Manage Azure policies and deploy the Azure monitoring agent extension to Azure Arc Linux and Windows servers
This article provides guidance on how to use Azure Arc-enabled servers to assign Azure policies to VMs outside of Azure, whether they are on-premises or on other clouds. With this feature you can now use Azure Policy to audit settings in the operating system of an Azure Arc-enabled server, if a setting is not compliant you can also trigger a remediation task.
In this case, you will assign a policy to audit if the Azure Arc-connected machine has the Log Analytics agent installed. If not, use the extensions feature to automatically deploy it to the VM, an enrollment experience that levels to Azure VMs. This approach can be used to make sure all your servers are onboard to services such as Azure Monitor, Microsoft Defender for Cloud, Microsoft Sentinel, and so on.
You can use the Azure portal, an Azure Resource Manager template (ARM template) or PowerShell script to assign policies to Azure subscriptions or resource groups. The following procedures use an ARM template to assign built-in policies.
Important
The procedures in this article assumes you've already deployed VMs, or servers that are running on-premises or on other clouds, and you have connected them to Azure Arc. If you haven't, the following information can help you automate this.
- GCP Ubuntu instance
- GCP Windows instance
- AWS Ubuntu EC2 instance
- AWS Amazon Linux 2 EC2 instance
- VMware vSphere Ubuntu VM
- VMware vSphere Windows Server VM
- Vagrant Ubuntu box
- Vagrant Windows box
Review the Azure Monitor supported OS documentation and ensure that the VMs you use for these procedures are supported. For Linux VMs, check both the Linux distribution and kernel to ensure you are using a supported configuration.
Prerequisites
Clone the Azure Arc Jumpstart repository.
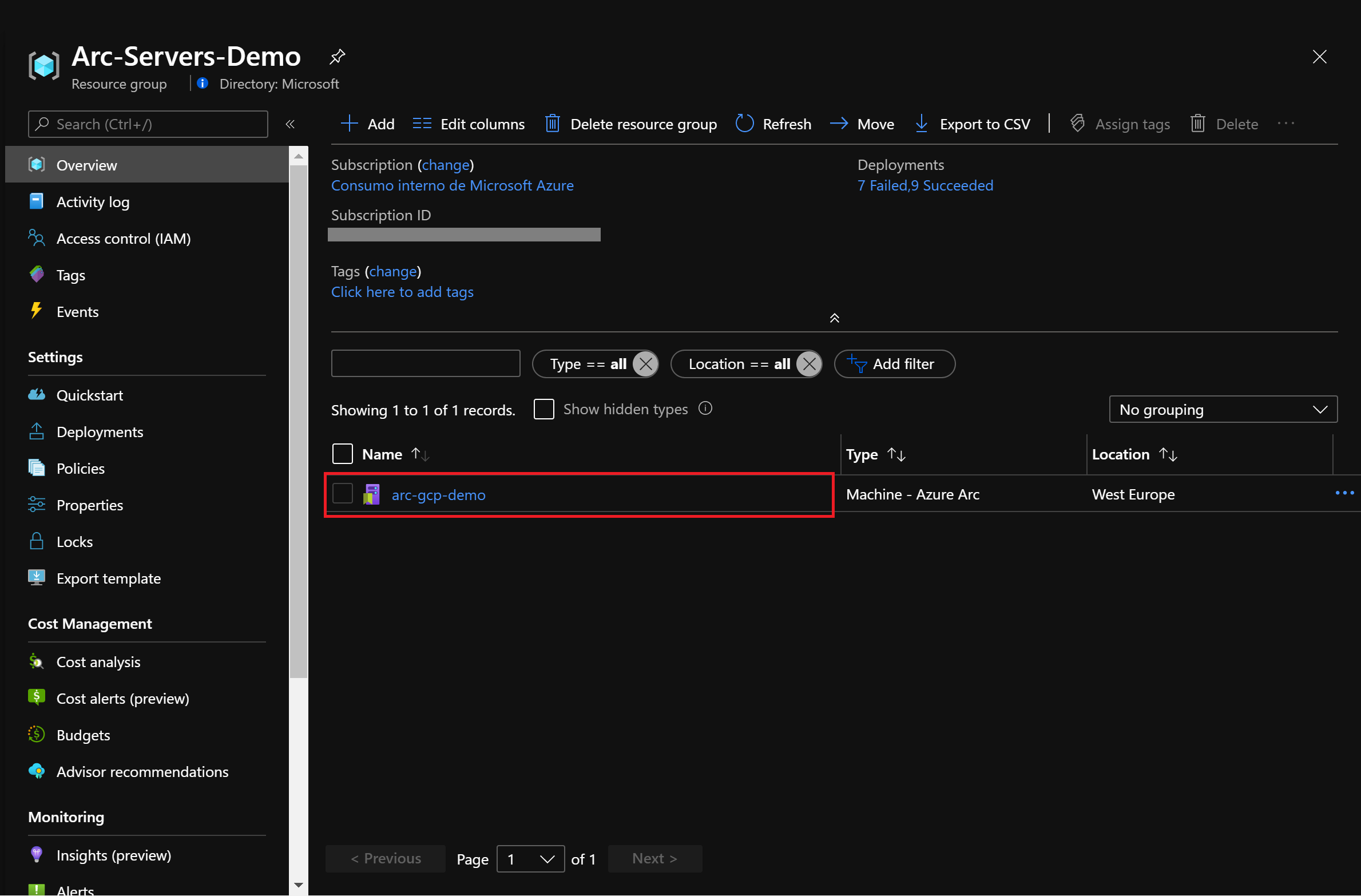
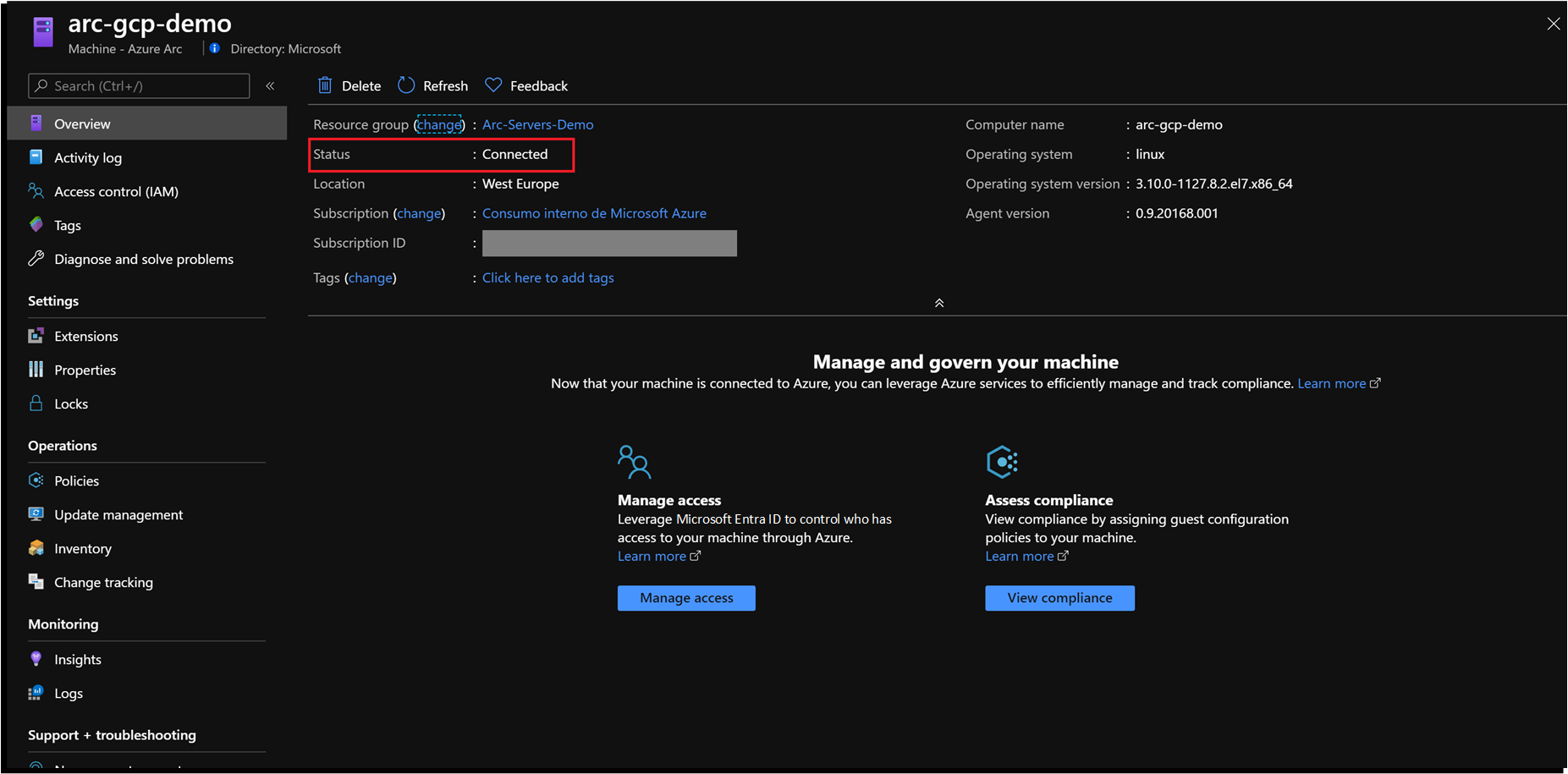
git clone https://github.com/microsoft/azure_arcAs mentioned, this guide starts at the point where you already deployed and connected VMs or servers to Azure Arc. In the following screenshots a Google Cloud Platform (GCP) server has been connected with Azure Arc and is visible as a resource in Azure.
Install or update Azure CLI. Azure CLI should be running version 2.7 or later. Use
az --versionto check your current installed version.Create an Azure service principal.
To connect a VM or bare-metal server to Azure Arc, Azure service principal assigned with the Contributor role is required. To create it, sign in to your Azure account and run the following command. You can also run this command in Azure Cloud Shell.
az login az account set -s <Your Subscription ID> az ad sp create-for-rbac -n "<Unique SP Name>" --role contributor --scopes "/subscriptions/<Your Subscription ID>"For example:
az ad sp create-for-rbac -n "http://AzureArcServers" --role contributor --scopes "/subscriptions/00000000-0000-0000-0000-000000000000"The output should look like this:
{ "appId": "XXXXXXXXXXXXXXXXXXXXXXXXXXXX", "displayName": "http://AzureArcServers", "password": "XXXXXXXXXXXXXXXXXXXXXXXXXXXX", "tenant": "XXXXXXXXXXXXXXXXXXXXXXXXXXXX" }Note
We highly recommend that you scope the service principal to a specific Azure subscription and resource group.
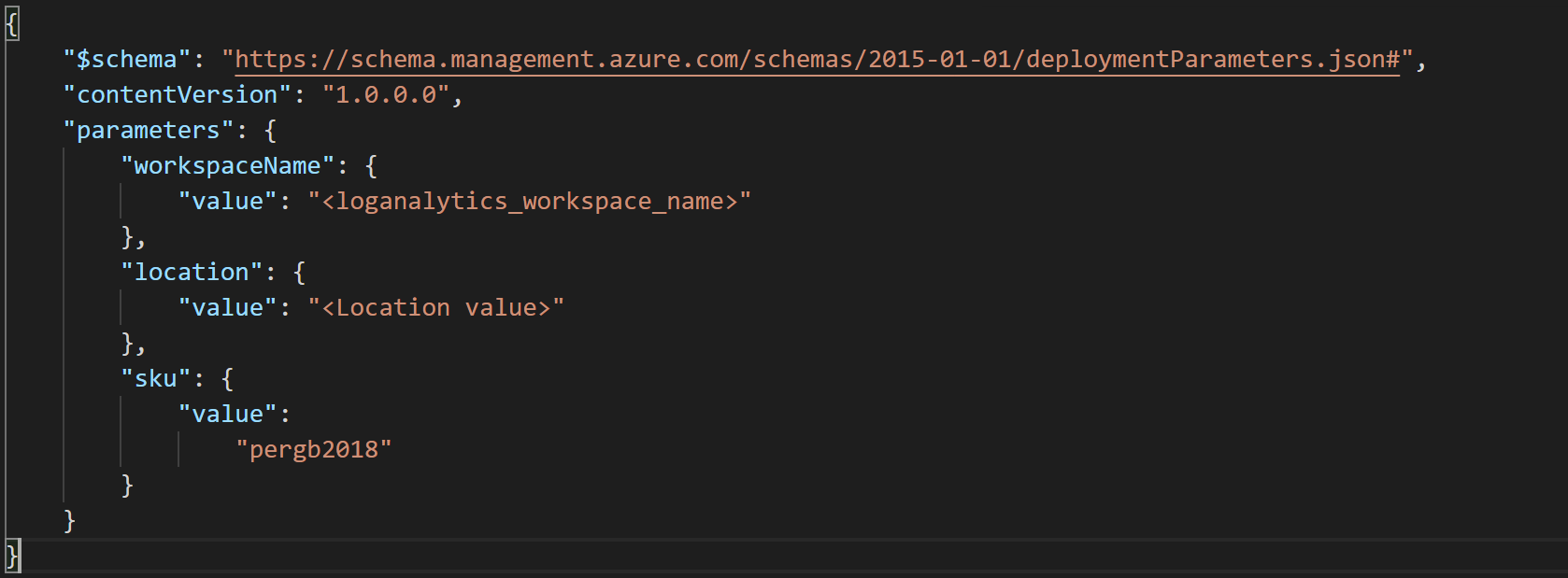
You'll also need to have a Log Analytics workspace deployed. You can automate the deployment by editing the ARM template parameters file and providing a name and location for your workspace.
To deploy the ARM template, navigate to the deployment folder and run the following command:
az deployment group create --resource-group <Name of the Azure resource group> \
--template-file <The `log_analytics-template.json` template file location> \
--parameters <The `log_analytics-template.parameters.json` template file location>
Assign policies to Azure Arc-connected machines
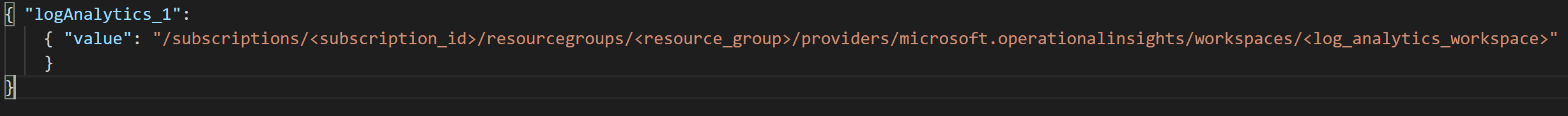
After all the prerequisites are set, you can assign policies to the Azure Arc-connected machines. Edit the parameters file to provide your subscription ID as well as the Log Analytics workspace.
To start the deployment, use the following command:
az policy assignment create --name 'Enable Azure Monitor for VMs' \ --scope '/subscriptions/<Your subscription ID>/resourceGroups/<Name of the Azure resource group>' \ --policy-set-definition '55f3eceb-5573-4f18-9695-226972c6d74a' \ -p <The *policy.json* template file location> \ --assign-identity --location <Azure Region>The
policy-set-definitionflag points to the initiativeEnable Azure Monitordefinition ID.After the initiative is assigned, it takes about 30 minutes for the assignment to be applied to the defined scope. Azure Policy then starts the evaluation cycle against the Azure Arc-connected machine and recognizes it as noncompliant because it still doesn't have the Log Analytics agent configuration deployed. To check this, go to the Azure Arc-connected machine under the Policies section.
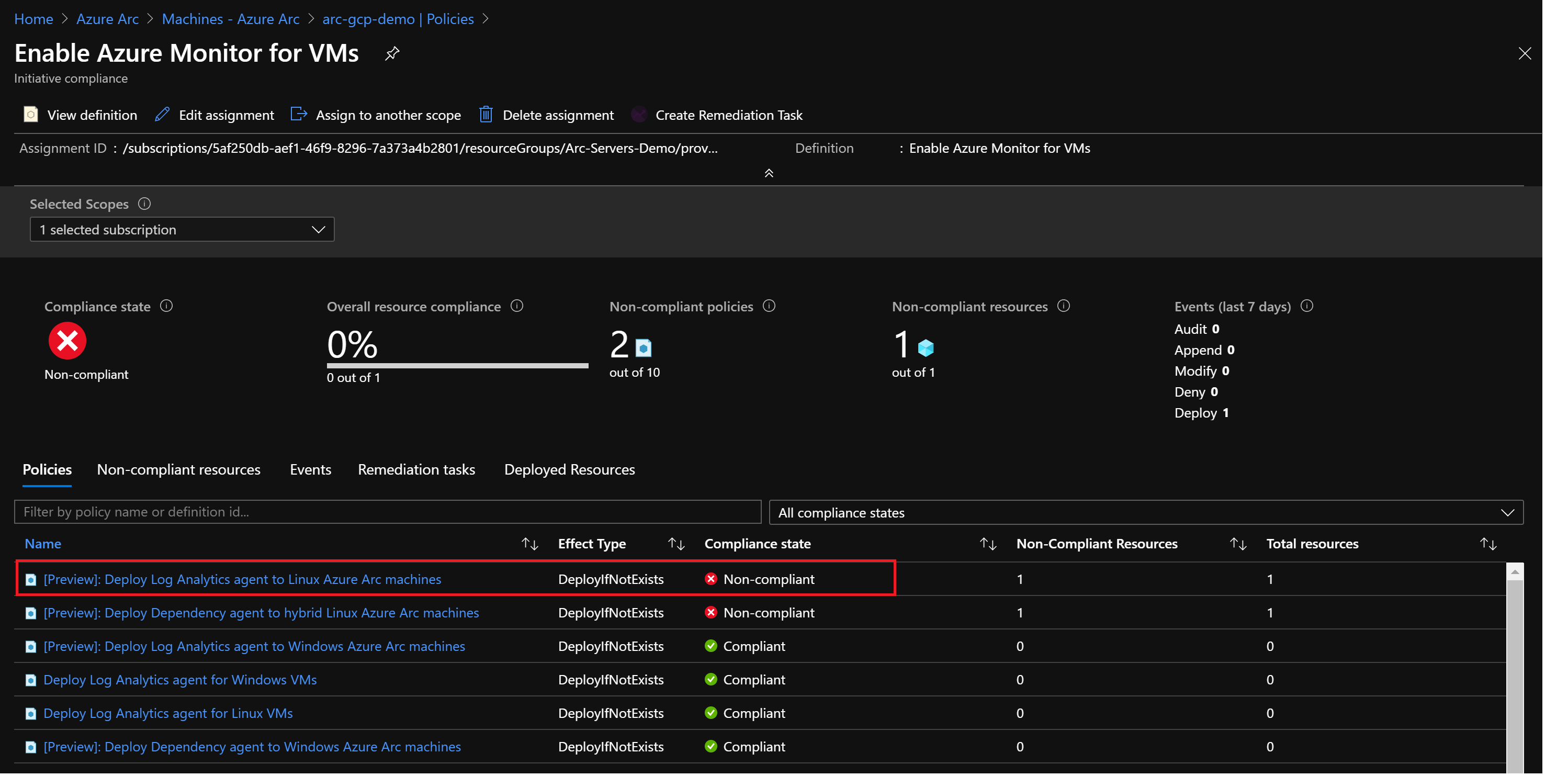
Now, assign a remediation task to the noncompliant resource to put into a compliant state.
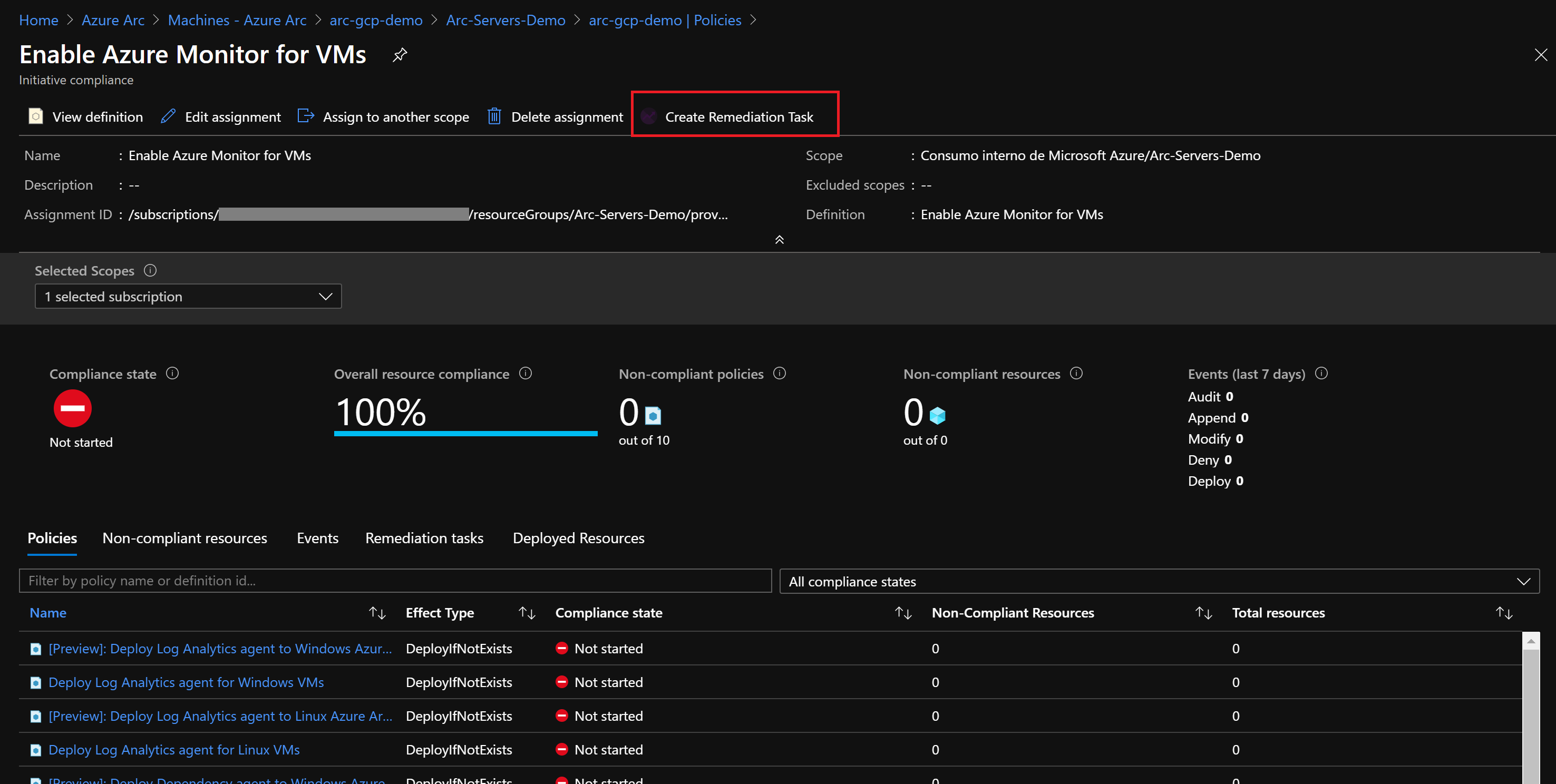
Under Policy to remediate, choose [Preview] Deploy Log Analytics Agent to Linux Azure Arc machines and select Remediate. This remediation task is instructing Azure Policy to run the
DeployIfNotExistseffect and use the Azure Arc extension management capabilities to deploy the Log Analytics agent on the VM.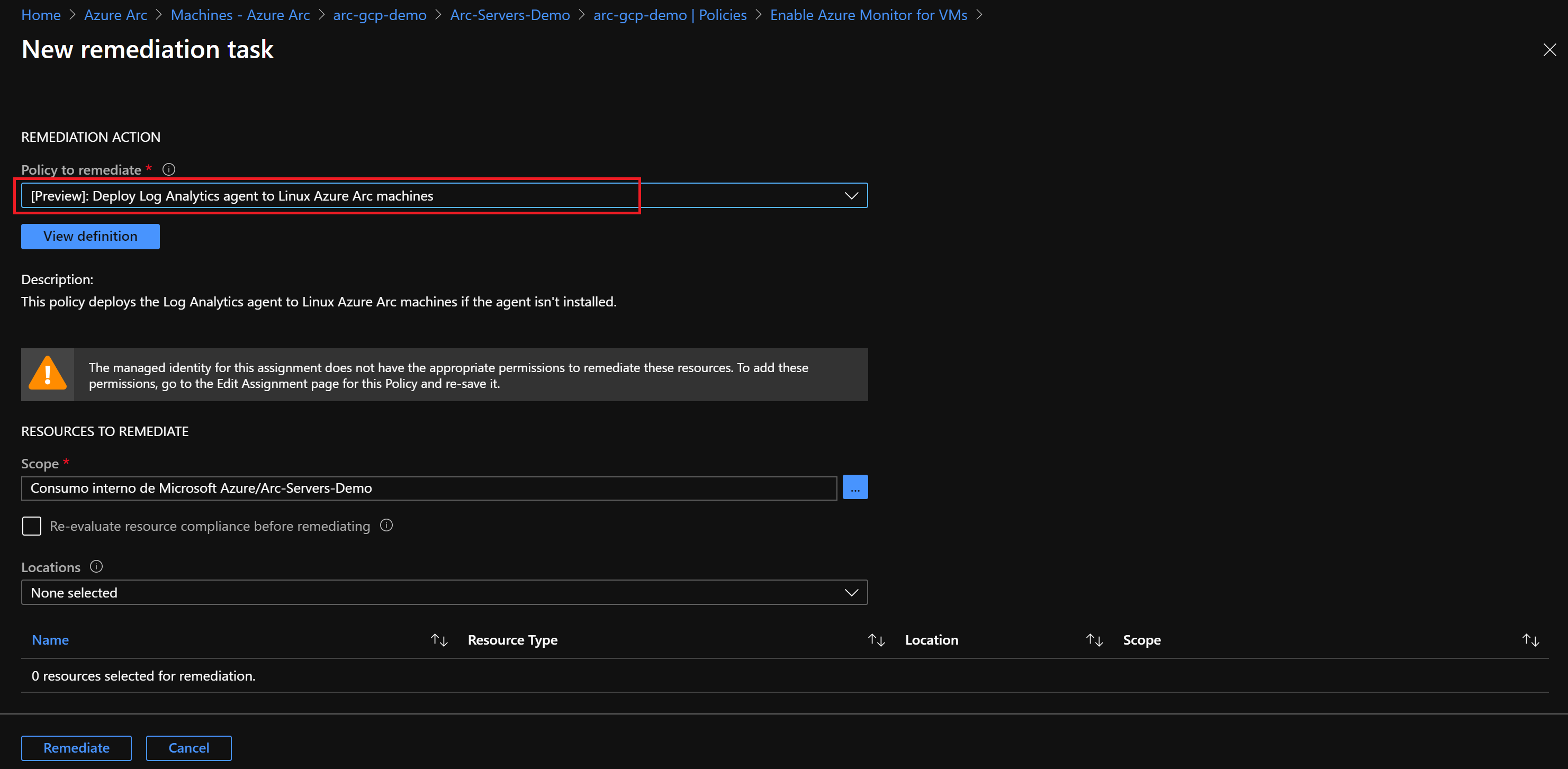
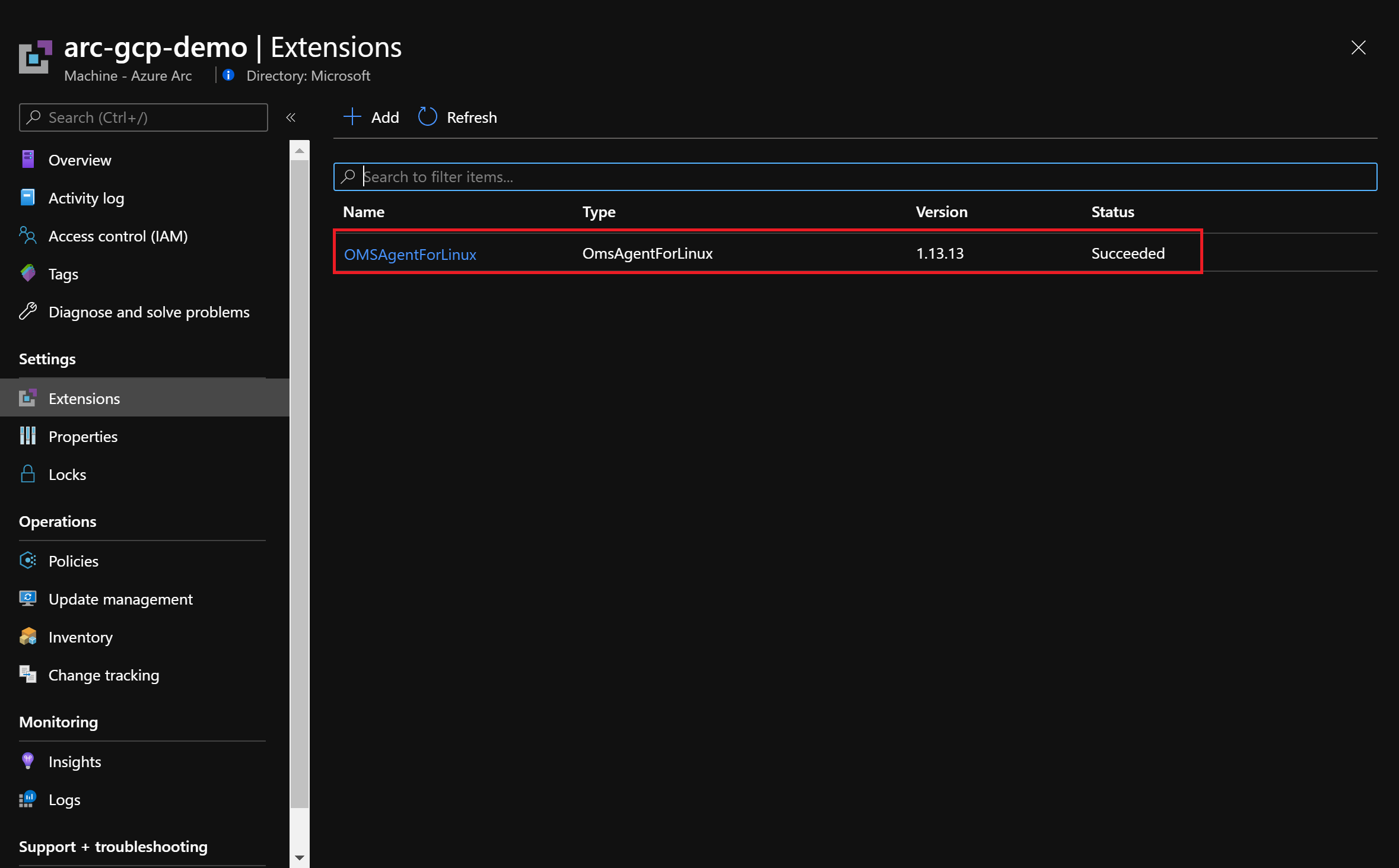
After you have assigned remediation task, the policy will be evaluated again. It should show that the server on GCP is compliant and that the Log Analytics agent is installed on the Azure Arc machine.
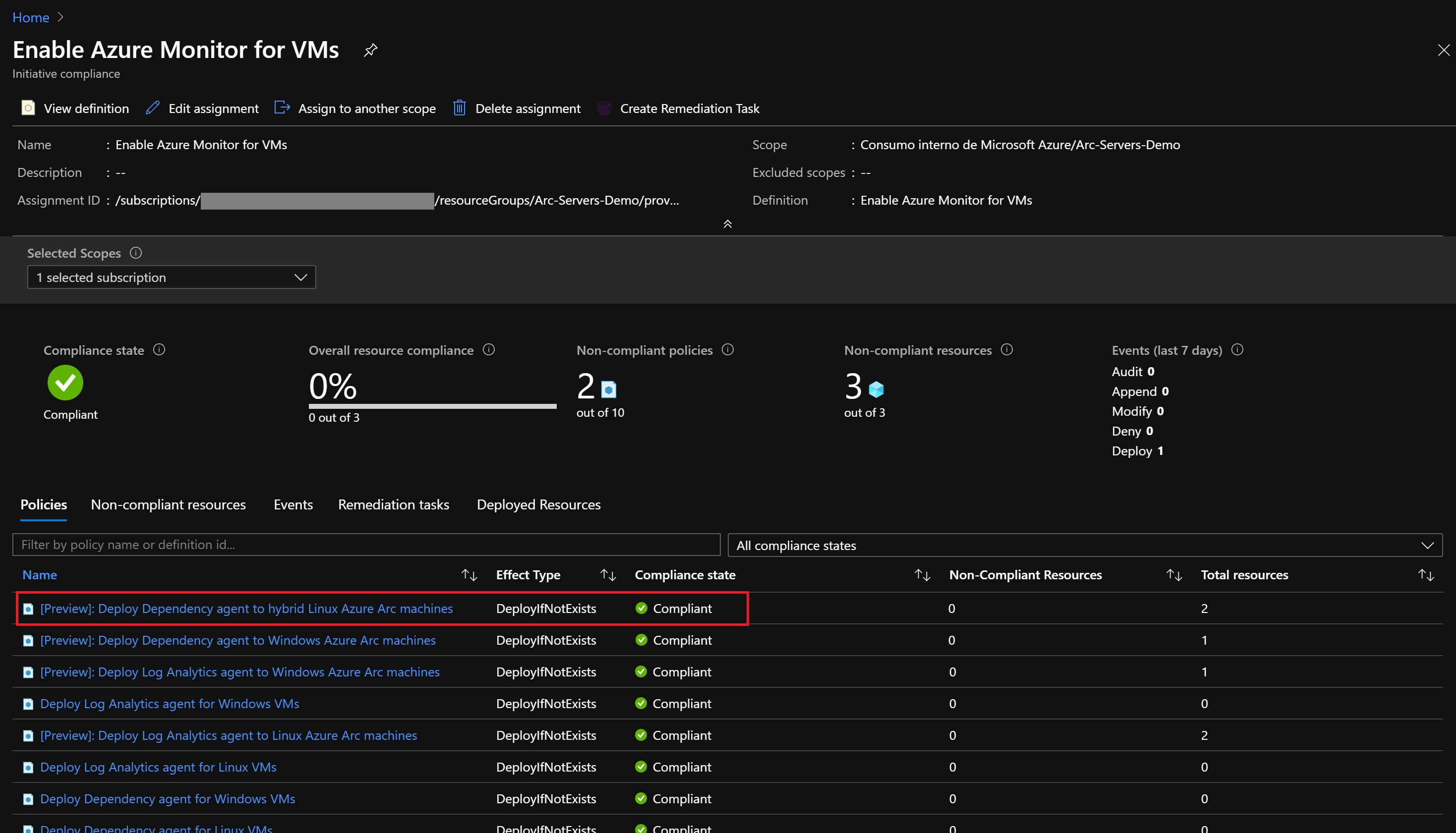
Clean up your environment
Complete the following steps to clean up your environment.
Remove the virtual machines from each environment by following the teardown instructions from each guide.
Remove the Azure Policy assignment by executing the following script in Azure CLI.
az policy assignment delete --name 'Enable Azure Monitor for VMs' --resource-group <resource-group>Remove the Log Analytics workspace by executing the following script in Azure CLI. Provide the workspace name you used when creating the Log Analytics workspace.
az monitor log-analytics workspace delete --resource-group <Name of the Azure resource group> --workspace-name <Log Analytics workspace Name> --yes
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for