@Alfred , From your description, it seems some clients get both SCCM and Intune Endpoint protection settings when we transfer the workload in Intune. if there's any misunderstanding, feel free to let us know.
Based as i know, when we switch the Endpoint Protection workload to Intune. the Configuration Manager policies stay on the device until the Intune policies overwrite them. This behavior makes sure that the device still has protection policies during the transition.
https://learn.microsoft.com/en-us/mem/configmgr/comanage/workloads#endpoint-protection
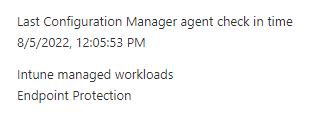
For our issue, please firstly check on affected device on Intune side to see if the "Endpoint Protection" is under "Intune managed workloads".
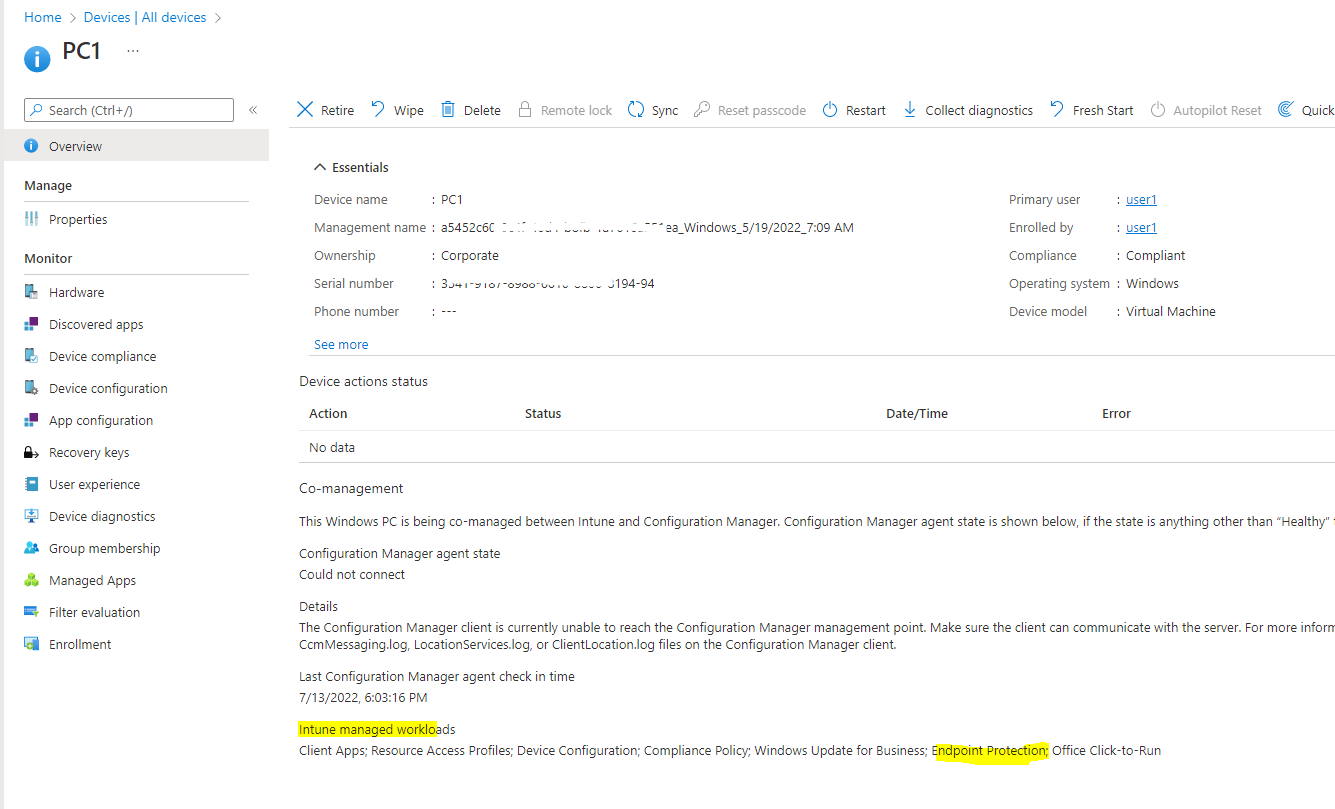
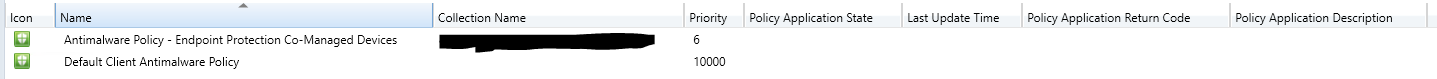
Meanwhile, go to Intune endpoint security policies and verify if the policy has applied successfully to the affected device. Please get a screen shot.
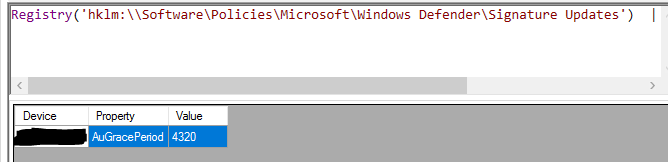
In addition, for the setting "Manage endpoint protection client on client computers", based on my understanding, when it is set as no. it will not managed by Configuration manager. So I think we can try it
https://learn.microsoft.com/en-us/mem/configmgr/core/clients/deploy/about-client-settings#manage-endpoint-protection-client-on-client-computers
If there's any update, feel free to let us know.
If the answer is helpful, please click "Accept Answer" and kindly upvote it. If you have extra questions about this answer, please click "Comment".
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.