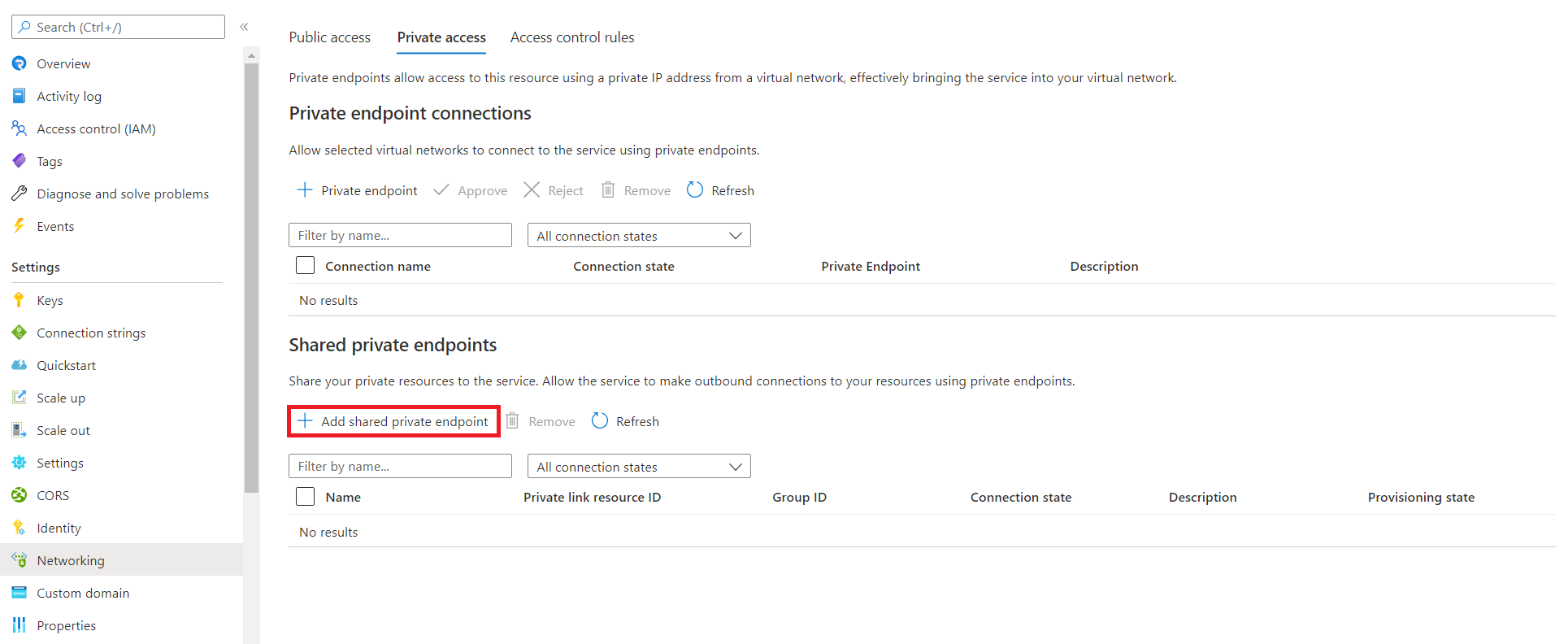
Access Key Vault in a private network through shared private endpoints
Azure SignalR Service can access your Key Vault in a private network through Shared Private Endpoints. This way, your Key Vault isn't exposed on a public network.
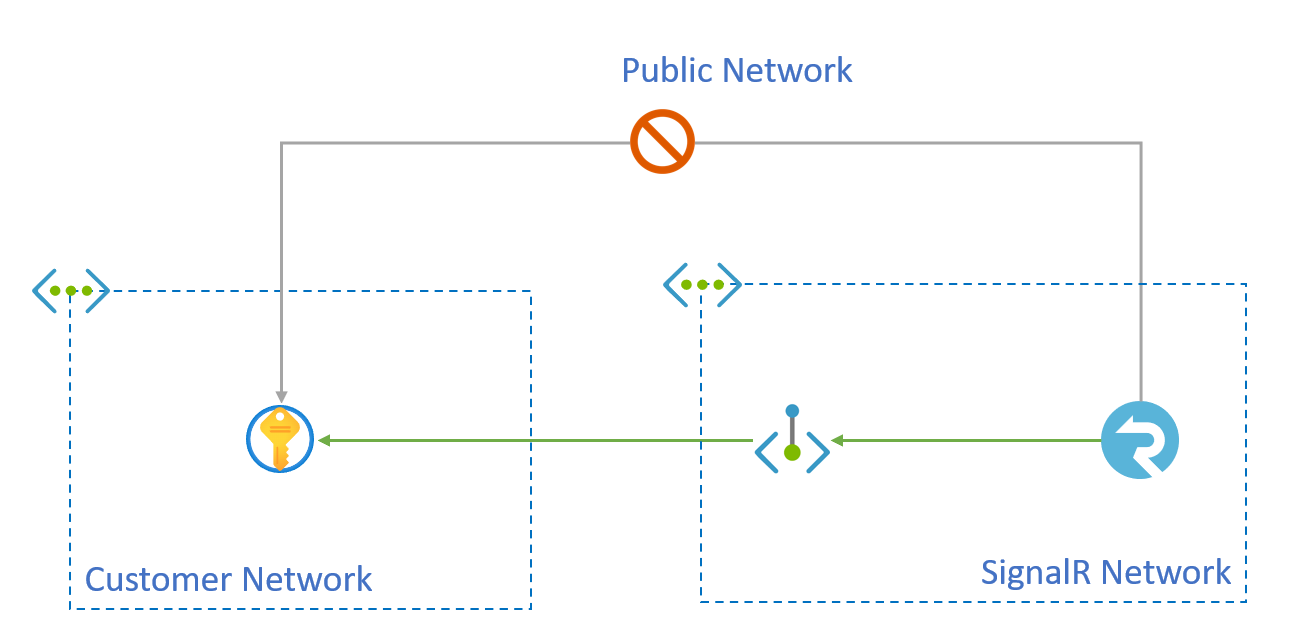
You can create private endpoints through Azure SignalR Service APIs for shared access to a resource integrated with Azure Private Link service. These endpoints, called shared private link resources, are created inside the SignalR execution environment and aren't accessible outside this environment.
In this article, you'll learn how to create a shared private endpoint to Key Vault.
Prerequisites
You'll need the following resources to complete this article:
- An Azure resource group.
- An Azure SignalR Service instance.
- An Azure Key Vault instance.
The examples in this article use the following naming convention, although you can use your own names instead.
- The resource ID of this Azure SignalR Service is /subscriptions/00000000-0000-0000-0000-000000000000/resourceGroups/contoso/providers/Microsoft.SignalRService/signalr/contoso-signalr.
- The resource ID of Azure Key Vault is /subscriptions/00000000-0000-0000-0000-000000000000/resourceGroups/contoso/providers/Microsoft.KeyVault/vaults/contoso-kv.
- The rest of the examples show how the contoso-signalr service can be configured so that its outbound calls to Key Vault go through a private endpoint rather than public network.
Create a shared private link resource to the Key Vault
In the Azure portal, go to your Azure SignalR Service resource.
Select Networking.
Select the Private access tab.
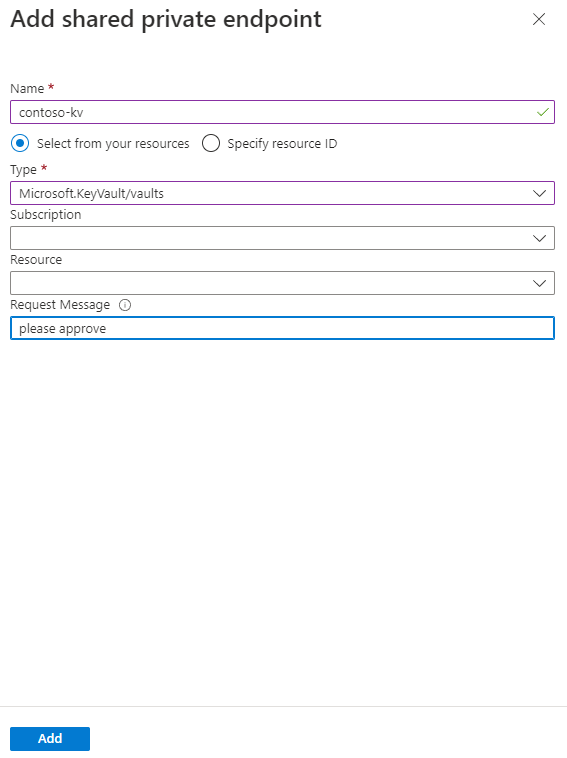
Select Add shared private endpoint in the Shared private endpoints section.
Enter the following information:
Field Description Name The name of the shared private endpoint. Type Select Microsoft.KeyVault/vaults Subscription The subscription containing your Key Vault. Resource Enter the name of your Key Vault resource. Request Message Enter "please approve" Select Add.
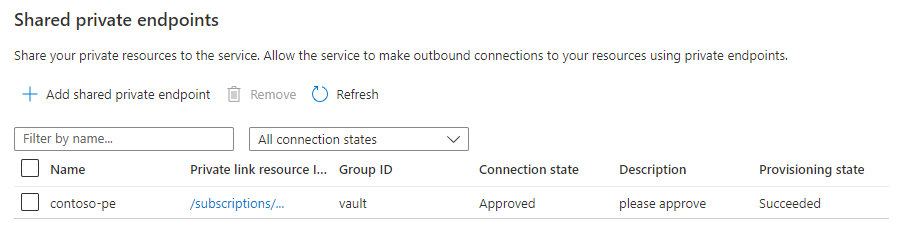
When you've successfully added the private endpoint, the provisioning state will be Succeeded. The connection state will be Pending until you approve the endpoint on the Key Vault side.
Approve the private endpoint connection for the Key Vault
Go to your Key Vault resource
Select the Networking.
Select the Private endpoint connections tab. After the asynchronous operation has succeeded, there should be a request for a private endpoint connection with the request message from the previous API call.
Select the private endpoint that SignalR Service created, then select Approve.
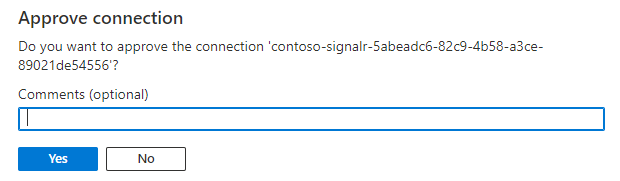
Select Yes to approve the connection.
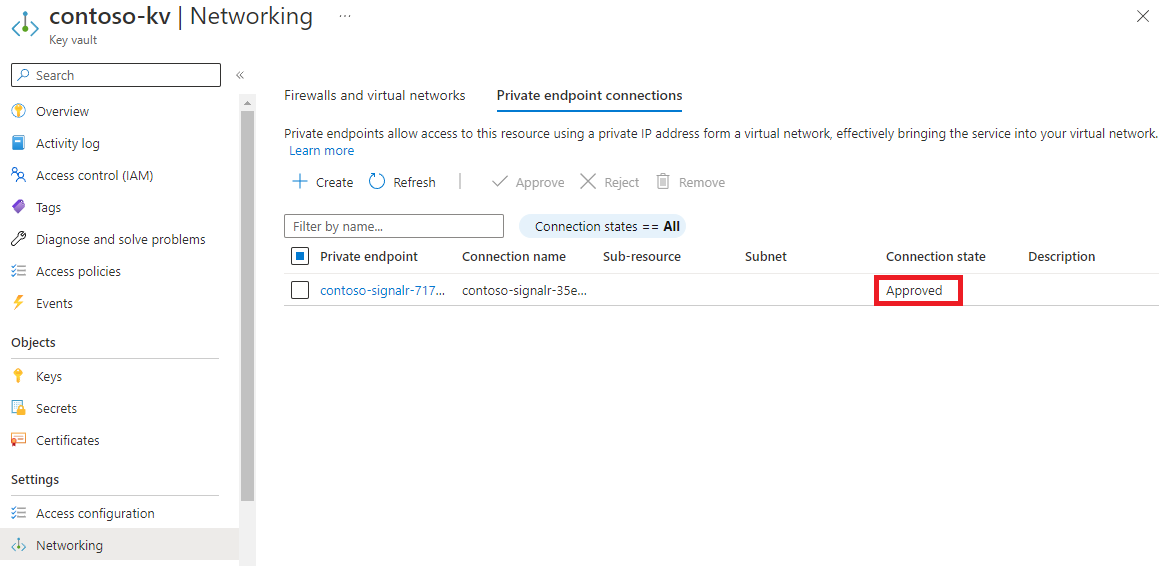
Verify the shared private endpoint is functional
After a few minutes, the approval propagates to the SignalR Service, and the connection state is set to Approved. You can check the state using either Azure portal or Azure CLI.
When the private endpoint between the SignalR Service and Azure Key Vault is functional, the value of the provisioning state is Succeeded, and the connection state is Approved.
Cleanup
If you don't plan to use the resources you've created in this article, you can delete the Resource Group.
Caution
Deleting the resource group deletes all resources contained within it. If resources outside the scope of this article exist in the specified resource group, they will also be deleted.
Next steps
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for