Hello @Oldrich Srubar ,
Apologies for the delay in response.
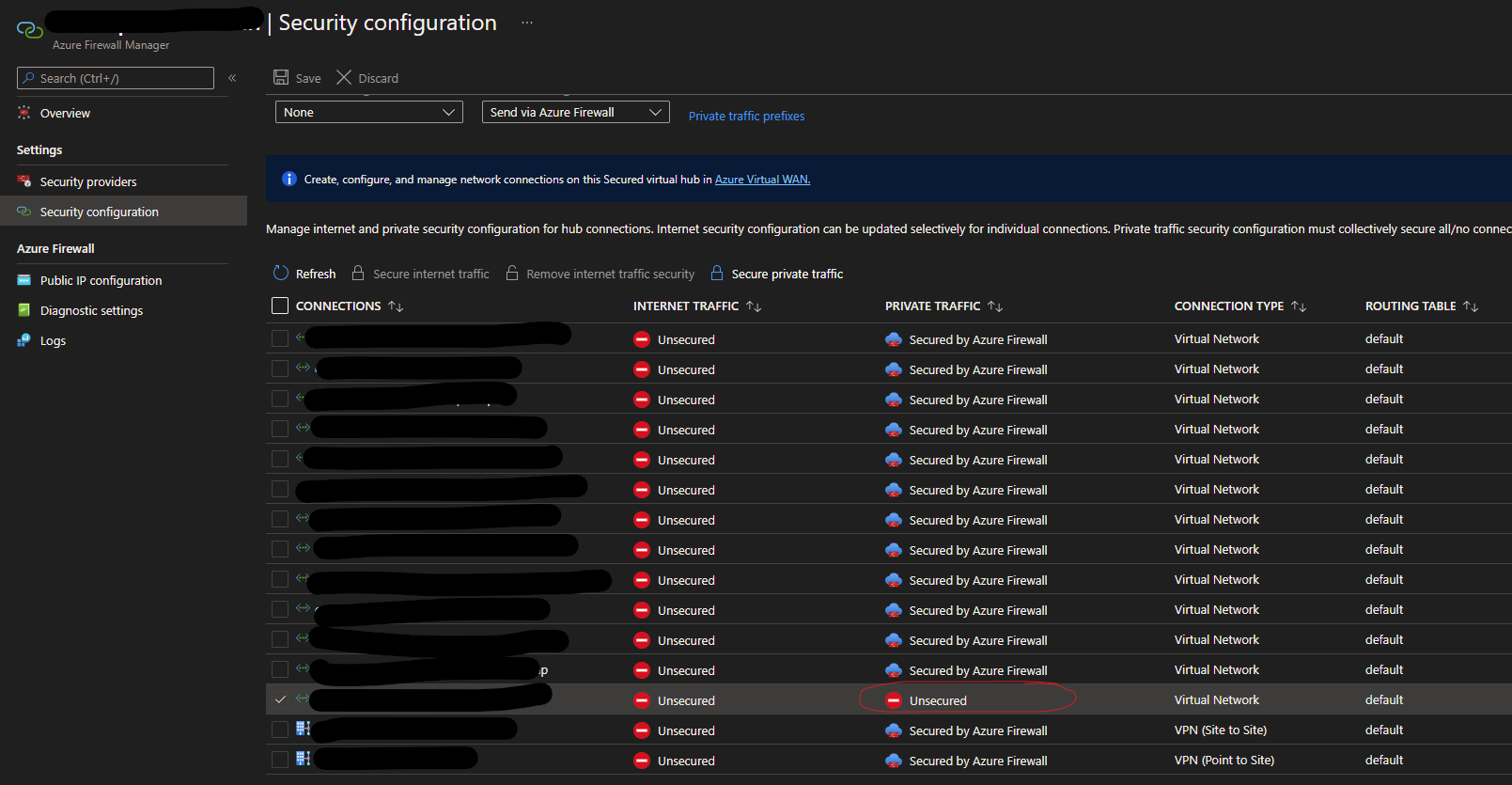
I understand that you are unable to configure inspection of private traffic via Azure Firewall in Security configuration deployed in your secured hub for the cross tenant peered Vnet.
I reproduced this issue in my lab and found that this is happening because Propogate RT was set to default in the cross tenant Vnet connection which was bypassing the Azure firewall from virtual hub to the spoke vnet.
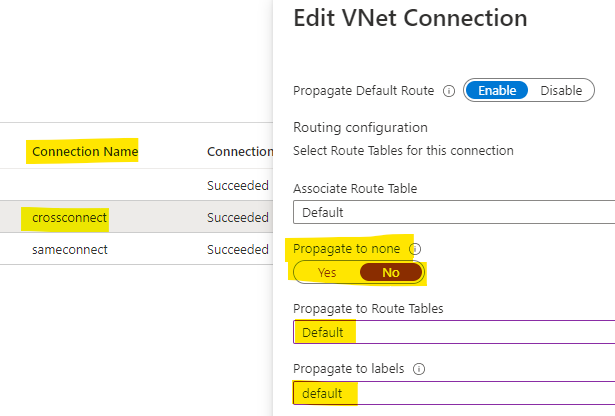
I tried setting "Propagate to None" as Yes in the cross tenant Vnet connection but it failed with permission error as below:
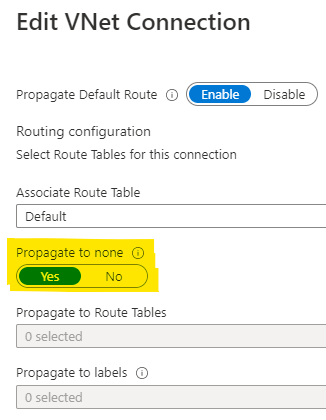
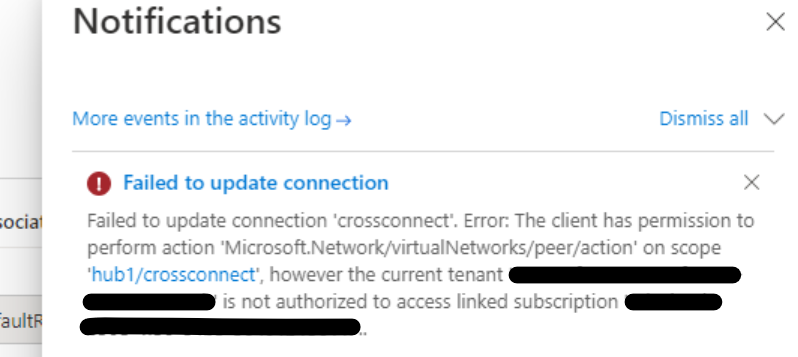
So, I deleted the cross tenant Vnet connection from portal and created the cross tenant vnet connection again via Azure PowerShell using the "-RoutingConfiguration" parameter as below:
When connected to the remote/spoke subscription account:
$remote = Get-AzVirtualNetwork -Name "remotevnet" -ResourceGroupName "remoterg"
When connected to the parent/hub subscription account:
$rt1 = Get-AzVHubRouteTable -ResourceGroupName "rg1" -VirtualHubName "hub1" -Name "defaultRouteTable"
$rt2 = Get-AzVHubRouteTable -ResourceGroupName "rg1" -VirtualHubName "hub1" -Name "noneRouteTable"
$routingconfig = New-AzRoutingConfiguration -AssociatedRouteTable $rt1.Id -Label @("none") -Id @($rt2.Id)
New-AzVirtualHubVnetConnection -ResourceGroupName "rg1" -VirtualHubName "hub1" -Name "crossconnect" -RemoteVirtualNetwork $remote -RoutingConfiguration $routingconfig
The above commands created the cross tenant vnet connection with Propagate to None option set as Yes and when I checked the Security configuration deployed in my secured hub, I could see the cross tenant Vnet secured via Azure Firewall.
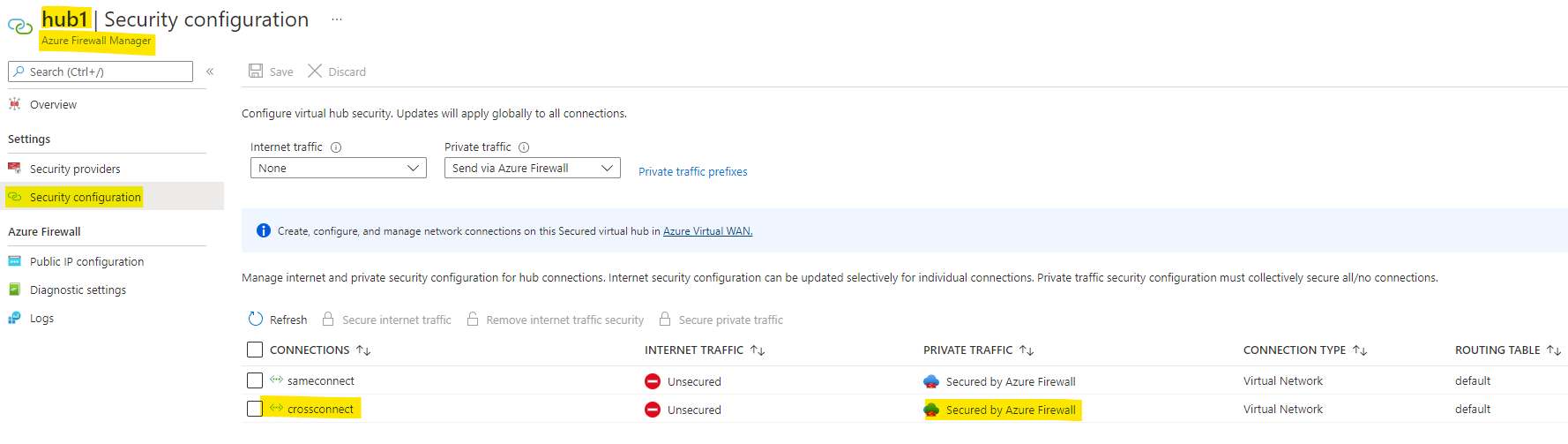
Kindly let us know if the above helps or you need further assistance on this issue.
----------------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.