Tutorial: Configure Secure Hybrid Access with Microsoft Entra ID and Datawiza
In this tutorial, learn how to integrate Microsoft Entra ID with Datawiza for hybrid access. Datawiza Access Proxy (DAP) extends Microsoft Entra ID to enable single sign-on (SSO) and provide access controls to protect on-premises and cloud-hosted applications, such as Oracle E-Business Suite, Microsoft IIS, and SAP. With this solution, enterprises can transition from legacy web access managers (WAMs), such as Symantec SiteMinder, NetIQ, Oracle, and IBM, to Microsoft Entra ID without rewriting applications. Enterprises can use Datawiza as a no-code, or low-code, solution to integrate new applications to Microsoft Entra ID. This approach enables enterprises to implement their Zero Trust strategy while saving engineering time and reducing costs.
Learn more: Zero Trust security
Datawiza with Microsoft Entra authentication Architecture
Datawiza integration includes the following components:
- Microsoft Entra ID - Identity and access management service that helps users sign in and access external and internal resources
- Datawiza Access Proxy (DAP) - This service transparently passes identity information to applications through HTTP headers
- Datawiza Cloud Management Console (DCMC) - UI and RESTful APIs for administrators to manage the DAP configuration and access control policies
The following diagram illustrates the authentication architecture with Datawiza in a hybrid environment.
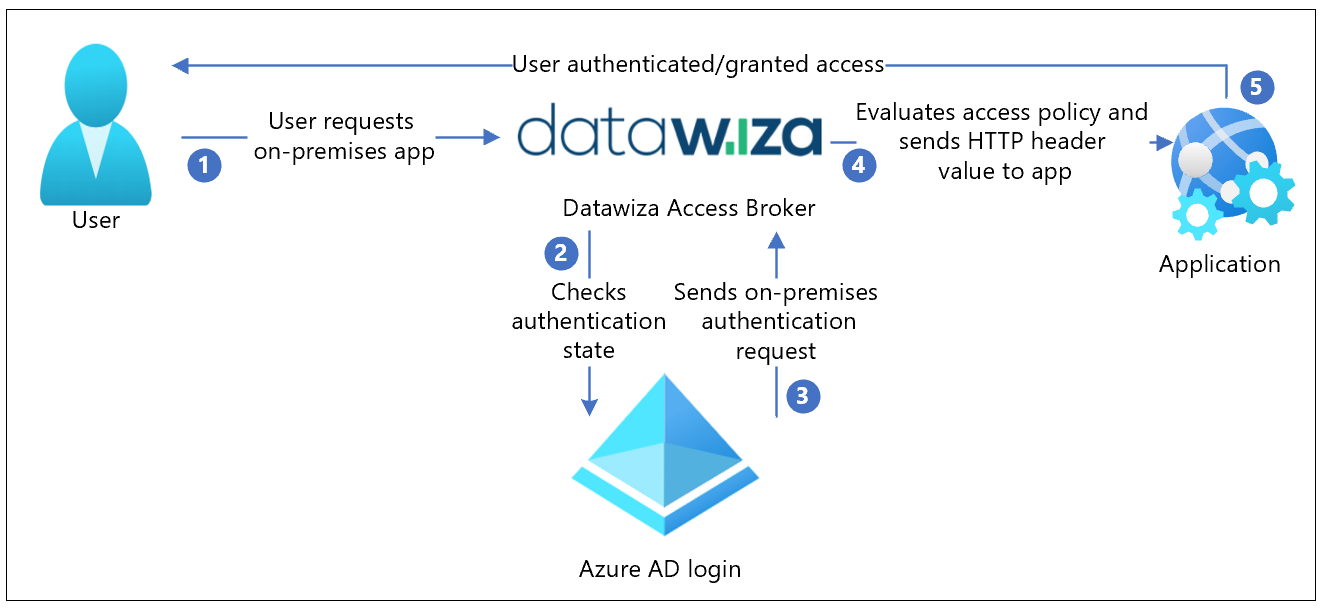
- The user requests access to the on-premises or cloud-hosted application. DAP proxies the request to the application.
- DAP checks user authentication state. If there's no session token, or the session token is invalid, DAP sends the user request to Microsoft Entra ID for authentication.
- Microsoft Entra ID sends the user request to the endpoint specified during DAP registration in the Microsoft Entra tenant.
- DAP evaluates policies and attribute values to be included in HTTP headers forwarded to the application. DAP might call out to the identity provider to retrieve the information to set the header values correctly. DAP sets the header values and sends the request to the application.
- The user is authenticated and is granted access.
Prerequisites
To get started, you need:
- An Azure subscription
- If you don't have one, you can get an Azure free account
- An Microsoft Entra tenant linked to the Azure subscription
- Docker and docker-compose are required to run DAP
- Your applications can run on platforms, such as a virtual machine (VM) or bare metal
- An on-premises or cloud-hosted application to transition from a legacy identity system to Microsoft Entra ID
- In this example, DAP is deployed on the same server as the application
- The application runs on localhost: 3001. DAP proxies traffic to the application via localhost: 9772
- The traffic to the application reaches DAP, and is proxied to the application
Configure Datawiza Cloud Management Console
Sign in to Datawiza Cloud Management Console (DCMC).
Create an application on DCMC and generate a key pair for the app:
PROVISIONING_KEYandPROVISIONING_SECRET.To create the app and generate the key pair, follow the instructions in Datawiza Cloud Management Console.
Register your application in Microsoft Entra ID with One Click Integration With Microsoft Entra ID.
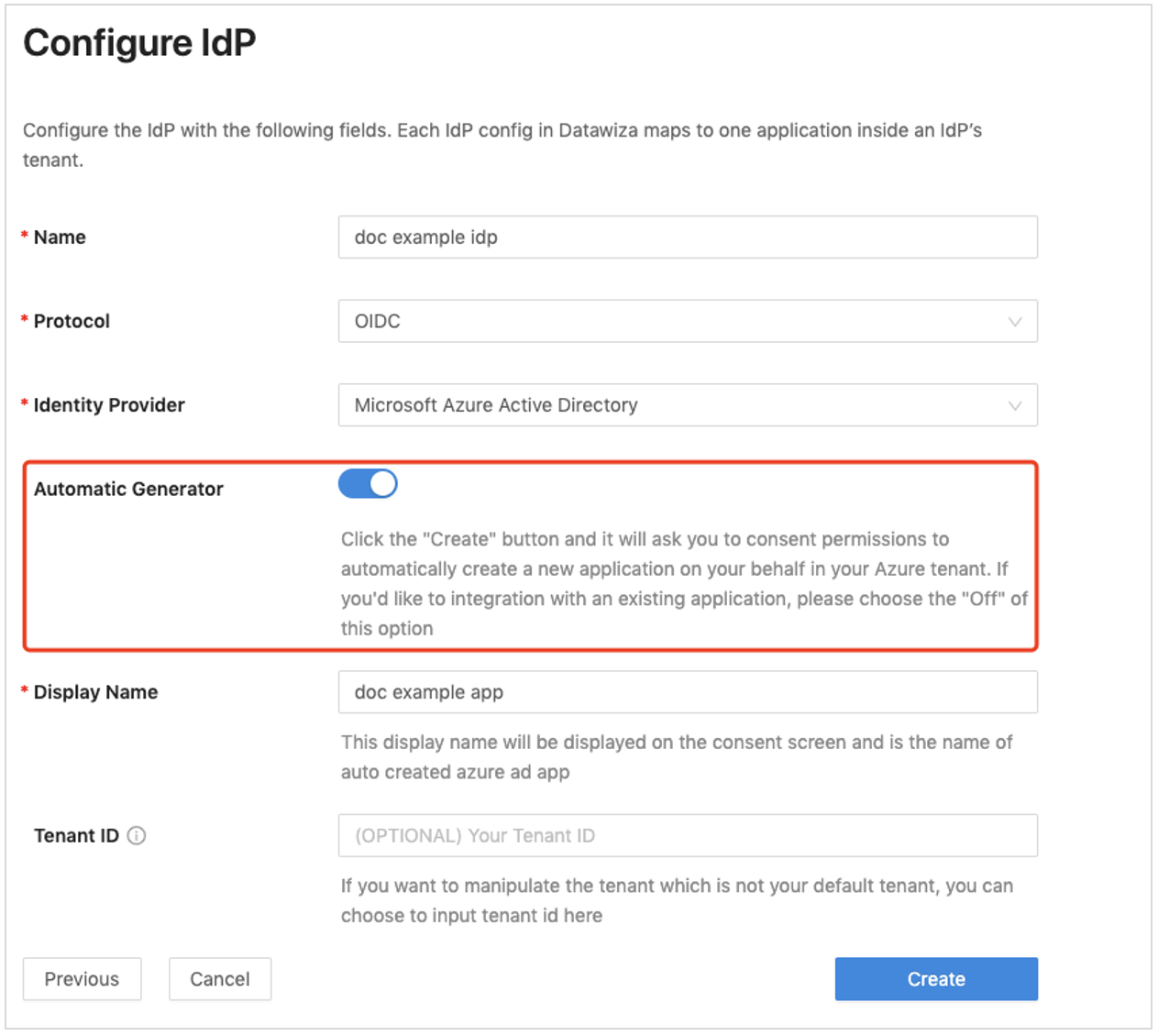
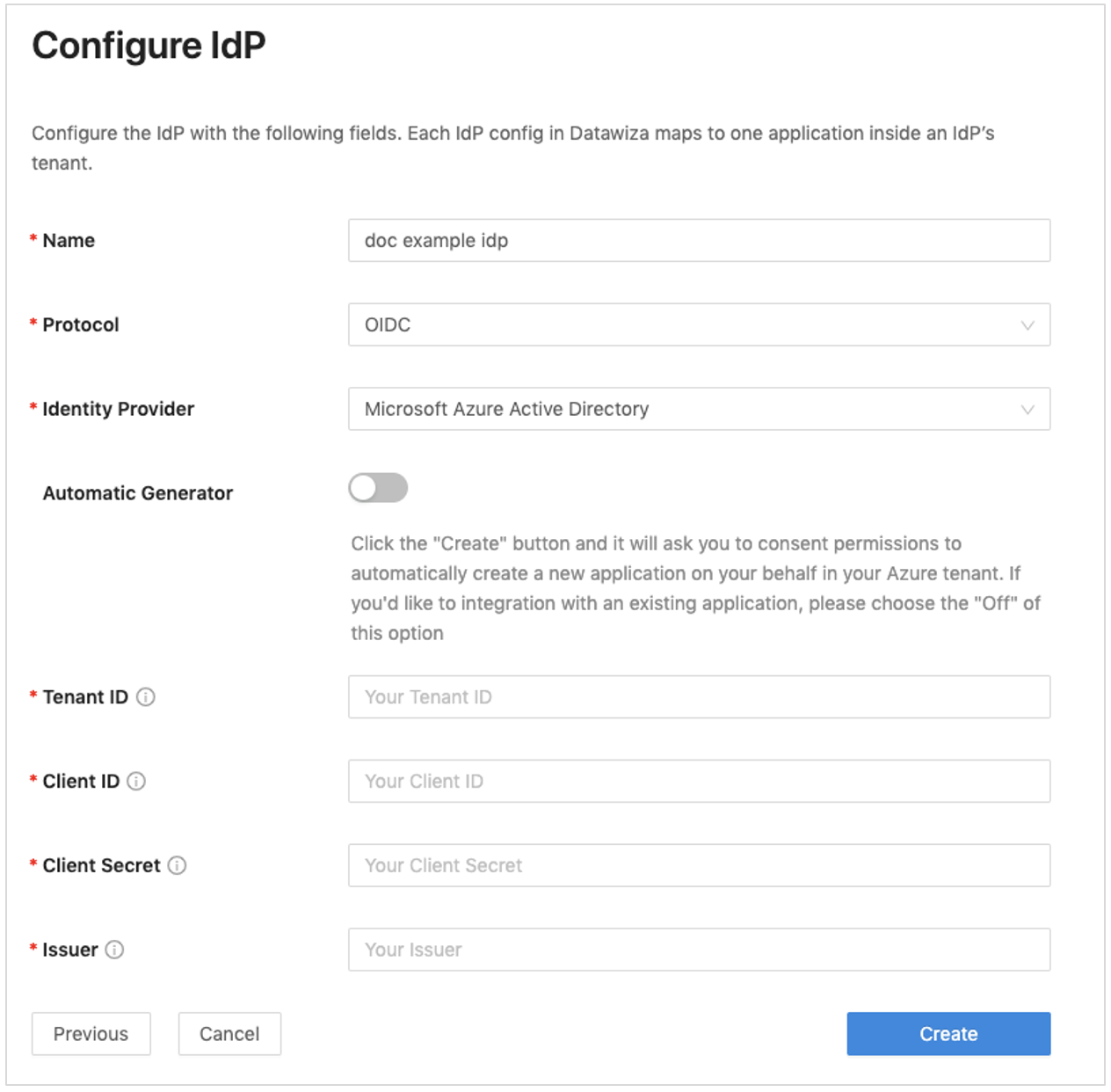
To use a web application, manually populate form fields: Tenant ID, Client ID, and Client Secret.
Learn more: To create a web application and obtain values, go to docs.datawiza.com for Microsoft Entra ID documentation.
Run DAP using either Docker or Kubernetes. The docker image is needed to create a sample header-based application.
- For Kubernetes, see Deploy Datawiza Access Proxy with a Web App using Kubernetes
- For Docker, see Deploy Datawiza Access Proxy With Your App
- You can use the following sample docker image docker-compose.yml file:
services:
datawiza-access-broker:
image: registry.gitlab.com/datawiza/access-broker
container_name: datawiza-access-broker
restart: always
ports:
- "9772:9772"
environment:
PROVISIONING_KEY: #############################################
PROVISIONING_SECRET: ##############################################
header-based-app:
image: registry.gitlab.com/datawiza/header-based-app
restart: always
ports:
- "3001:3001"
- Sign in to the container registry.
- Download the DAP images and the header-based application in this Important Step.
- Run the following command:
docker-compose -f docker-compose.yml up. - The header-based application has SSO enabled with Microsoft Entra ID.
- In a browser, go to
http://localhost:9772/. - A Microsoft Entra sign-in page appears.
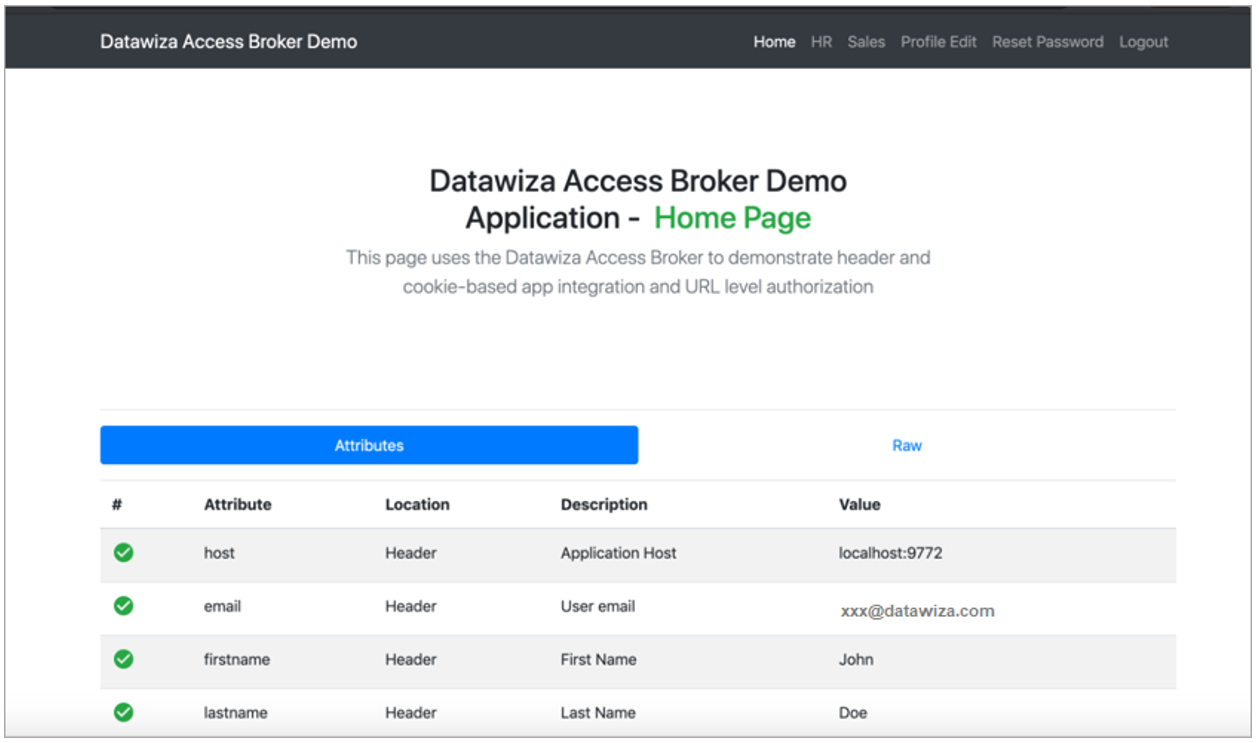
- Pass user attributes to the header-based application. DAP gets user attributes from Microsoft Entra ID and passes attributes to the application via a header or cookie.
- To pass user attributes such as email address, first name, and last name to the header-based application, see Pass User Attributes.
- To confirm configured user attributes, observe a green check mark next to each attribute.
Test the flow
- Go to the application URL.
- DAP redirects you to the Microsoft Entra sign-in page.
- After authentication, you're redirected to DAP.
- DAP evaluates policies, calculates headers, and sends you to the application.
- The requested application appears.
Next steps
- Tutorial: Configure Azure Active Directory B2C with Datawiza to provide secure hybrid access
- Tutorial: Configure Datawiza to enable Microsoft Entra multifactor authentication and SSO to Oracle JD Edwards
- Tutorial: Configure Datawiza to enable Microsoft Entra multifactor authentication and SSO to Oracle PeopleSoft
- Tutorial: Configure Datawiza to enable Microsoft Entra multifactor authentication and SSO to Oracle Hyperion EPM
- Go to docs.datawiza.com for Datawiza User Guides
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for