Authentication methods and identity providers for customers
Microsoft Entra External ID offers several options for authenticating users of your applications. You can let customers create an account in your customer directory using their email and either a password or an email one-time passcode. You can also enable sign-in with a social account.
Email and password sign-in
Email sign-up is enabled by default in your local account identity provider settings. With the email option, customers can sign up and sign in with their email address and a password.
Sign-up: Customers are prompted for an email address, which is verified at sign-up with a one-time passcode. The customer then enters any other information requested on the sign-up page, for example, display name, given name, and surname. Then they select Continue to create an account.
Sign-in: After the customer signs up and creates an account, they can sign in by entering their email address and password.
Password reset: If you enable email and password sign-in, a password reset link appears on the password page. If the customer forgets their password, selecting this link sends a one-time passcode to their email address. After verification, the customer can choose a new password.
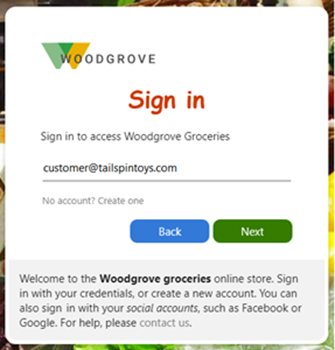
When you create a sign-up and sign-in user flow, Email with password is the default option.
Email with one-time passcode sign-in
Email with one-time passcode is an option in your local account identity provider settings. With this option, the customer signs in with a temporary passcode instead of a stored password each time they sign in.
Sign-up: Customers can sign up with their email address and request a temporary code, which is sent to their email address. Then they enter this code to continue signing in.
Sign-in: After the customer signs up and creates an account, each time they sign they'll enter their email address and receive a temporary passcode.
Note
If you want to enable multifactor authentication (MFA), set your local account authentication method to Email with password. If you set your local account option to Email with one-time passcode, customers who use this method won't be able to sign in because the one-time passcode is already their first-factor sign-in method and can't be used as a second factor. Currently, other verification methods aren't available for customer scenarios.
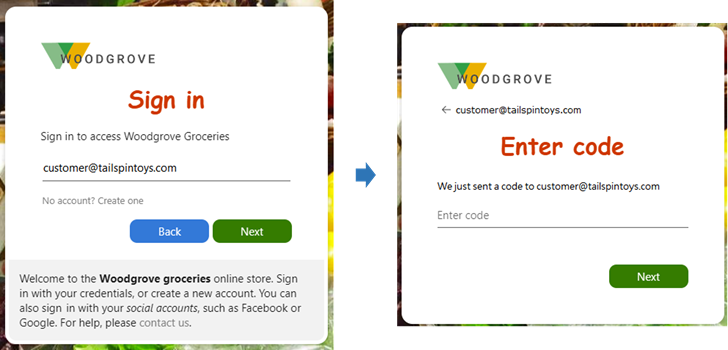
When you create a sign-up and sign-in user flow, Email one-time passcode is one of the local account options.
Social identity providers: Facebook and Google
For an optimal sign-in experience, federate with social identity providers whenever possible so you can give your customers a seamless sign-up and sign-in experience. In an external tenant, you can allow a customer to sign up and sign in using their own Facebook or Google account. When a customer signs up for your app using their social account, the social identity provider creates, maintains, and manages identity information while providing authentication services to applications.
When you enable social identity providers, customers can select from the social identity providers options you've made available on the sign-up page. To set up social identity providers in your external tenant, you create an application at the identity provider and configure credentials. You obtain a client or app ID and a client or app secret, which you can then add to your external tenant.
Google sign-in
By setting up federation with Google, you can allow customers to sign in to your applications with their own Gmail accounts. After you've added Google as one of your application's sign-in options, on the sign-in page, users can sign in to Microsoft Entra External ID with a Google account.
The following screenshots show the sign-in with Google experience. In the sign-in page, users select Sign-in with Google. At that point, the user is redirected to the Google identity provider to complete the sign-in.
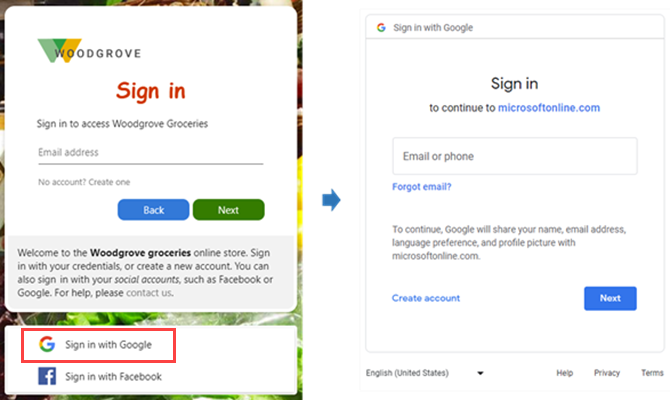
Learn how to add Google as an identity provider.
Facebook sign-in
By setting up federation with Facebook, you can allow invited users to sign in to your applications with their own Facebook accounts. After you've added Facebook as one of your application's sign-in options, on the sign-in page, users can sign-in to Microsoft Entra External ID with a Facebook account.
The following screenshots show the sign-in with Facebook experience. In the sign-in page, users select Sign-in with Facebook. Then the user is redirected to the Facebook identity provider to complete the sign-in.
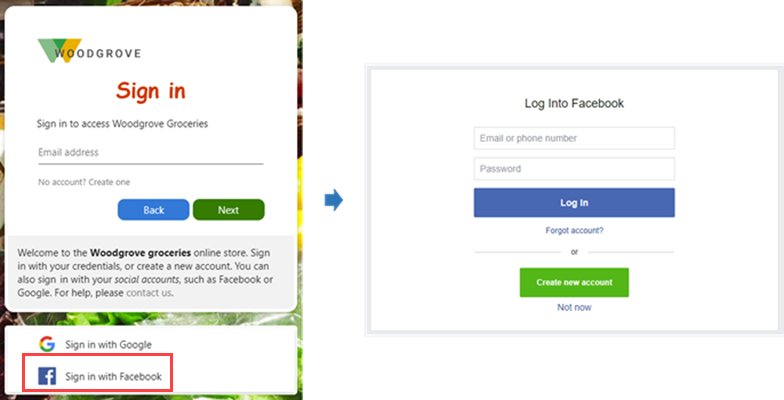
Learn how to add Facebook as an identity provider.
Updating sign-in methods
At any time, you can update the sign-in options you've selected for an app. For example, you can add social identity providers or change the local account sign-in method.
Be aware that when you change sign-in methods, the change affects only new users. Existing users will continue to sign in using their original method. For example, suppose you start out with the email and password sign-in method, and then change to email with one-time passcode. New users will sign in using a one-time passcode, but any users who have already signed up with an email and password will continue to be prompted for their email and password.
Microsoft Graph APIs
The following Microsoft Graph API operations are supported for managing identity providers and authentication methods in Microsoft Entra External ID:
- To identify what identity providers and authentication methods are supported, you call the List availableProviderTypes API.
- To identify the identity providers and authentication methods that are already configured and enabled in the tenant, you call the List identityProviders API.
- To enable a supported identity provider or authentication method, you call the Create identityProvider API.
Next steps
To learn how to add identity providers for sign-in to your applications, refer to the following articles:
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for