Configure DNS Dynamic Update Credentials for DHCP with PowerShell
It's an old story... client meets network, client falls in love obtains IP address from DHCP server, DHCP server registers DNS record on behalf of client...
Ah, so romantic!
But.. have you ever wondered how the DHCP server registers the client's DNS record? No? Where's your sense of adventure!
Background
Here's the context. As you may have gathered, the DHCP server is able to register PTR and A records on behalf of clients. There are a few ways to achieve this. To perform the DNS updates in a secure manner and to ensure that stale resource records are avoided, we recommend configuring the DHCP server to use a standard Active Directory user account, i.e. non-privileged, to perform the updates. The same account can be used across a number of DHCP servers. In summary, you'll need to create a dedicated account and configure the DHCP server with its credentials in the following circumstances:
- The DHCP server is configured to perform dynamic updates on behalf of clients (see below)
- The DNS zones to be update are configured to only allow secure dynamic updates, e.g. Active Directory integrated
I want to achieve the configuration shown in the following screen-shots...
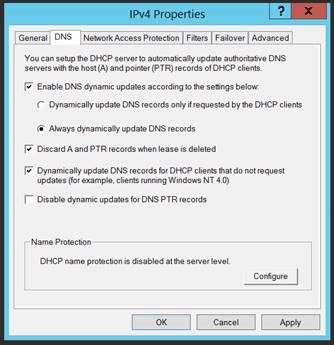
Figure 1 - Example DNS Related Settings (IPv4 Properties / DNS)
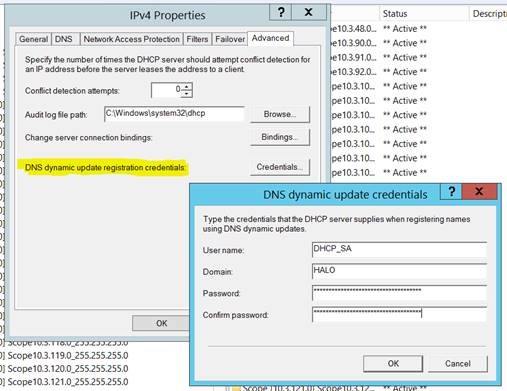
Figure 2 - Example DNS Dynamic Update Credentials (IPv4 Properties / Advanced / Credentials)
Over to PowerShell...
PowerShell
Here's a hash table of values to be splatted to the Set-DhcpServerv4Setting cmdlet. It reflects the settings in Figure 1.
#Set up values for Set-DhcpServerv4DnsSetting
$DnsSettings = @{
DynamicUpdates = "Always"
DeleteDnsRROnLeaseExpiry = $true
UpdateDnsRRForOlderClients = $true
DisableDnsPtrRRUpdate = $false
NameProtection = $false
}
Now, splat those settings to your DHCP servers.
#Splat values to Set-DhcpServerv4DnsSetting
Set-DhcpServerv4DnsSetting -ComputerName HALODC01 @DnsSettings
Set-DhcpServerv4DnsSetting -ComputerName HALODC02 @DnsSettings
Next, create the low-privileged user account. Make sure the password doesn't expire and set a complex password. Manage the account as per all your other service accounts. With the account created you can add it to each of your DHCP servers. You'll need to use Get-Credential first to temporarily store the credential.
#Add service account to DHCP
$Cred = Get-Credential
Set-DhcpServerDnsCredential -ComputerName HALODC01 -Credential $Cred
Set-DhcpServerDnsCredential -ComputerName HALODC02 -Credential $Cred
And, they all lived happily ever after...