@Tagvor Hovsepyan
Thank you for your post!
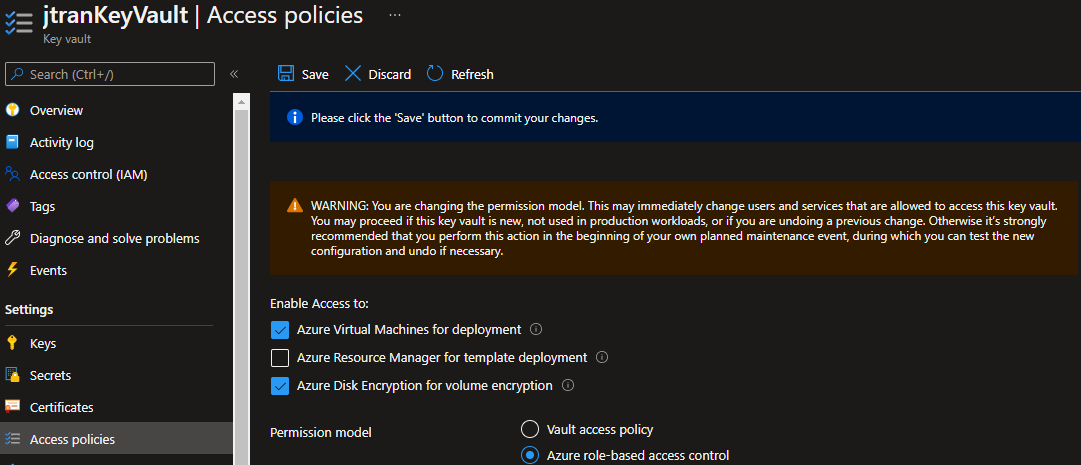
When it comes to providing Key Vault access to a specific group of users for only one Secret, this is only possible with the Azure Key Vault's RBAC permission model. The Azure RBAC model provides the ability to set permissions on different scope levels: management group, subscription, resource group, or individual resources. Azure RBAC for key vault also provides the ability to have separate permissions on individual keys, secrets, and certificates.
Using Azure RBAC secret, key, and certificate permissions with Key Vault:
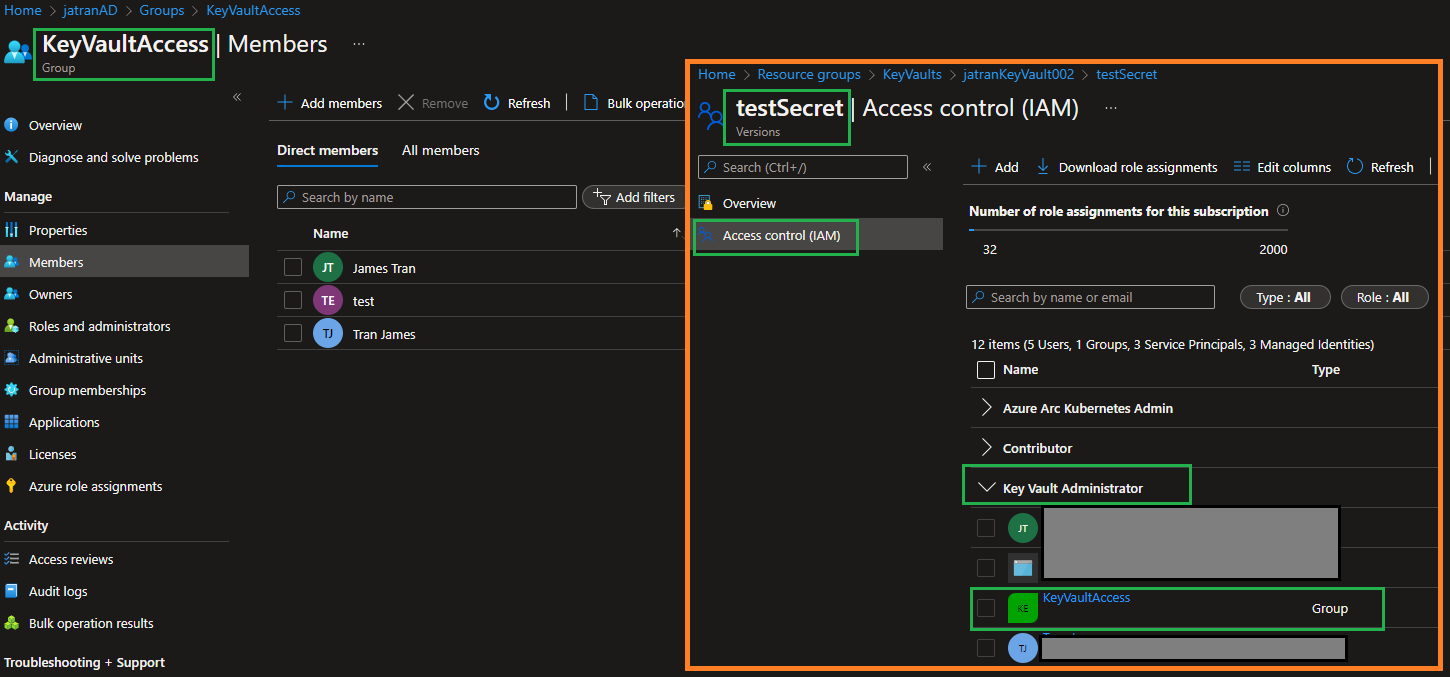
- Go to your
Key Vault->Open the Secretyou'll to be using -> Select theAccess control (IAM)tab - Select
Add->Add role assignmentto open the Add role assignment page. - Assign the needed built-in role for the Group
Additional Link:
Secret scope role assignment
Known limits and performance
If you have any other questions, please let me know.
Thank you for your time and patience throughout this issue.
----------
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.