Thank you for the confirmation, @TXS-DEV .
Now I know the root cause of the issue. It is the VPN gateways deployed in both Vnets.
Traffic is not transiting your peered VNet because of the VPN gateways deployed in both VNets. Traffic will transit a peered Vnet if only one of the VNet has VPN gateway deployed.
You can configure the gateway in the peered virtual network as a transit point to an on-premises network, but the virtual network that is using a remote gateway can't have its own gateway.
Reference : https://learn.microsoft.com/en-us/azure/virtual-network/virtual-network-peering-overview#gateways-and-on-premises-connectivity
To resolve this issue, I would advise you to follow the below:
Either:
Delete the P2S VPN gateway from Virutal Network#2.
Configure P2S on the existing VPN gateway of Virutal Network#1.
Peer Virutal Network#1 & Virutal Network#2 and then use the transit gateway feature in the Vnet peering between both Vnets to access both Vnets from the P2S clients by re-downloading the XML file.
Refer : https://learn.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-about-point-to-site-routing#multipeered
OR:
Disable the Vnet peering and create a site-to-site (IPsec) connection between the two VPN gateways.
Refer : https://learn.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-howto-vnet-vnet-resource-manager-portal#site-to-site-ipsec
The local network that is connected to Virutal Network#1 must contain both the Vnet range of Virutal Network#2 and the Point to Site range (address pool range) of VPN clients.
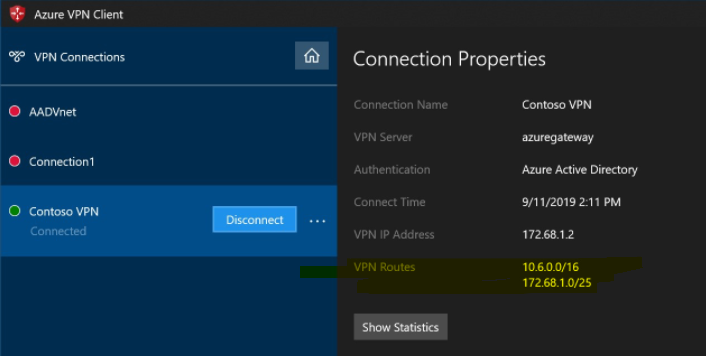
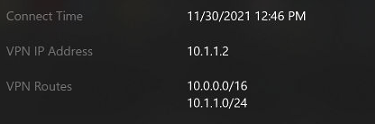
The point to site client must be injected with a proper route for Virutal Network#1, as by default the VPN package will only provide a route for Virutal Network#2.
You can leverage the Add-VpnConnectionRoute powershell cmdlet to add the route for Virutal Network#1.
Refer : https://learn.microsoft.com/en-us/powershell/module/vpnclient/add-vpnconnectionroute?view=windowsserver2019-ps
Kindly let us know if the above helps or you need further assistance on this issue.
----------------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.