Understanding Zone Elevation
The security setting “Websites in less privileged web content zone can navigate into this zone”:
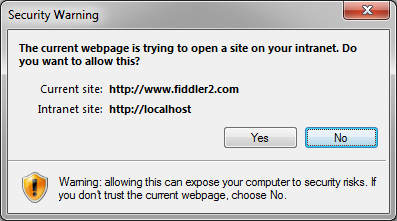
... is one that leads to more questions than almost any other. This setting, also known as Zone Elevation protection, was originally designed to prevent navigation from untrusted Internet content into the highly-trusted Local Machine Zone. Prior to Internet Explorer 6 on Windows XP SP2, if an attacker could accomplish such a navigation and inject script into the LMZ, they had found a Remote Code Execution vulnerability and could take over the machine. This was a key source of vulnerabilities in that era, and the threat led to the introduction of Zone Elevation protection.
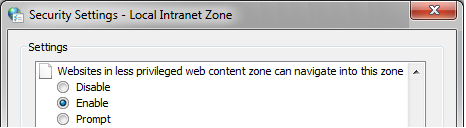
The Zone Elevation protection feature blocks navigation, either outright (when set to Disable) or via a Prompt:
Regardless of your specific security configuration, for the purposes of Zone Elevation checks, the privilege precedence of Zones is: Local Machine > (Local Intranet == Trusted Sites) > Internet > Restricted Sites. There's a special-case exemption in the logic that allows Trusted Sites to navigate to Intranet sites, even though normally Intranet > Trusted. (One reason for that is that the user may configure an Intranet Site to be a Trusted Site. Most people expect this to increase the site's level of privilege, despite the fact that the opposite is what happens by default, since the Intranet runs at the Medium-Low Security Template while the Trusted Zone defaults to the Medium Security Template. To help match users' expectations, the Trusted Zone is often afforded special exemptions like this one.)
You can explore the Zone Elevation prompt's behavior by adjusting the setting for the Intranet zone to Prompt, then visiting this test page: https://webdbg.com/test/zoneelevation.htm. This page attempts to load a frame at https://localhost, and offers various navigation-triggering methods as well.
In XP SP2, Zone Elevation protection was bolstered by the Local Machine Zone lockdown, such that Zone Elevation into the LMZ would be akin to “Breaking into Jail.” When an attacker Zone Elevates into the Local Machine Lockdown Zone, he ends up with fewer privileges, not more.
However, even after the Local Machine Zone lockdown was introduced, Zone Elevation protection still has some value in that it can prevent Internet Zone content from navigating into Trusted or Intranet Zone content. As such, when set to Prompt or Disable, it serves as a protection against XSS and CSRF attacks against content in those Zones. Without this protection, an attacker with knowledge of your Trusted/Intranet sites and their vulnerabilities could potentially execute a cross-zone attack against those pages from an Internet site. This attack is non-trivial to pull off (since it is, by its very nature, a targeted attack), and it isn’t nearly as scary as a pre-XPSP2 attack against LMZ.
By default, all Zones have their Zone Elevation setting set to Allow except the Local Machine and Restricted Zones, where it is set to Disable. That setting is meaningless for the Restricted Zone because there is no less trusted Zone. It’s set that way because Disable is the default for the High Security template which may be used by other zones. If a Zone’s security level is set to the Low template, then the Zone Elevation URLAction is set to Prompt because this high level of privilege allows download of signed ActiveX controls and one-click access to scripting ActiveX controls that are not marked safe-for-scripting.
Configuring Zone Elevation to prompt or disable access to your Local Intranet and Trusted Sites zones can help protect against CSRF and XSS.
In IE10 Metro Mode, the Private Network Isolation feature more effectively enforces protection of the “Intranet,” as it prevents circumvention of cross-Zone restrictions using the site’s IP address or otherwise causing IE to Zone a “private network” site into the Internet zone.
-Eric