Hi,
We tried this in first attempt and it's still not working. User can read folder, but cannot write (from pc with department=IT).
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Hello all,
I have "simple" problem and DAC is simple solution for me. I have security group with users that can access certain folder on our FS (servers 2019). But they should be able to access mentioned folder ONLY from ONE or TWO workstations (win10 or server 2019)
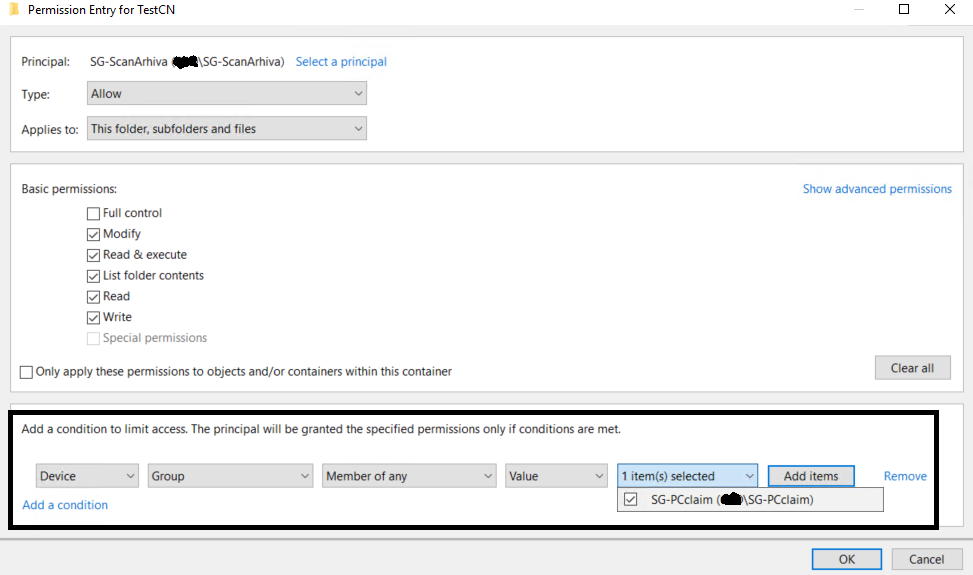
Picture above represents NTFS permissions I want...and adding DEVICE claim should do the work. But DEVICE CLAIMS are NOT working. USER CLAIMS work.
1.GPO "kerberos armoring" for domain controllers (all 2016) is in place.
2.GPO "Kerberos client support for claims" is in place for needed workstations (win10)
SG-scanarhiva contains users, SG-PCclaim contains workstations from witch SG-scanarhiva should access folder testCN.
Like i mentioned user claims work. I created new "Claim type" in ADAC and tested it with department atribute. All users having for example "IT" string in department field can access folder. Users without cannot.
When i type "whoami /claims" i cmd i can clearly see claims for particular user.
Problem is whatever combination I try with DEVICE CLAIM, with any attribute (CN, department...etc) folder does not give NTFS access.
But if I test it in "effective access" looks like I should have permissions.
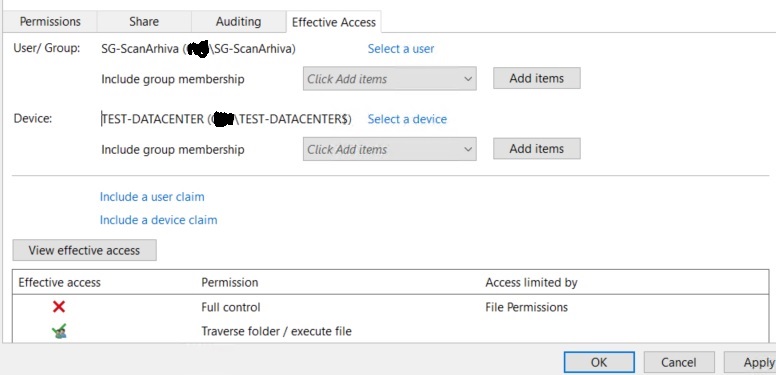
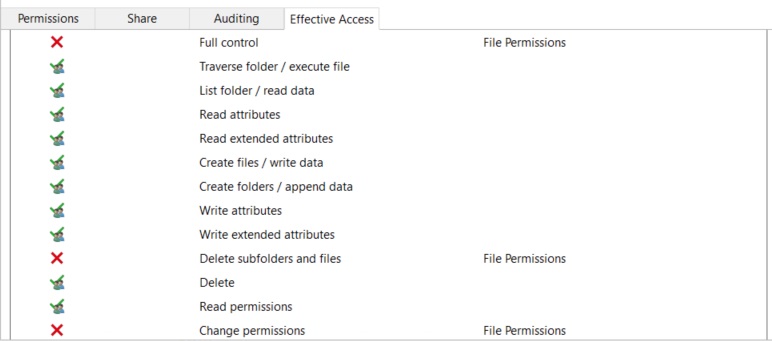
I really don't know how to troubleshoot Device claims... What is the difference between device and user claims?? Can you help me and point me to right direction ??
Additionally, i tried to make device claims based on department, CN and location... (same way like i do for users and for users it works). But with devices, No luck..
And I want't to check device claims by runing: New-Object System.Security.Principal.WindowsIdentity("PC$@keyman .local")
result is:
DeviceClaims : {}
Hi,
We tried this in first attempt and it's still not working. User can read folder, but cannot write (from pc with department=IT).

Are there any news on this issue? I have exactly the same problem.
DC: Windows Server 2019
File Server: Windows Server 2022
Client: Windows 11 22H2 or Windows 10 21H1
All with latest updates.
I added a claim type department for both, user and computer mapped to the department property of AD. I provided the value Research for the department property of both, the user and the client computer. The KDC support for claims is enabled and set to Supported for the DC. Kerberos client support for claims is enabled for the clients, but (see below).
On a folder, I granted Users the permission Modify. As condition, I set User.department Equals "Research".
Result: Access is granted.
Comment: This test proves that claims based access works.
On the same folder I set the condition to User.department Equals "Research" AND Device.department Equals "Research"
Result: Access is denied.
Comment: This should work.
I disabled the group policy with the setting Kerberos client support for claims. The condition is restored to User.department Equals "Research".
Result: Access is granted.
Comment: Based on most documentation, this should not work. It seems, that this setting only applies to services running in computer account context.
$identity = New-Object System.Security.Principal.WindowsIdentity('claire@ad.adatum.com')
$identity.UserClaims
With disabled Kerberos client support for claims this does not return the claim for the department. However, whoami /claims shows the claim with the message Kerberos support for Dynamic Access Control on this device has been disabled.
With enabled Kerberos client support for claims I see the claim:
ad://ext/department:88daac6779977a9a Research
$identity.Claims returns the same results.
$identity.DeviceClaims is empty. Shouln't there be a claim?
$identity = New-Object System.Security.Principal.WindowsIdentity('cl2$@ad.adatum.com')
$identity.UserClaims
$identity. Claims
$identity.DeviceClaims
These calls return the same results as for the user identity.
It seems that DeviceClaims never gets populated and therefore the test scenario does not work.
I've same issue and made same tests as you all .....
I'm still not able to deal with computer's claims ...
At least, I would like to deny access to any computers which is not domain joined (ie : to prevent personal computer, network connected, to reach my file servers, using AD account to auth)
Does anyone had a chance to have computer filtering in DAC working ?
Thks,
I have the same issue. I can only set claims for user, but device claims does not work. Is there anyone who has got the solution? for test i set the condition to devices, there are have member of domain computers, but does not work. i had reboot client, gpupdate, and login, but without success.
Is it possible to check device claims like user claims (whoami /claims) ?
hopeful
yve1701