Hi @Gurudas • Thank you for reaching out.
As PowerShell and GUI both update the same attributes, it is not possible to distinguish whether MFA registration on a user account was done via Powershell or GUI.
You can use the below PowerShell command to get a list of users with MFA Enabled/Disabled:
Connect-MsolService
Get-MsolUser -All | select DisplayName,BlockCredential,UserPrincipalName,@{N="MFA Status"; E={ if( $_.StrongAuthenticationRequirements.State -ne $null){ $_.StrongAuthenticationRequirements.State} else { "Disabled"}}}
If MFA is enabled and still not working, you can use the below options:
- Navigate to Azure AD > Users > Click on the user account that you want to re-provision MFA for > Authentication methods > Require re-register MFA.
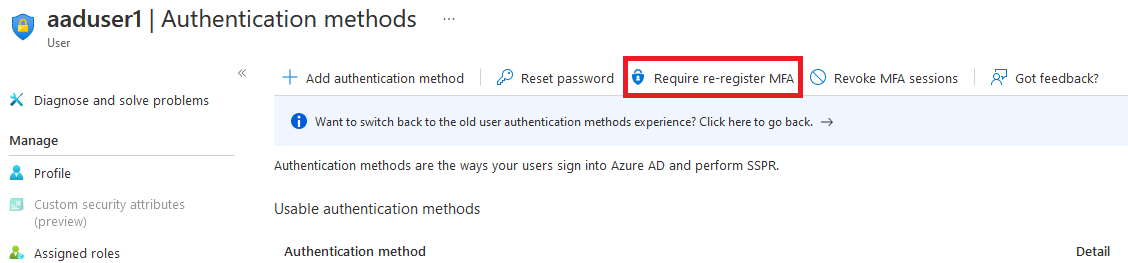
- Run the below PowerShell cmdlets:
Connect-MsolService
Set-MsolUser -UserPrincipalName username@your_tenant.onmicrosoft.com -StrongAuthenticationMethods @()
Below is the list of services/settings that can be used to require MFA Registration for a user:
- Conditional Access Policy (https://learn.microsoft.com/en-us/azure/active-directory/conditional-access/howto-conditional-access-policy-all-users-mfa)
- Azure AD Identity Protection (https://learn.microsoft.com/en-us/azure/active-directory/identity-protection/howto-identity-protection-configure-mfa-policy)
- Security Defaults (https://learn.microsoft.com/en-us/azure/active-directory/fundamentals/concept-fundamentals-security-defaults)
- Per-user MFA (https://learn.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-userstates)
-----------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.



