Hi @Surinder Singh ,
Thanks for reaching out.
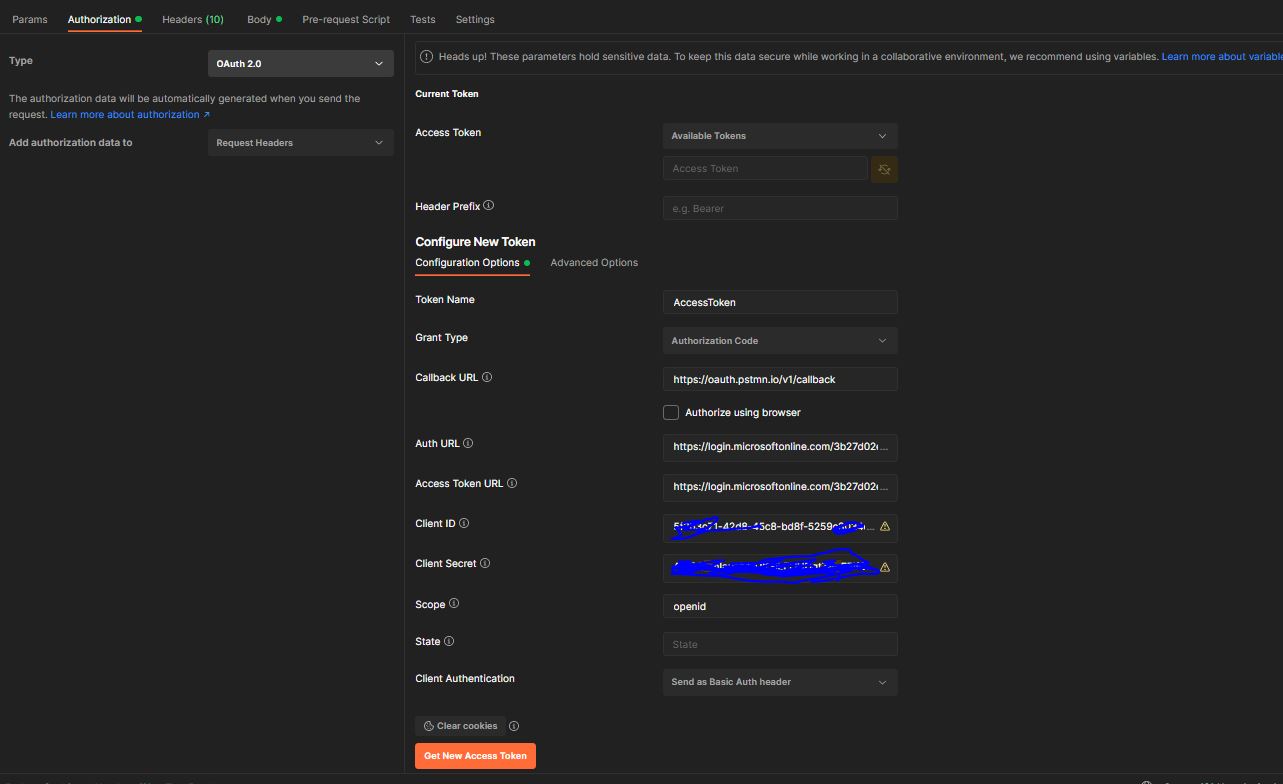
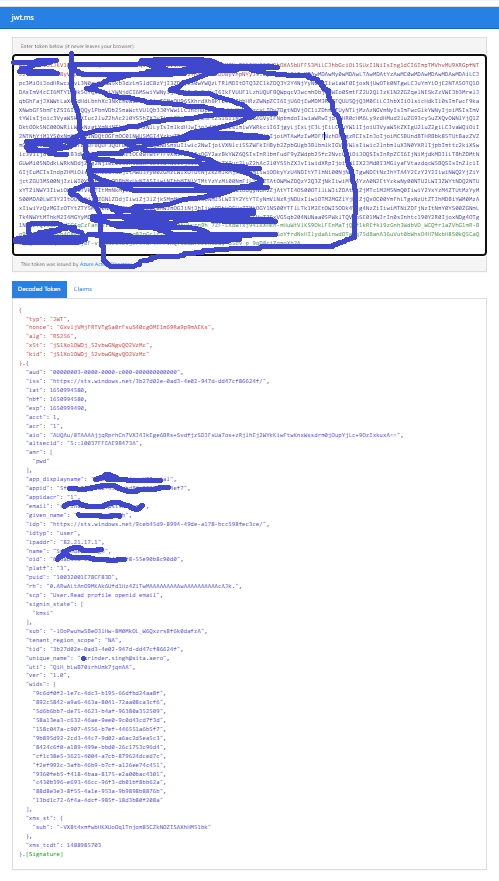
I understand you are not getting "oid claim" when you are retrieving the access token using postman.
As mentioned in your screenshot, only scope requested by you is openid. To get the "oid claim" in the access token, will also need to request for profile scope.
As documented here,
"Because the oid allows multiple apps to correlate principals, the profile scope is required in order to receive this claim for users."
Also, there might be chance you are passing profile scope in your application and missed the same in postman due to which you are getting different results.
Hope this will help.
Please remember to "Accept Answer" if answer helped you.
Thanks,
Shweta