Threat Analysis And Modeling (TAM) v3.0 – Learn about the New Features!
Last time we briefly talked about releasing TAM v3.0 this year. With each week we’re inching closer to that goal. TAM v3.0 release is focused on 3 main areas of the tool including:
- threat modeling methodology
- gathering application architecture
- security guidance
Apart from these import and export of items to and from threat model, threat generation were also significantly changed.
The following are the prominent new features in version 3.0.
- Cloud CTL – Common Task List (CTL) is a list of countermeasures. This rich structure allows the threat modeling tool to provide comprehensive and context sensitive security guidance. CTL is externally hosted on Azure as a WCF Service providing an easy way for external users to access the security guidance. In the near future, the WCF Service code will also be released so external organizations can take advantage and host their own service internally.

- Visio Drawing Surface – In v2.1, the use case generation can be a very tedious process. Although automatic use case generation feature existed, it did not provide logical break down of use cases. Manually adding calls one by one in large use cases involved remembering the previous callers and mapping appropriately. In v3.0, we replaced the graph in the use case edit screen with the Visio drawing surface where users can drag and drop roles and components to build a use case.
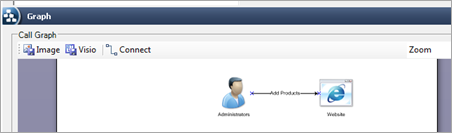
This Visio drawing surface reduces the number of clicks it takes to add a use case from 10 clicks to now just 6! The drag and drop drawing surface also helps you visualize while you are simultaneously adding calls. - Simplified ATG – Automatic Threat Generation (ATG) from v1.0 has been the best feature in the tool providing the user an easy way to generate threats. In v3.0 we’ve added a new feature called composite threats, read more about it here. It’s suffice to say that composite threats dramatically reduces the time it takes to evaluate threats. It combines calls with same the caller and component into one threat. Essentially you have multiple threats per call which reduces the number of threats and also allows the user to focus on the countermeasures of the affected components.
- Auto Updated Client – With this version users will be notified of the new release(s) and redirected to Microsoft.com download center to download the latest version. This ensures that users will always have the most up-to-date client installed.
- Backward Compatibility – V3.0 is completely backward compatible with v2.1 threat models. A new plug-in has been added in the import section for users to import v2.1 threat models. All of the data is imported including the countermeasures which are mapped automatically to the new CTL countermeasures.
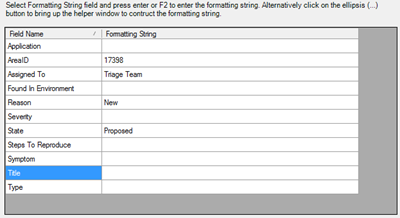
- Intelligent TFS Sync – TFS Export in v2.1 did not provide a way to consolidate countermeasures across multiple components. This new version includes complete TFS field mapper which provides a new UI to map TFS fields to CTL Fields allowing proper export across different TFS process templates. The exported work item references are stored in the threat model which helps users avoid exporting the same countermeasure twice.
- Leaner Threat modeling methodology – Items including identities, data effects, primary threat factors were removed. Service identities that are being used for specifying Component Run As and Call Impersonation Identity are now replaced with the Roles themselves. In v2.1 visibility to identities was not apparent which caused users not to create identities resulting in no mapping to the Run As property. Application Use Case data effect was used to identify the primary data effect of a single use case, but very often many calls in use case have multiple data effects. For example when creating a user, writing to a file log which has two data effects C –> User and C –> App Log. Now the use case data effects are completely removed, call data effects are consolidated to generate Data Access Control Matrix analytic. The primary threat factors were additional steps in understanding threats, however it was adding an extra step in evaluating threats.
Please continue to check out this blog site for release announcements and more updates on specific features.
Thanks
Anil