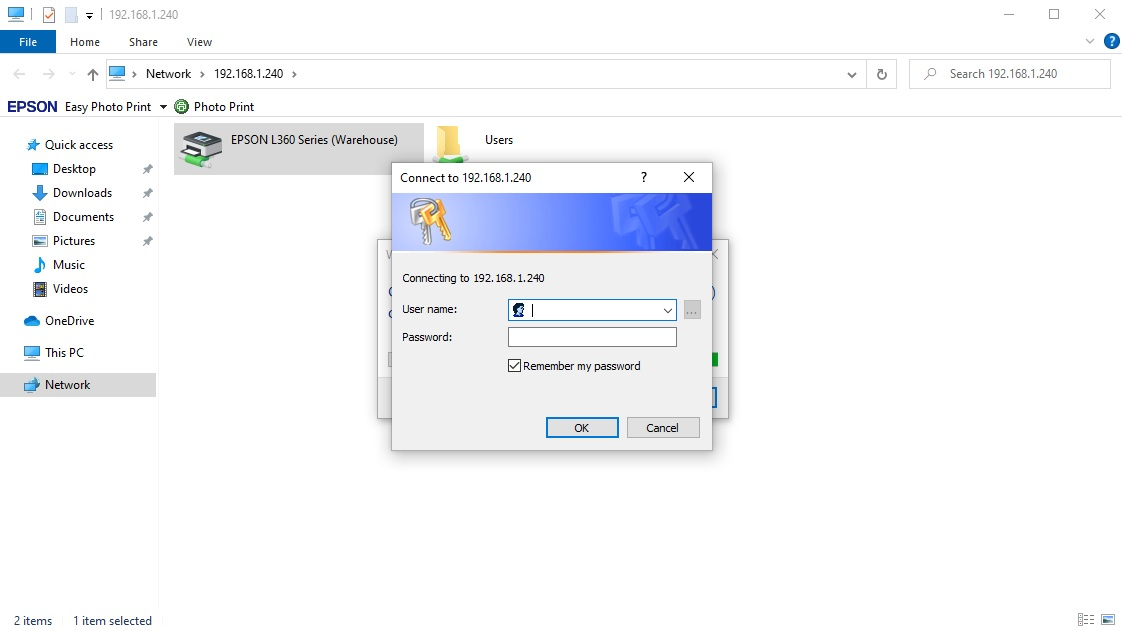
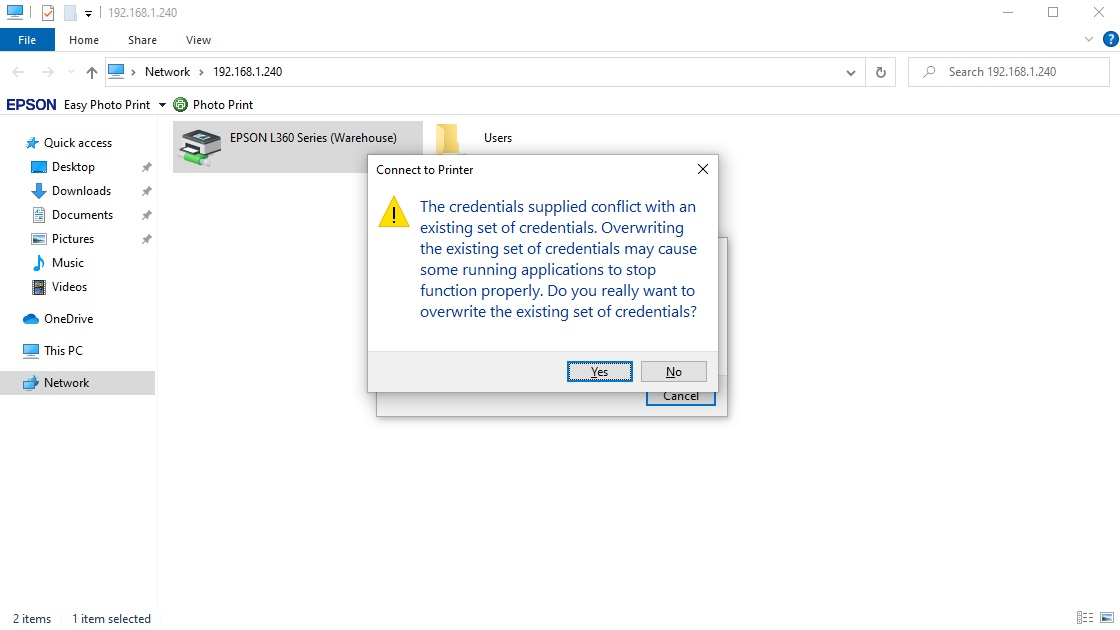
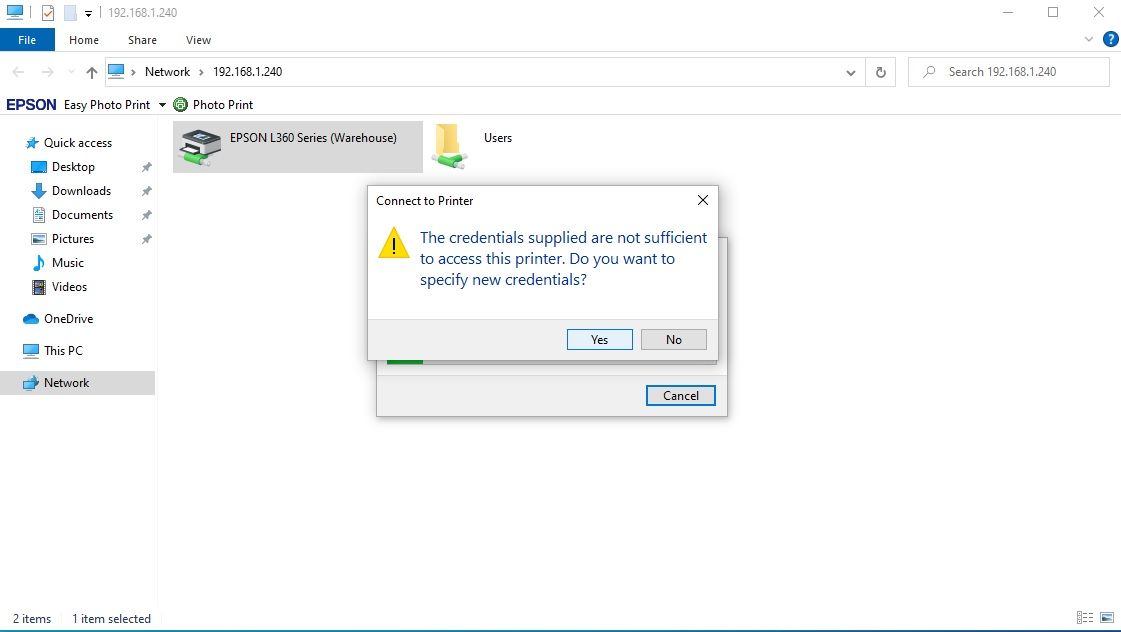
Hi @Norell
By default, non-admin domain users do not have permission to install the printer drivers on domain computers. To install a driver, the user should have local admin privileges (must be a member of the local Administrators group).
You can use Group Policy to allow users permission to install printers
Create a new (or edit an existing) GPO object (policy) and link it to the OU (AD container), which contains the computers on which is necessary to allow users to install printer drivers (use the gpmc.msc snap-in to manage domain GPOs). You can implement the same settings on a standalone (non-domain) computer using the Local Group Policy Editor (gpedit.msc).
Expand the following branch in the Group Policy editor: Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options. Find the policy Devices: Prevent users from installing printer drivers.
Set the policy value to Disable. This policy allows non-administrators to install printer drivers when connecting a shared network printer (the printer’s driver downloaded from the print-server host). Then you can set the policy value to Disable, any unprivileged user can install a printer driver as a part of a shared printer connection to a computer. However, this policy does not allow downloading and installing an untrusted (not-signed) printer driver.
The next step is to allow the user to install the printer drivers via GPO. In this case, we are interested in the policy Allow non-administrators to install drivers for these device setup classes in the GPO section Computer Configuration > Policies > Administrative Templates > System > Driver Installation.
Enable the policy and specify the device classes that users should be allowed to install. Click the Show button and in the appeared window add two lines with device class GUID corresponding to printers:
Class = Printer {4658ee7e-f050-11d1-b6bd-00c04fa372a7};
Class = PNPPrinters {4d36e979-e325-11ce-bfc1-08002be10318}.
You can find a full list of the device class GUIDs in Windows here.
When you enable this policy, members of the local Users group can install a new device driver for any device that matches the specified device classes.
Note. You can enable this policy through the registry using the command:
reg add "HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\DriverInstall\Restrictions" /v AllowUserDeviceClasses /t REG_DWORD/d 1 /f
You can find the list of allowed to install device GUIDs under the registry key: HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\DriverInstall\Restrictions\AllowUserDeviceClasses.
Now save the policy.
I hope this answers your question.
Thanks.
--
--If the reply is helpful, please Upvote and Accept as answer--