Events
Sep 16, 11 PM - Oct 18, 11 PM
Join us on a learning journey combining AI, apps and cloud-scale data to build unique solutions.
Learn moreThis browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Policies and policy initiatives provide a simple method to enable logging at-scale via diagnostics settings for Azure Monitor. Using a policy initiative, you can turn on audit logging for all supported resources in your Azure environment.
Enable resource logs to track activities and events that take place on your resources and give you visibility and insights into any changes that occur. Assign policies to enable resource logs and to send them to destinations according to your needs. Send logs to event hubs for third-party SIEM systems, enabling continuous security operations. Send logs to storage accounts for longer term storage or the fulfillment of regulatory compliance.
A set of built-in policies and initiatives exists to direct resource logs to Log Analytics Workspaces, Event Hubs, and Storage Accounts. The policies enable audit logging, sending logs belonging to the audit or the All logs log category group, to an event hub, Log Analytics workspace or Storage Account. The policies' effect is DeployIfNotExists, which deploys the policy as a default if there aren't other settings defined.
Deploy the policies and initiatives using the Portal, CLI, PowerShell, or Azure Resource Management templates
The following steps show how to apply the policy to send audit logs to for key vaults to a log analytics workspace.
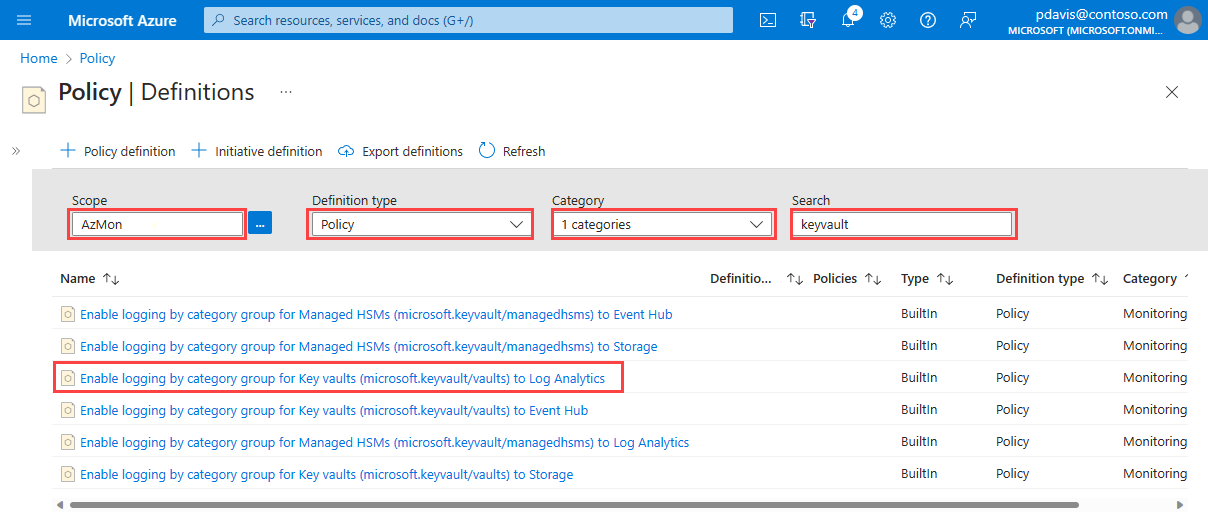
From the Policy page, select Definitions.
Select your scope. You can apply a policy to the entire subscription, a resource group, or an individual resource.
From the Definition type dropdown, select Policy.
Select Monitoring from the Category dropdown
Enter keyvault in the Search field.
Select the Enable logging by category group for Key vaults (microsoft.keyvault/vaults) to Log Analytics policy,
From the policy definition page, select Assign
Select the Parameters tab.
Select the Log Analytics Workspace that you want to send the audit logs to.
On the remediation tab, select the keyvault policy from the Policy to remediate dropdown.
Select the Create a Managed Identity checkbox.
Under Type of Managed Identity, select System assigned Managed Identity.
The policy is visible in the resources' diagnostic settings after approximately 30 minutes.
Policies are applied to new resources when they're created. To apply a policy to existing resources, create a remediation task. Remediation tasks bring resources into compliance with a policy.
Remediation tasks act for specific policies. For initiatives that contain multiple policies, create a remediation task for each policy in the initiative where you have resources that you want to bring into compliance.
Define remediation tasks when you first assign the policy, or at any stage after assignment.
To create a remediation task for policies during the policy assignment, select the Remediation tab on Assign policy page and select the Create remediation task checkbox.
To create a remediation task after the policy has been assigned, select your assigned policy from the list on the Policy Assignments page.
Select Remediate. Track the status of your remediation task in the Remediation tasks tab of the Policy Remediation page.
For more information on remediation tasks, see Remediate noncompliant resources
Initiatives are collections of policies. There are two sets of initiatives for Azure Monitor Diagnostics settings:
Enable the audit category group resource logging
Enable the allLogs category group resource logging
In this example, we assign an initiative for sending audit logs to a Log Analytics workspace.
From the policy Definitions page, select your scope.
Select Initiative in the Definition type dropdown.
Select Monitoring in the Category dropdown.
Enter audit in the Search field.
Select thee Enable audit category group resource logging for supported resources to Log Analytics initiative.
On the Basics tab of the Assign initiative page, select a Scope that you want the initiative to apply to.
Enter a name in the Assignment name field.
The Parameters contains the parameters defined in the policy. In this case, we need to select the Log Analytics workspace that we want to send the logs to. For more information in the individual parameters for each policy, see Policy-specific parameters.
Select the Log Analytics workspace to send your audit logs to.
To verify that your policy or initiative assignment is working, create a resource in the subscription or resource group scope that you defined in your policy assignment.
After 10 minutes, select the Diagnostics settings page for your resource. Your diagnostic setting appears in the list with the default name setByPolicy-LogAnalytics and the workspace name that you configured in the policy.
Change the default name in the Parameters tab of the Assign initiative or policy page by unselecting the Only show parameters that need input or review checkbox.
The following table describes the common parameters for each set of policies.
| Parameter | Description | Valid Values | Default |
|---|---|---|---|
| effect | Enable or disable the execution of the policy | DeployIfNotExists, AuditIfNotExists, Disabled |
DeployIfNotExists |
| diagnosticSettingName | Diagnostic Setting Name | setByPolicy-{LogAnalytics|EventHubs|Storage} | |
| categoryGroup | Diagnostic category group | none, audit, allLogs |
audit |
| resourceTypeList | For initiatives, a list of resource types to be evaluated for diagnostic setting existence. | Supported resources | All supported resources |
This policy deploys a diagnostic setting using a category group to route logs to a Log Analytics workspace.
| Parameter | Description | Valid Values | Default |
|---|---|---|---|
| resourceLocationList | Resource Location List to send logs to nearby Log Analytics. "*" selects all locations |
Supported locations | * |
| logAnalytics | Log Analytics Workspace |
This policy deploys a diagnostic setting using a category group to route logs to an event hub.
| Parameter | Description | Valid Values | Default |
|---|---|---|---|
| resourceLocation | Resource Location must be the same location as the event hub Namespace | Supported locations | |
| eventHubAuthorizationRuleId | Event hub Authorization Rule ID. The authorization rule is at event hub namespace level. For example, /subscriptions/{subscription ID}/resourceGroups/{resource group}/providers/Microsoft.EventHub/namespaces/{Event Hub namespace}/authorizationrules/{authorization rule} | ||
| eventHubName | Event hub name | Monitoring |
This policy deploys a diagnostic setting using a category group to route logs to a Storage Account.
| Parameter | Description | Valid Values | Default |
|---|---|---|---|
| resourceLocation | Resource Location must be in the same location as the Storage Account | Supported locations | |
| storageAccount | Storage Account resourceId |
Built-in All logs and Audit logs policies for Log Analytics workspaces, Event Hubs, and Storage Accounts exist for the following resources:
| Resource Type | All logs | Audit Logs |
|---|---|---|
| microsoft.aad/domainservices | Yes | Yes |
| microsoft.agfoodplatform/farmbeats | Yes | Yes |
| microsoft.analysisservices/servers | Yes | No |
| microsoft.apimanagement/service | Yes | Yes |
| microsoft.app/managedenvironments | Yes | Yes |
| microsoft.appconfiguration/configurationstores | Yes | Yes |
| microsoft.appplatform/spring | Yes | No |
| microsoft.attestation/attestationproviders | Yes | Yes |
| microsoft.automation/automationaccounts | Yes | Yes |
| microsoft.autonomousdevelopmentplatform/workspaces | Yes | No |
| microsoft.avs/privateclouds | Yes | Yes |
| microsoft.azureplaywrightservice/accounts | Yes | Yes |
| microsoft.azuresphere/catalogs | Yes | Yes |
| microsoft.batch/batchaccounts | Yes | Yes |
| microsoft.botservice/botservices | Yes | No |
| microsoft.cache/redis | Yes | Yes |
| microsoft.cache/redisenterprise/databases | Yes | Yes |
| microsoft.cdn/cdnwebapplicationfirewallpolicies | Yes | No |
| microsoft.cdn/profiles | Yes | Yes |
| microsoft.cdn/profiles/endpoints | Yes | No |
| microsoft.chaos/experiments | Yes | Yes |
| microsoft.classicnetwork/networksecuritygroups | Yes | No |
| microsoft.cloudtest/hostedpools | Yes | No |
| microsoft.codesigning/codesigningaccounts | Yes | Yes |
| microsoft.cognitiveservices/accounts | Yes | Yes |
| microsoft.communication/communicationservices | Yes | No |
| microsoft.community/communitytrainings | Yes | Yes |
| microsoft.confidentialledger/managedccfs | Yes | Yes |
| microsoft.connectedcache/enterprisemcccustomers | Yes | No |
| microsoft.connectedcache/ispcustomers | Yes | No |
| microsoft.containerinstance/containergroups | Yes | No |
| microsoft.containerregistry/registries | Yes | Yes |
| microsoft.customproviders/resourceproviders | Yes | No |
| microsoft.d365customerinsights/instances | Yes | No |
| microsoft.dashboard/grafana | Yes | Yes |
| microsoft.databricks/workspaces | Yes | No |
| microsoft.datafactory/factories | Yes | No |
| microsoft.datalakeanalytics/accounts | Yes | No |
| microsoft.datalakestore/accounts | Yes | No |
| microsoft.dataprotection/backupvaults | Yes | No |
| microsoft.datashare/accounts | Yes | No |
| microsoft.dbformariadb/servers | Yes | No |
| microsoft.dbformysql/flexibleservers | Yes | Yes |
| microsoft.dbformysql/servers | Yes | No |
| microsoft.dbforpostgresql/flexibleservers | Yes | Yes |
| microsoft.dbforpostgresql/servergroupsv2 | Yes | No |
| microsoft.dbforpostgresql/servers | Yes | No |
| microsoft.desktopvirtualization/applicationgroups | Yes | No |
| microsoft.desktopvirtualization/hostpools | Yes | No |
| microsoft.desktopvirtualization/scalingplans | Yes | No |
| microsoft.desktopvirtualization/workspaces | Yes | No |
| microsoft.devcenter/devcenters | Yes | Yes |
| microsoft.devices/iothubs | Yes | Yes |
| microsoft.devices/provisioningservices | Yes | No |
| microsoft.digitaltwins/digitaltwinsinstances | Yes | No |
| microsoft.documentdb/cassandraclusters | Yes | Yes |
| microsoft.documentdb/databaseaccounts | Yes | Yes |
| microsoft.documentdb/mongoclusters | Yes | Yes |
| microsoft.eventgrid/domains | Yes | Yes |
| microsoft.eventgrid/partnernamespaces | Yes | Yes |
| microsoft.eventgrid/partnertopics | Yes | No |
| microsoft.eventgrid/systemtopics | Yes | No |
| microsoft.eventgrid/topics | Yes | Yes |
| microsoft.eventhub/namespaces | Yes | Yes |
| microsoft.experimentation/experimentworkspaces | Yes | No |
| microsoft.healthcareapis/services | Yes | No |
| microsoft.healthcareapis/workspaces/dicomservices | Yes | No |
| microsoft.healthcareapis/workspaces/fhirservices | Yes | No |
| microsoft.healthcareapis/workspaces/iotconnectors | Yes | No |
| microsoft.insights/autoscalesettings | Yes | No |
| microsoft.insights/components | Yes | No |
| microsoft.insights/datacollectionrules | Yes | No |
| microsoft.keyvault/managedhsms | Yes | Yes |
| microsoft.keyvault/vaults | Yes | Yes |
| microsoft.kusto/clusters | Yes | Yes |
| microsoft.loadtestservice/loadtests | Yes | Yes |
| microsoft.logic/integrationaccounts | Yes | No |
| microsoft.logic/workflows | Yes | No |
| microsoft.machinelearningservices/registries | Yes | Yes |
| microsoft.machinelearningservices/workspaces | Yes | Yes |
| microsoft.machinelearningservices/workspaces/onlineendpoints | Yes | No |
| microsoft.managednetworkfabric/networkdevices | Yes | No |
| microsoft.media/mediaservices | Yes | Yes |
| microsoft.media/mediaservices/liveevents | Yes | Yes |
| microsoft.media/mediaservices/streamingendpoints | Yes | Yes |
| microsoft.netapp/netappaccounts/capacitypools/volumes | Yes | Yes |
| microsoft.network/applicationgateways | Yes | No |
| microsoft.network/azurefirewalls | Yes | No |
| microsoft.network/bastionhosts | Yes | Yes |
| microsoft.network/dnsresolverpolicies | Yes | No |
| microsoft.network/expressroutecircuits | Yes | No |
| microsoft.network/frontdoors | Yes | Yes |
| microsoft.network/loadbalancers | Yes | No |
| microsoft.network/networkmanagers | Yes | Yes |
| microsoft.network/networkmanagers/ipampools | Yes | Yes |
| microsoft.network/networksecuritygroups | Yes | No |
| microsoft.network/networksecurityperimeters | Yes | No |
| microsoft.network/p2svpngateways | Yes | Yes |
| microsoft.network/publicipaddresses | Yes | Yes |
| microsoft.network/publicipprefixes | Yes | Yes |
| microsoft.network/trafficmanagerprofiles | Yes | No |
| microsoft.network/virtualnetworkgateways | Yes | Yes |
| microsoft.network/virtualnetworks | Yes | No |
| microsoft.network/vpngateways | Yes | No |
| microsoft.networkanalytics/dataproducts | Yes | Yes |
| microsoft.networkcloud/baremetalmachines | Yes | No |
| microsoft.networkcloud/clusters | Yes | No |
| microsoft.networkcloud/storageappliances | Yes | No |
| microsoft.networkfunction/azuretrafficcollectors | Yes | No |
| microsoft.notificationhubs/namespaces | Yes | Yes |
| microsoft.notificationhubs/namespaces/notificationhubs | Yes | Yes |
| microsoft.openenergyplatform/energyservices | Yes | No |
| microsoft.operationalinsights/workspaces | Yes | Yes |
| microsoft.powerbi/tenants/workspaces | Yes | No |
| microsoft.powerbidedicated/capacities | Yes | No |
| microsoft.purview/accounts | Yes | Yes |
| microsoft.recoveryservices/vaults | Yes | No |
| microsoft.relay/namespaces | Yes | No |
| microsoft.search/searchservices | Yes | Yes |
| microsoft.servicebus/namespaces | Yes | Yes |
| microsoft.servicenetworking/trafficcontrollers | Yes | No |
| microsoft.signalrservice/signalr | Yes | Yes |
| microsoft.signalrservice/webpubsub | Yes | Yes |
| microsoft.sql/managedinstances | Yes | Yes |
| microsoft.sql/managedinstances/databases | Yes | No |
| microsoft.sql/servers/databases | Yes | Yes |
| microsoft.storagecache/caches | Yes | No |
| microsoft.storagemover/storagemovers | Yes | No |
| microsoft.streamanalytics/streamingjobs | Yes | No |
| microsoft.synapse/workspaces | Yes | Yes |
| microsoft.synapse/workspaces/bigdatapools | Yes | Yes |
| microsoft.synapse/workspaces/kustopools | Yes | Yes |
| microsoft.synapse/workspaces/scopepools | Yes | Yes |
| microsoft.synapse/workspaces/sqlpools | Yes | Yes |
| microsoft.timeseriesinsights/environments | Yes | No |
| microsoft.timeseriesinsights/environments/eventsources | Yes | No |
| microsoft.videoindexer/accounts | Yes | No |
| microsoft.web/hostingenvironments | Yes | Yes |
| microsoft.workloads/sapvirtualinstances | Yes | Yes |
Events
Sep 16, 11 PM - Oct 18, 11 PM
Join us on a learning journey combining AI, apps and cloud-scale data to build unique solutions.
Learn moreTraining
Learning path
Implement finance and operations apps - Training
Plan and design your project methodology to successfully implement finance and operations apps with FastTrack services, data management and more.
Certification
Microsoft Certified: Azure Administrator Associate - Certifications
Demonstrate key skills to configure, manage, secure, and administer key professional functions in Microsoft Azure.