Single Sign Out–WebSSO
While reviewing all the existing samples we’ve noticed that our implementation of Single Sign Out was kind of….weak. It wasn’t really fully implemented and wasn’t very clear what was happening either (or what it should happen)
We’ve fixed all that now in scenario 1: WebSSO. Things get more complicated when more than 1 STS is in the picture, and even more so when the identity provider uses other protocols (for example, all our scenarios using ACS and Google or ACS and LiveID). But for WebSSO, things are more or less straight forward.
WebSSO scenario recap:
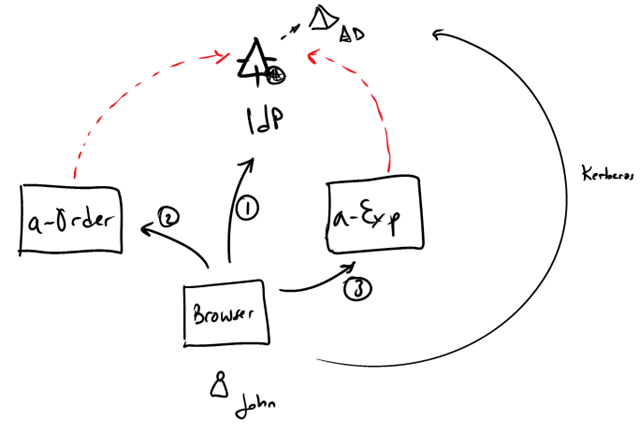
If you remember for previous posts or the book, in our first chapter we had Adatum with 2 applications: a-Order and a-Expense. We wanted that Adatum employees login to one or the other seamlessly:
- John opens the browser on his desktop (that already has a been authenticated with AD)
- Opens a-Order home page
- Gets redirected to the IdP. He’s authenticated (e.g. Kerberos ticket)
- A token is given to him. The token is posted back to a-Order. He’s in.
Sometime later, he browses a-Expense.
- No session with a-Expense yet, he’s redirected to IdP
- He’s already authenticated, gets a new token for a-Expense.
- Voila
So far, so good. Nothing really new. What happens now if John wants to signoff. We don’t want our system to be a roach motel: once in, never out… what happens is actually pretty straight forward, but there are some subtle considerations. When John signs-off, he should sign off from all relying parties and the IdP.
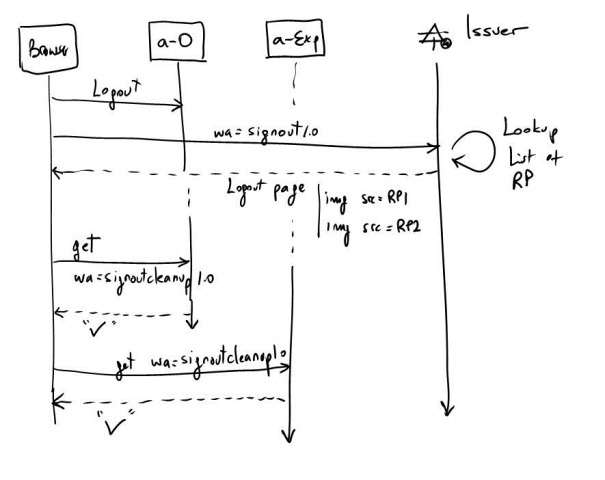
This diagram illustrates the process:
John clicks on “Logout” (on any of the relying parties: a-Order in our example). This results on a wa=signout1.0 to be sent to the IdP. The Idp cleans up its own session with the user and then (here comes the tricky part)returns a page to the user with a list of image tags (HTML image tags). An image tag for each RP the IdP has issued a security token for John. The src url for these images will be actually something like:
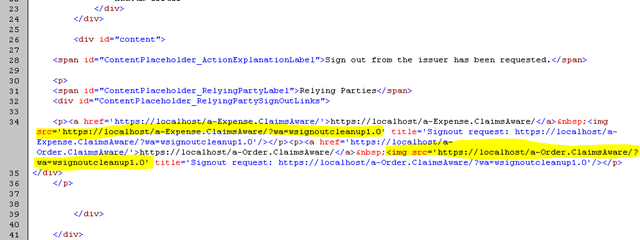
src=https://localhost/a-Expense/?wa=signoutcleanup1.0
src=https://localhost/a-Order/?wa=signoutcleanup1.0
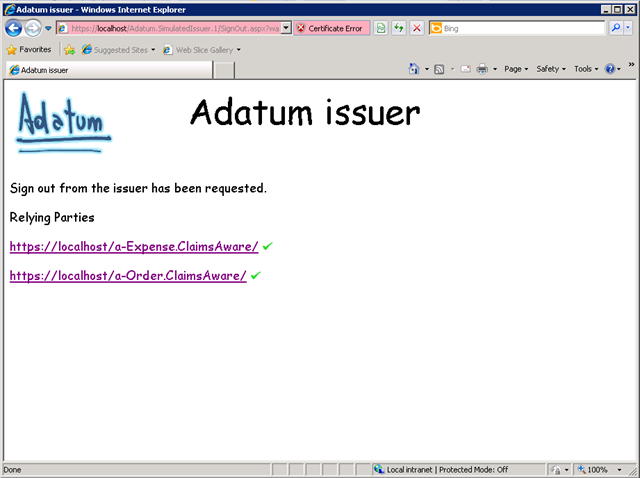
With these tags, the browser will attempt to get the image from these URL (which happens to be located in each RP: a-Order and a_expense), and in fact you will see something like this:
The HTML:
Where do these green checks images come from? There are nowhere in a-Order or in a-Expense… you would spend hours looking for the PNG, or JPG or GIF and you will never find it, because it is very well concealed. Can you guess where it comes from?
Hint: page 115 of Vittorio’s excellent book.
Bonus question: how does the IdP know all the applications the user accessed to?
By the way, all this is now working on the new updated samples which we will post to our CodePlex site very soon.