Hi NormanJ-8524,
Thanks for reaching out.
I understood that users are forced to reauthenticate in the application every 30 days as conditional policy of 30 days has been setup in sign-in frequency as below
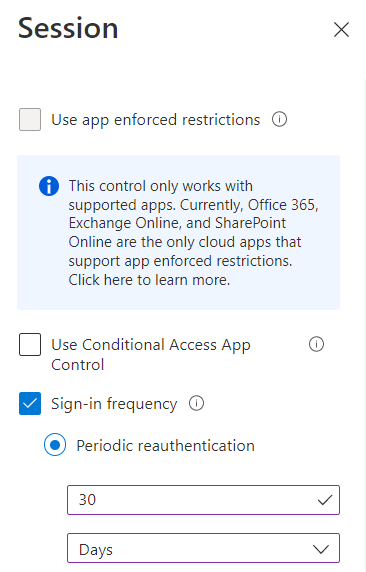
This is the expected behavior for sign-in frequency if periodic reauthentication has been setup 30 days.
As per info, The Azure AD default configuration for user sign-in frequency is a rolling window of 90 days but we can apply sign-in frequency conditional policy to asked the users to sign in again after the period which is define in "Periodic reauthentication".
In case users need to reauthenticate after 90 days, there is no need to set sign in frequency conditional policy as this is default Azure AD behavior.
To disable sign-in frequency to rollout every 30 days, unchecked the "Sign-in frequency" and do not configure any session control.
Hope this will help.
Thanks,
Shweta
Please remember to "Accept Answer" if answer helped you.