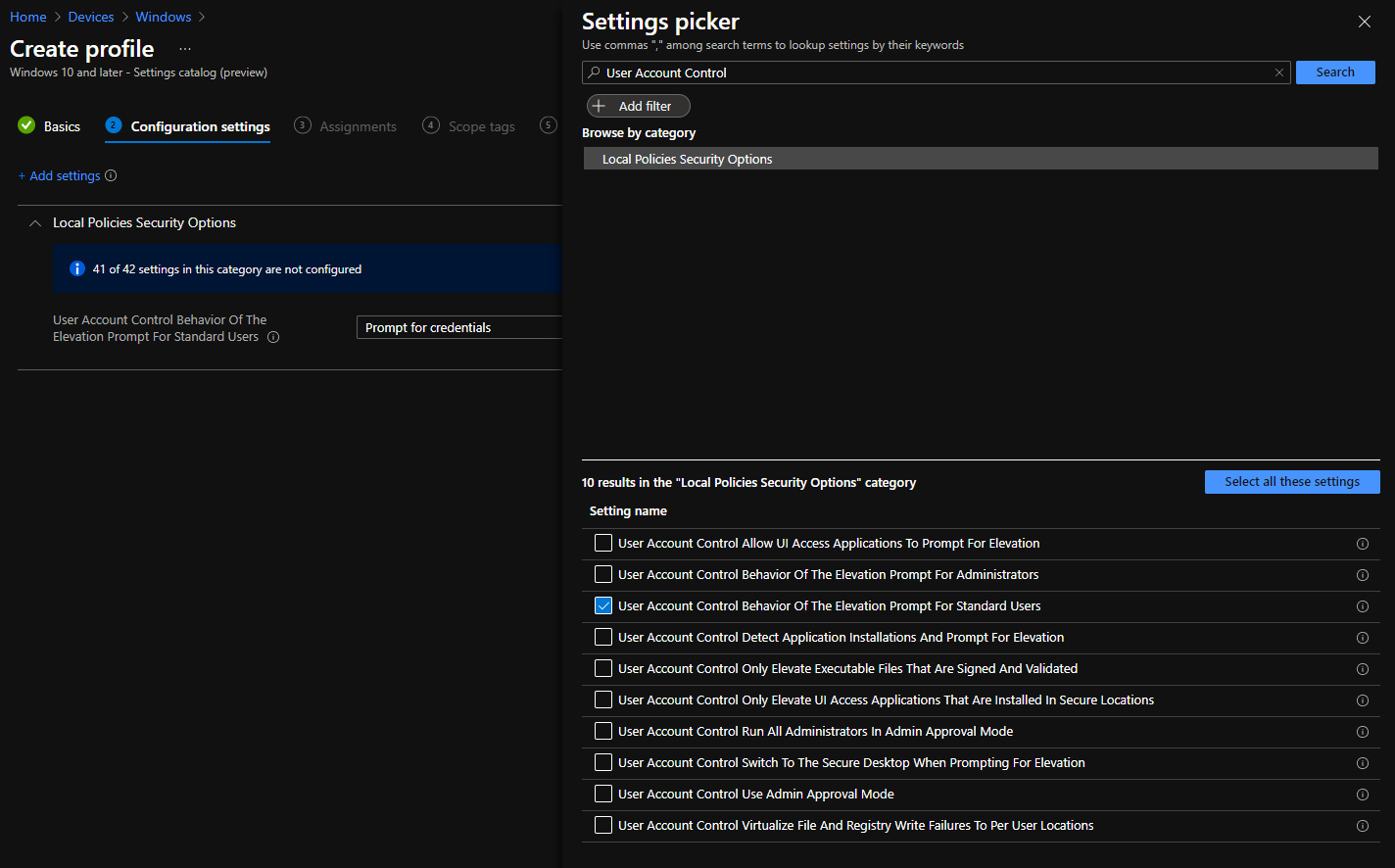
I am trying to disable secure desktop in UAC using custom configuration profile with these settings:
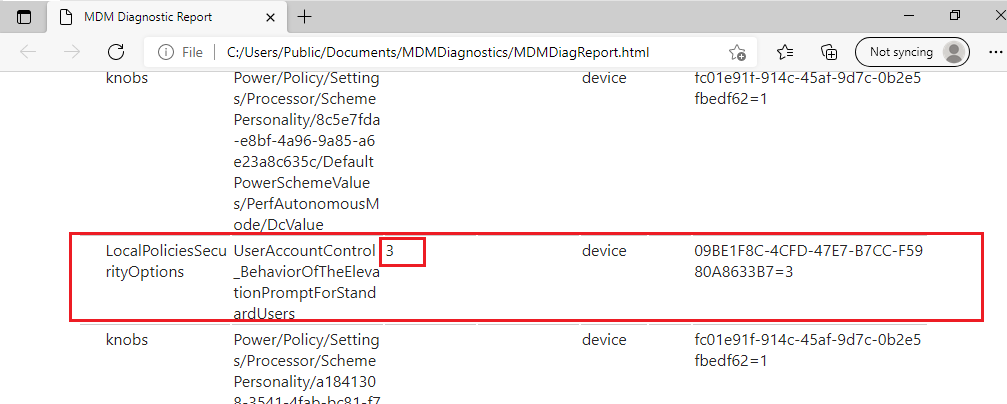
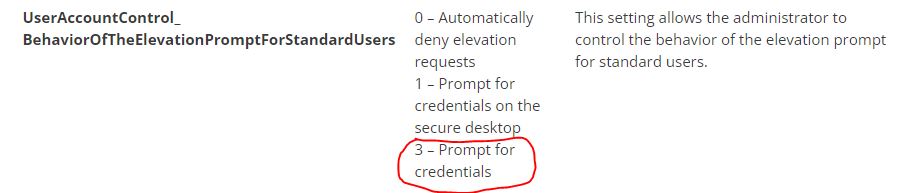
OMA-URI: ./Device/Vendor/MSFT/Policy/Config/LocalPoliciesSecurityOptions/UserAccountControl_BehaviorOfTheElevationPromptForStandardUsers
Data type: Integer
Value: 3
https://www.petervanderwoude.nl/post/managing-user-account-control-settings-via-windows-10-mdm/
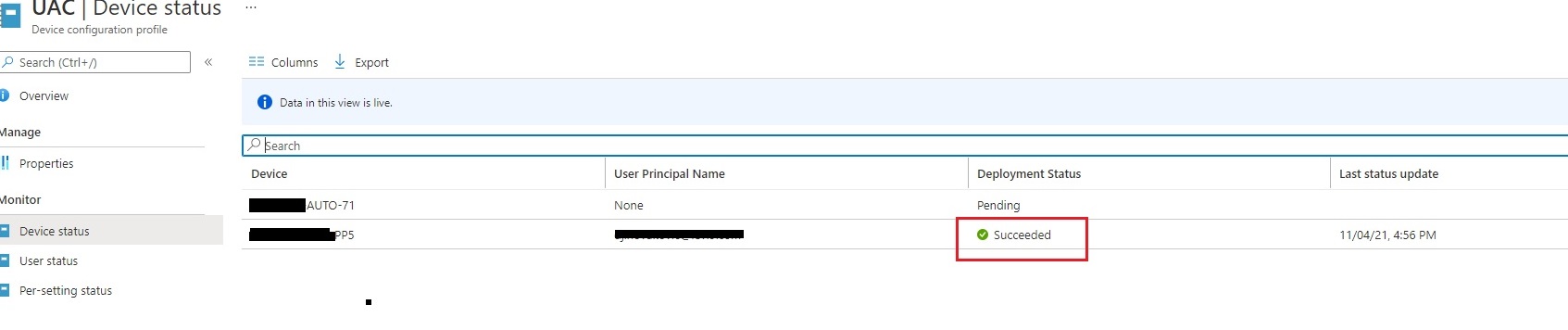
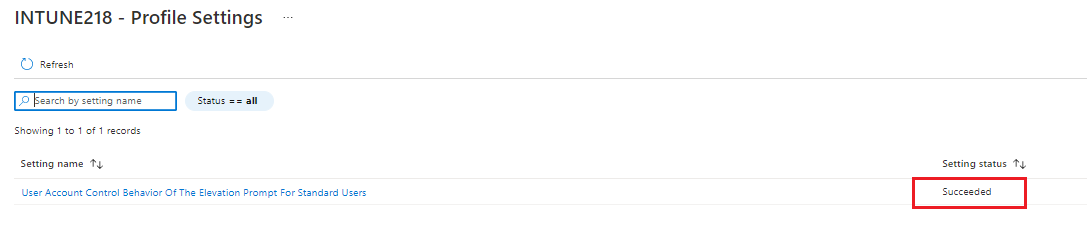
Configuration profile is applied successfully but this still does not work:
Is there anything else that I should configure?
Thanks