Secure Azure SignalR outbound traffic through shared private endpoints
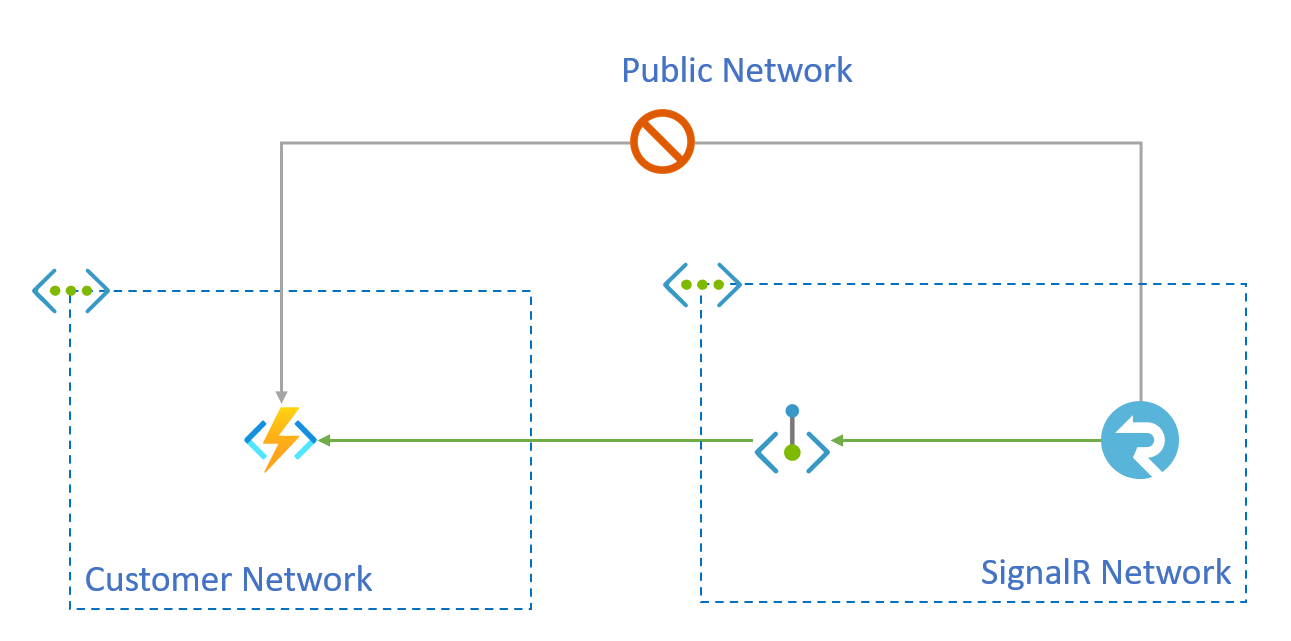
When you're using serverless mode in Azure SignalR Service, you can create outbound private endpoint connections to an upstream service.
Upstream services, such as Azure Web App and Azure Functions, can be configured to accept connections from a list of virtual networks and refuse outside connections that originate from a public network. To reach these endpoints, you can create an outbound private endpoint connection.
This outbound method is subject to the following requirements:
- The upstream service must be Azure Web App or Azure Function.
- The Azure SignalR service not must be on the free tier.
- The Azure Web App or Azure Function must be on certain SKUs. See Use Private Endpoints for Azure Web App.
In this article, you'll learn how to create a shared private endpoint with an outbound private endpoint connection to secure outbound traffic to an upstream Azure Function instance.
Shared Private Link Resources Management
You create private endpoints of secured resources through the SignalR Service APIs. These endpoints, called shared private link resources, allow you to share access to a resource, such as an Azure Function integrated with the Azure Private Link service. These private endpoints are created inside the SignalR Service execution environment and aren't accessible outside this environment.
Prerequisites
You'll need the following resources to complete the steps in this article:
An Azure Resource Group
An Azure SignalR Service instance (must not be in free tier)
An Azure Function instance
-
Note
The examples in this article are based on the following assumptions:
- The resource ID of the SignalR Service is /subscriptions/00000000-0000-0000-0000-000000000000/resourceGroups/contoso/providers/Microsoft.SignalRService/signalr/contoso-signalr.
- The resource ID of upstream Azure Function is /subscriptions/00000000-0000-0000-0000-000000000000/resourceGroups/contoso/providers/Microsoft.Web/sites/contoso-func. The rest of the examples show how the contoso-signalr service can be configured so that its upstream calls to the function go through a private endpoint rather than public network. You may use your own resource IDs in the examples.
Create a shared private link resource to the function
In the Azure portal, go to your SignalR Service resource.
Select Networking with the left menu.
Select the Private access tab.
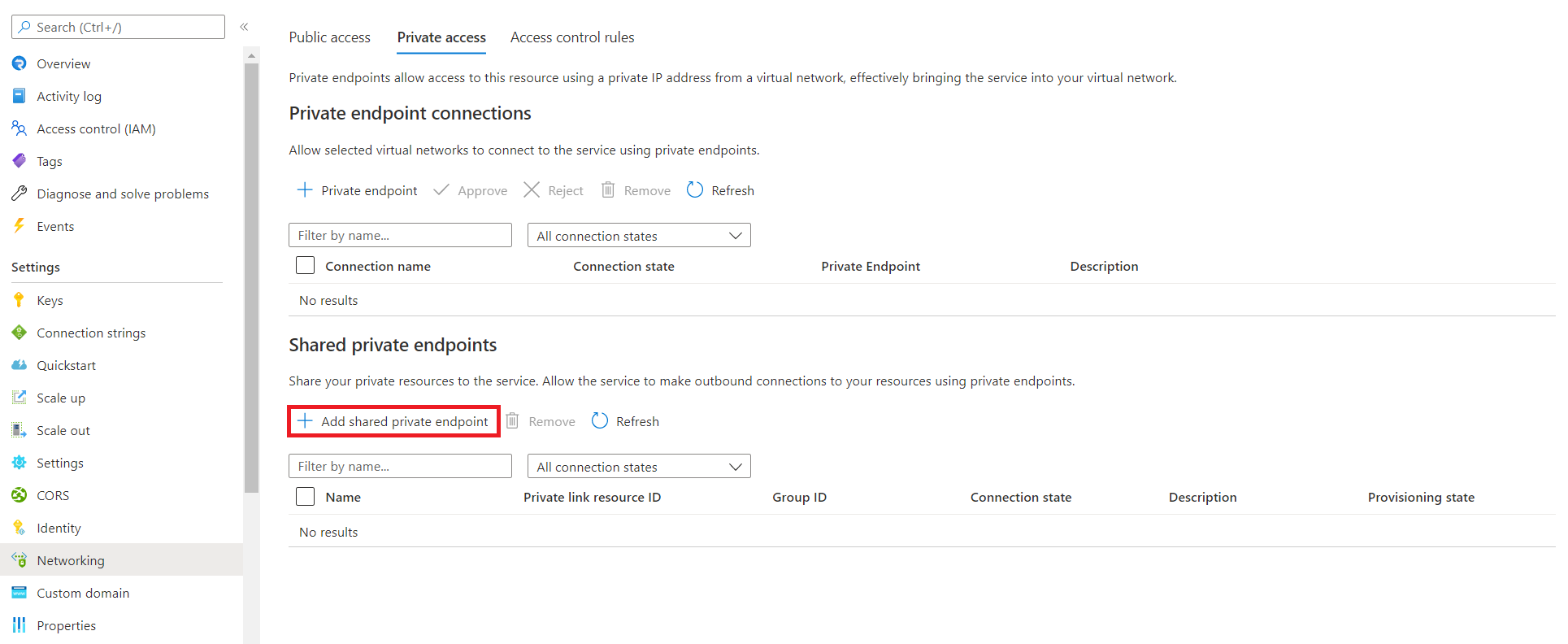
Select Add shared private endpoint in the Shared private endpoints section.
Enter the following information: | Field | Description | | ----- | ----------- | | Name | The name of the shared private endpoint. | | Type | Select Microsoft.Web/sites | | Subscription | The subscription containing your Function app. | | Resource | Enter the name of your Function app. | | Request Message | Enter "please approve" |
Select Add.
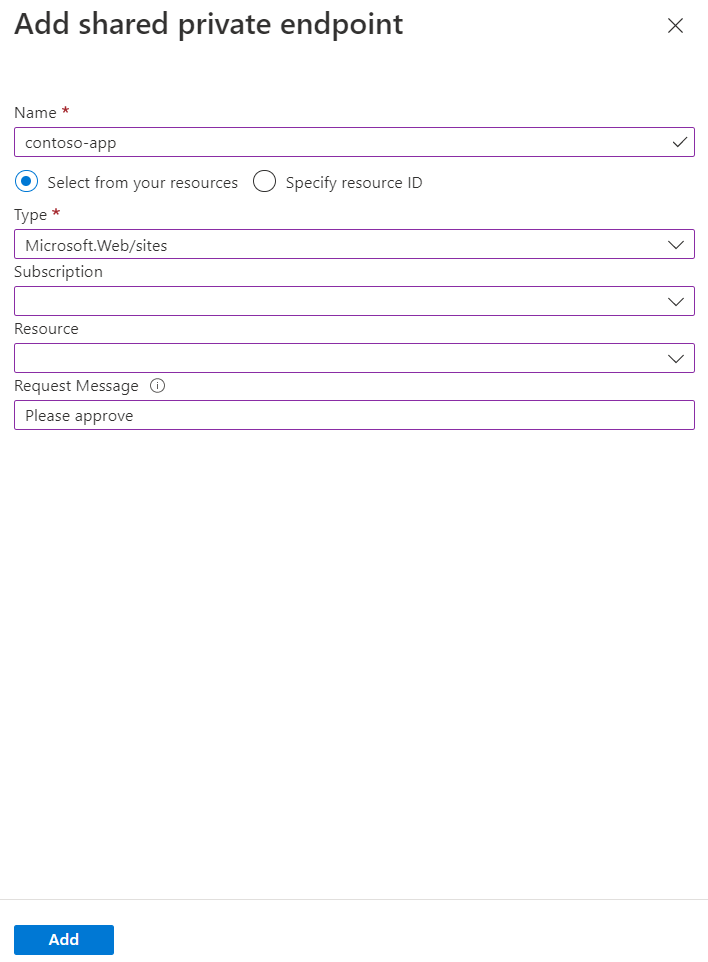
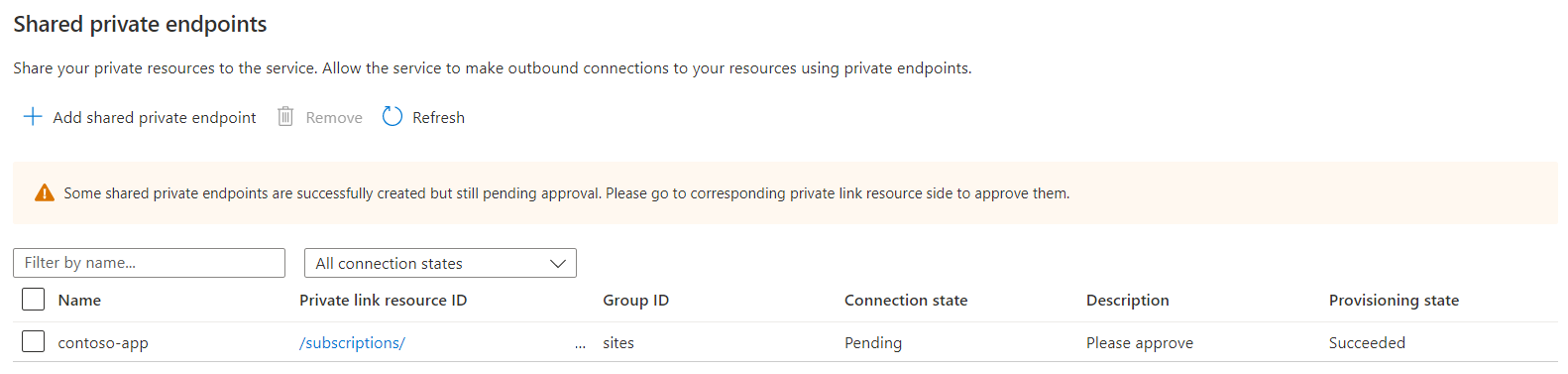
The shared private endpoint resource will be in Succeeded provisioning state. The connection state is Pending approval at target resource side.
Approve the private endpoint connection for the function
Important
After you approve the private endpoint connection, the Function is no longer accessible from a public network. You may need to create other private endpoints in your virtual network to access the Function endpoint.
In the Azure portal, go to your Function app.
Select Networking from the left side menu.
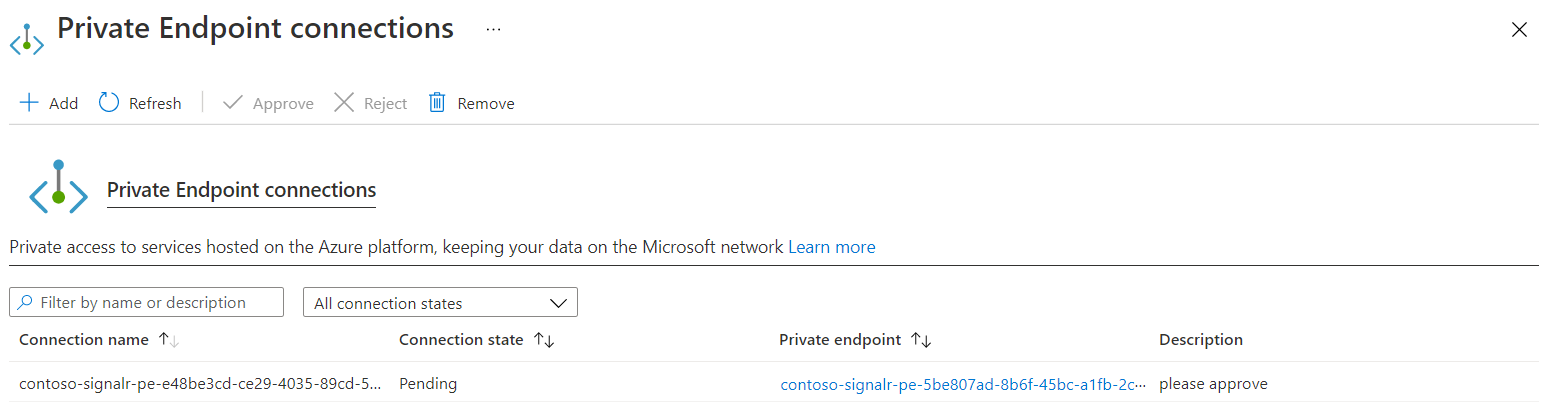
Select Private endpoint connections.
Select Private endpoints in Inbound Traffic.
Select the Connection name of the private endpoint connection.
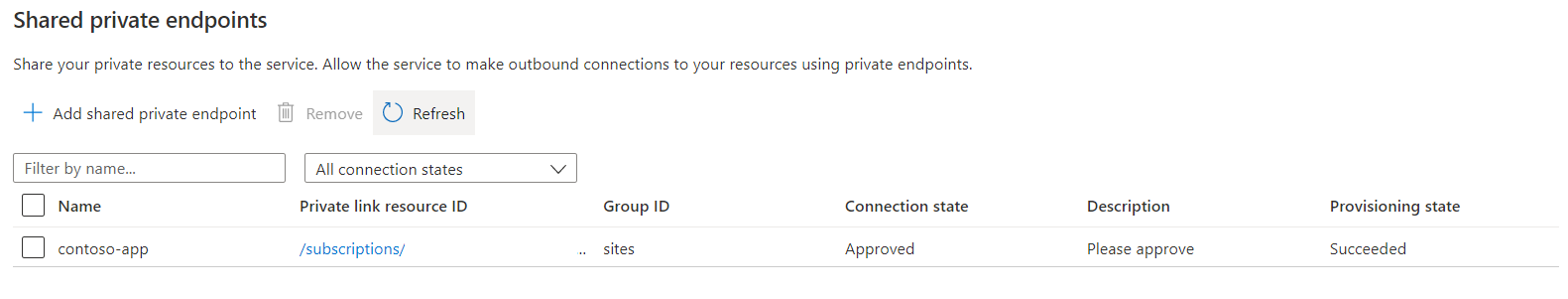
Select Approve.
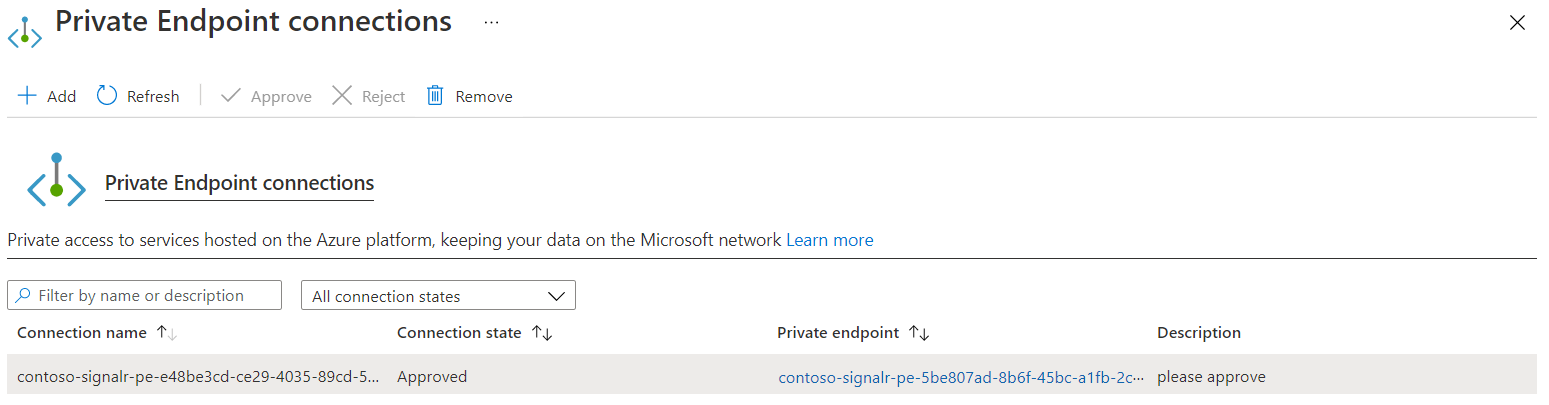
Make sure that the private endpoint connection appears as shown in the following screenshot. It could take a few minutes for the status to be updated.
Query the status of the shared private link resource
The approval takes a few minutes to propagate to the SignalR Service. You can check the state using either the Azure portal or Azure CLI.
At this point, the private endpoint between the SignalR Service and Azure Function is established.
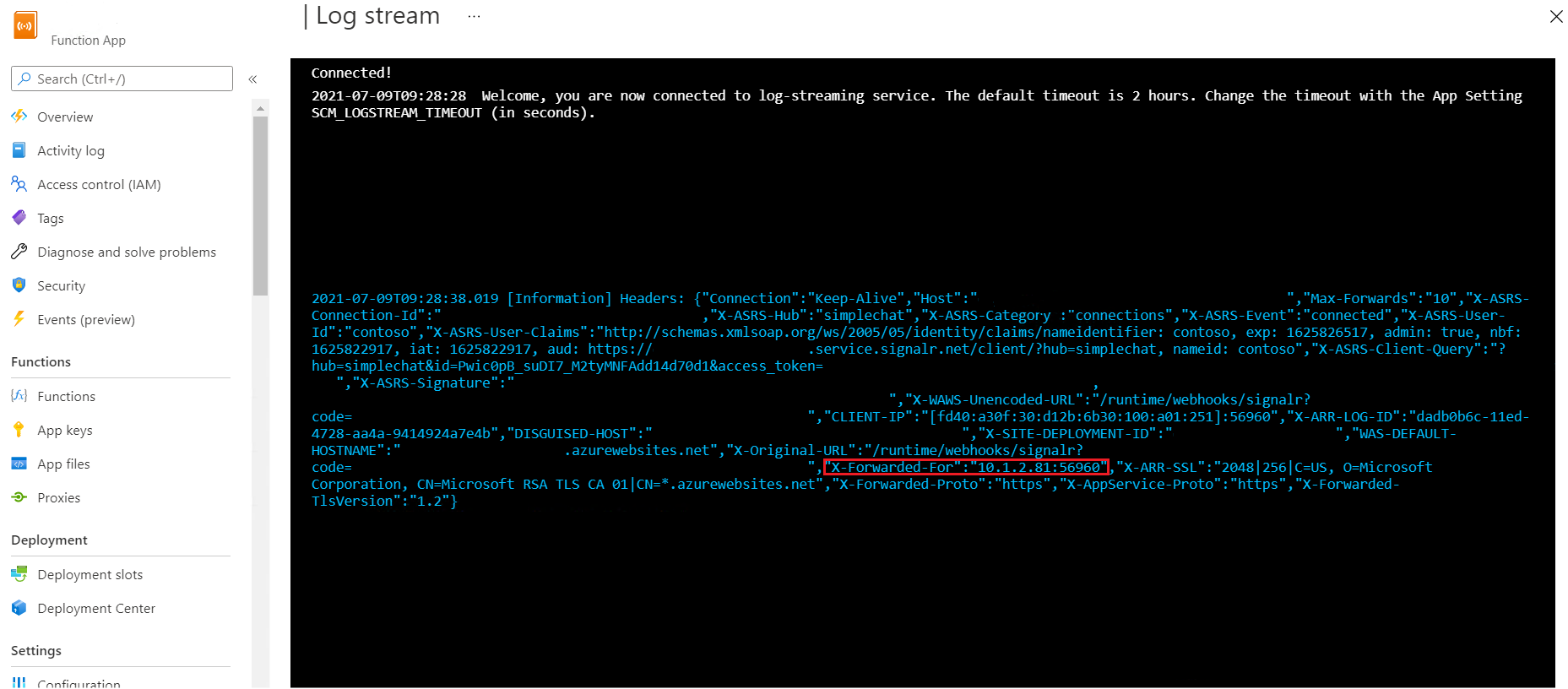
Verify upstream calls are from a private IP
Once the private endpoint is set up, you can verify incoming calls from a private IP by checking the X-Forwarded-For header upstream side.
Cleanup
If you don't plan to use the resources you've created in this article, you can delete the Resource Group.
Caution
Deleting the resource group deletes all resources contained within it. If resources outside the scope of this article exist in the specified resource group, they will also be deleted.
Next steps
Learn more about private endpoints:
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for