Tutorial: Application proxy configuration for Microsoft Entra SAML SSO for Confluence
This article helps to configure Microsoft Entra SAML SSO for your on-premises Confluence application using Application Proxy.
Prerequisites
To configure Microsoft Entra integration with Confluence SAML SSO by Microsoft, you need the following items:
- A Microsoft Entra subscription.
- Confluence server application installed on a Windows 64-bit server (on-premises or on the cloud IaaS infrastructure).
- Confluence server is HTTPS enabled.
- Note the supported versions for Confluence Plugin are mentioned in below section.
- Confluence server is reachable on internet particularly to Microsoft Entra Login page for authentication and should able to receive the token from Microsoft Entra ID.
- Admin credentials are set up in Confluence.
- WebSudo is disabled in Confluence.
- Test user created in the Confluence server application.
To get started, you need the following items:
- Do not use your production environment, unless it is necessary.
- A Microsoft Entra subscription. If you don't have a subscription, you can get a free account.
- Confluence SAML SSO by Microsoft single sign-on (SSO) enabled subscription.
Supported versions of Confluence
As of now, following versions of Confluence are supported:
- Confluence: 5.0 to 5.10
- Confluence: 6.0.1 to 6.15.9
- Confluence: 7.0.1 to 7.17.0
Note
Please note that our Confluence Plugin also works on Ubuntu Version 16.04
Scenario description
In this tutorial, you configure and test Microsoft Entra SSO for on-premises confluence setup using application proxy mode.
- Download and Install Microsoft Entra private network connector.
- Add Application Proxy in Microsoft Entra ID.
- Add a Confluence SAML SSO app in Microsoft Entra ID.
- Configure SSO for SAML SSO Confluence Application in Microsoft Entra ID.
- Create a Microsoft Entra test user.
- Assigning the test user for the Confluence Microsoft Entra App.
- Configure SSO for Confluence SAML SSO by Microsoft Confluence plugin in your Confluence Server.
- Assigning the test user for the Microsoft Confluence plugin in your Confluence Server.
- Test the SSO.
Download and Install the private network connector Service
Sign in to the Microsoft Entra admin center as at least a Application Administrator.
Browse to Identity > Applications > Enterprise applications > Application proxy.
Select Download connector service.
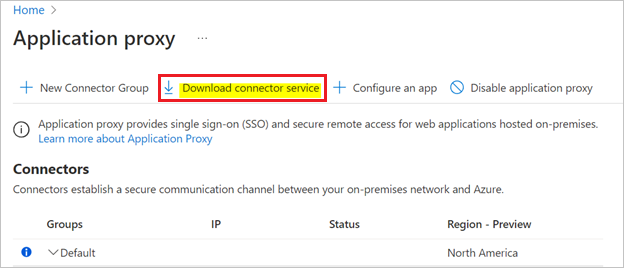
Accept terms & conditions to download connector. Once downloaded, install it to the system, which hosts the confluence application.
Add an On-premises Application in Microsoft Entra ID
To add an Application proxy, we need to create an enterprise application.
Sign in to the Microsoft Entra admin center as at least a Application Administrator.
Browse to Identity > Applications > Enterprise applications > New application.
Choose Add an on-premises application.
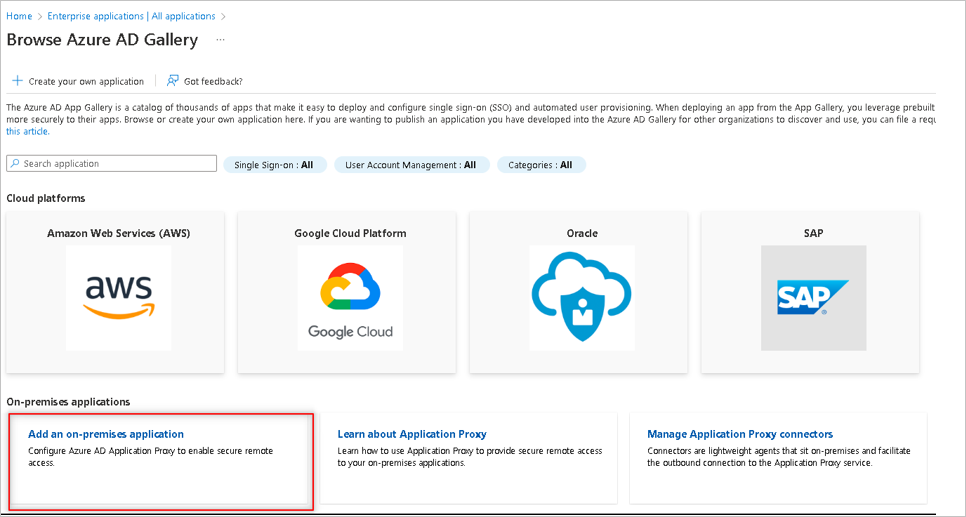
Type the name of the application and click the create button at the bottom left column.
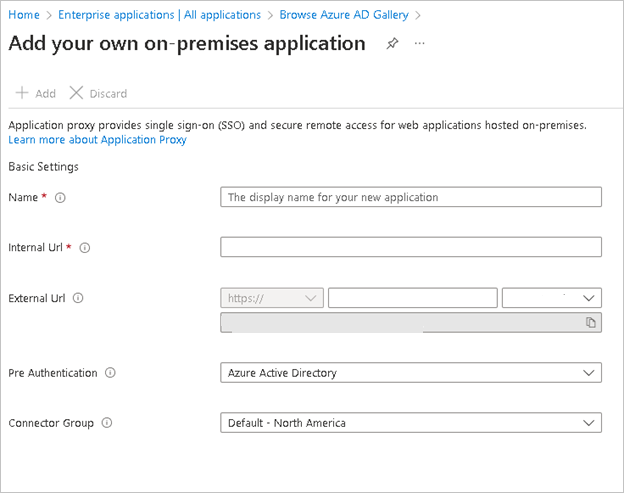
- Internal URL will be your Confluence application URL.
- External URL will be auto-generated based on the Name you choose.
- Pre Authentication can be left to Microsoft Entra ID as default.
- Choose Connector Group which lists your connector agent under it as active.
- Leave the Additional Settings as default.
Click on the Save from the top options to configure an application proxy.
Add a Confluence SAML SSO app in Microsoft Entra ID
Now that you've prepared your environment and installed a connector, you're ready to add confluence applications to Microsoft Entra ID.
- Sign in to the Microsoft Entra admin center as at least a Application Administrator.
- Browse to Identity > Applications > Enterprise applications > New application.
- Select Confluence SAML SSO by Microsoft widget from the Microsoft Entra Gallery.
Configure SSO for Confluence SAML SSO Application in Microsoft Entra ID
Sign in to the Microsoft Entra admin center as at least a Application Administrator.
Browse to Identity > Applications > Enterprise applications.
Open the Confluence SAML SSO by Microsoft > Single sign-on.
On the Select a single sign-on method page, select SAML.
On the Set up single sign-on with SAML page, click the pencil icon for Basic SAML Configuration to edit the settings.
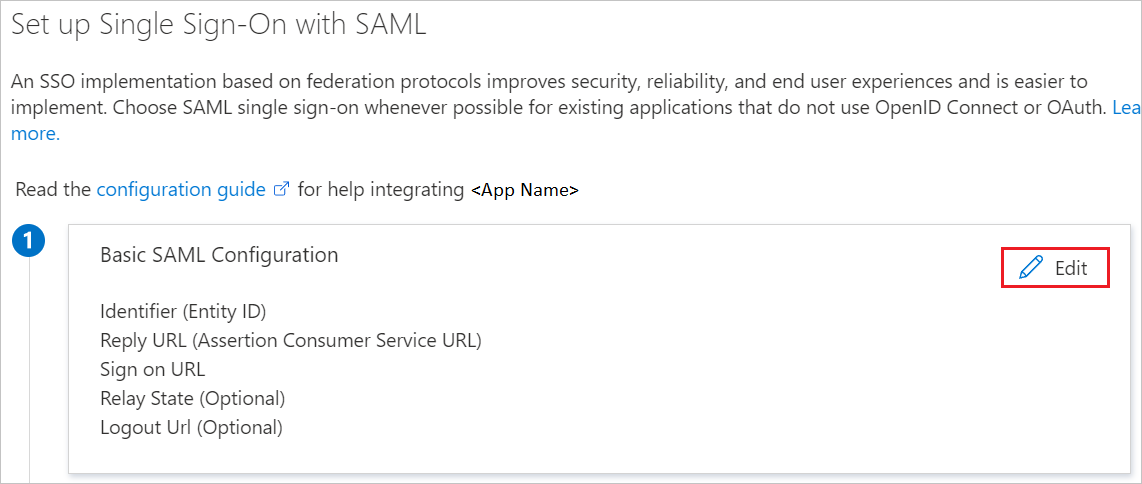
On the Basic SAML Configuration section, enter the External Url value for the following fields: identifier, Reply URL, SignOn URL.
Create a Microsoft Entra test user
In this section, you'll create a test user called B.Simon.
- Sign in to the Microsoft Entra admin center as at least a User Administrator.
- Browse to Identity > Users > All users.
- Select New user > Create new user, at the top of the screen.
- In the User properties, follow these steps:
- In the Display name field, enter
B.Simon. - In the User principal name field, enter the username@companydomain.extension. For example,
B.Simon@contoso.com. - Select the Show password check box, and then write down the value that's displayed in the Password box.
- Select Review + create.
- In the Display name field, enter
- Select Create.
Assigning the test user for the Confluence Microsoft Entra App
In this section, you'll enable B.Simon to use single sign-on by granting access to Confluence Microsoft Entra App.
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
Browse to Identity > Applications > Enterprise applications > Confluence SAML SSO by Microsoft.
In the app's overview page, find the Manage section and select Users and groups.
Select Add user/group, then select Users and groups in the Add Assignment dialog.
In the Users and groups dialog, select B.Simon from the Users list, then click the Select button at the bottom of the screen.
In the Add Assignment dialog, click the Assign button.
Verify the application proxy setup by checking if the configured test user is able to SSO using the external URL mentioned in the on-premises application.
Note
Complete the setup of the JIRA SAML SSO by Microsoft application by following this tutorial.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for