Build queries with cloud security explorer
Defender for Cloud's contextual security capabilities assists security teams in reducing the risk of impactful breaches. Defender for Cloud uses environmental context to perform a risk assessment of your security issues, identifies the biggest security risks, and distinguishes them from less risky issues.
Use the cloud security explorer, to proactively identify security risks in your cloud environment by running graph-based queries on the cloud security graph, which is Defender for Cloud's context engine. You can prioritize your security team's concerns, while taking your organization's specific context and conventions into account.
With the cloud security explorer, you can query all of your security issues and environment context such as assets inventory, exposure to internet, permissions, and lateral movement between resources and across multiple clouds (Azure AWS, and GCP).
Prerequisites
You must enable Defender CSPM
- You must enable agentless scanning.
For agentless container posture, you must enable the following extensions:
Note
If you only have Defender for Servers P2 plan 2 enabled, you can use the cloud security explorer to query for keys and secrets, but you must have Defender CSPM enabled to get the full value of the explorer.
Required roles and permissions:
- Security Reader
- Security Admin
- Reader
- Contributor
- Owner
Check the cloud availability tables to see which government and cloud environments are supported.
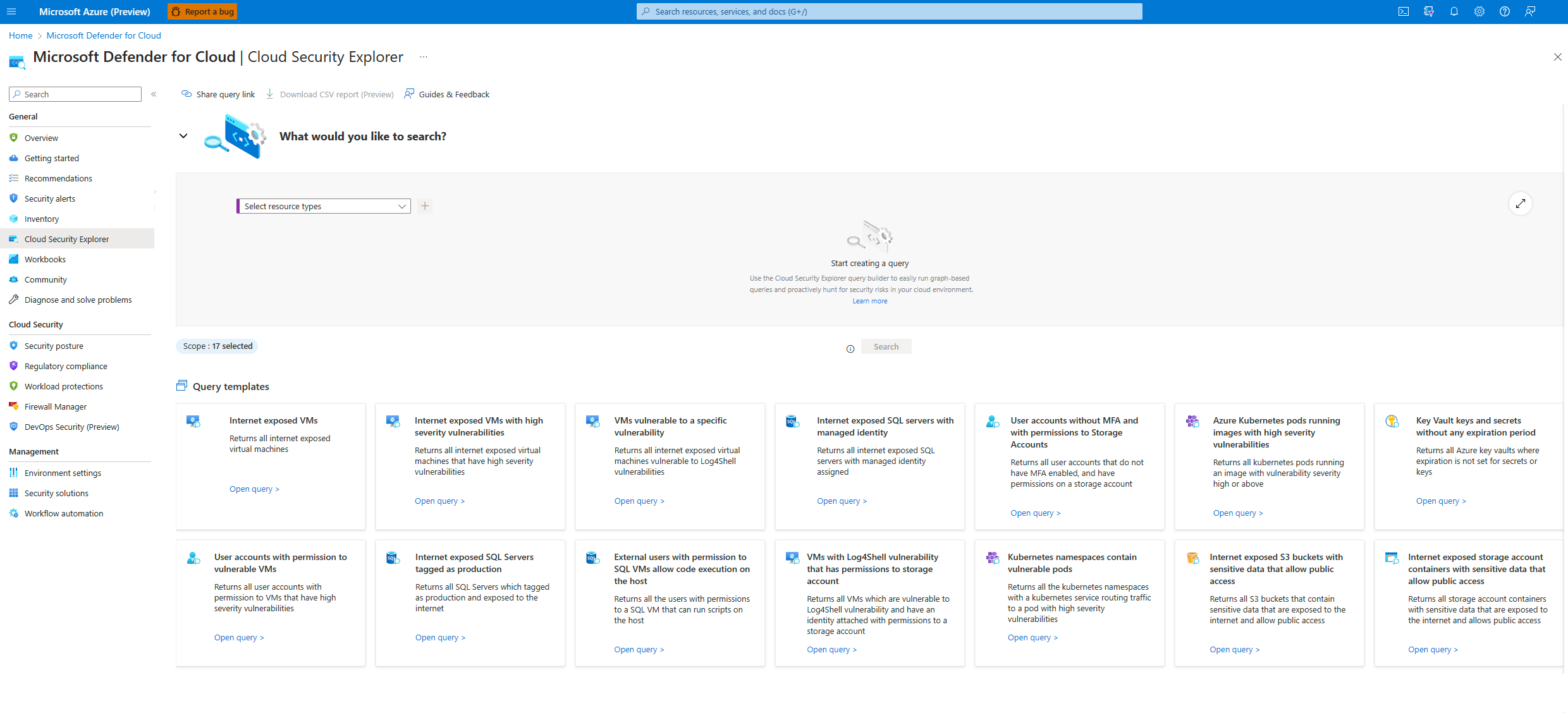
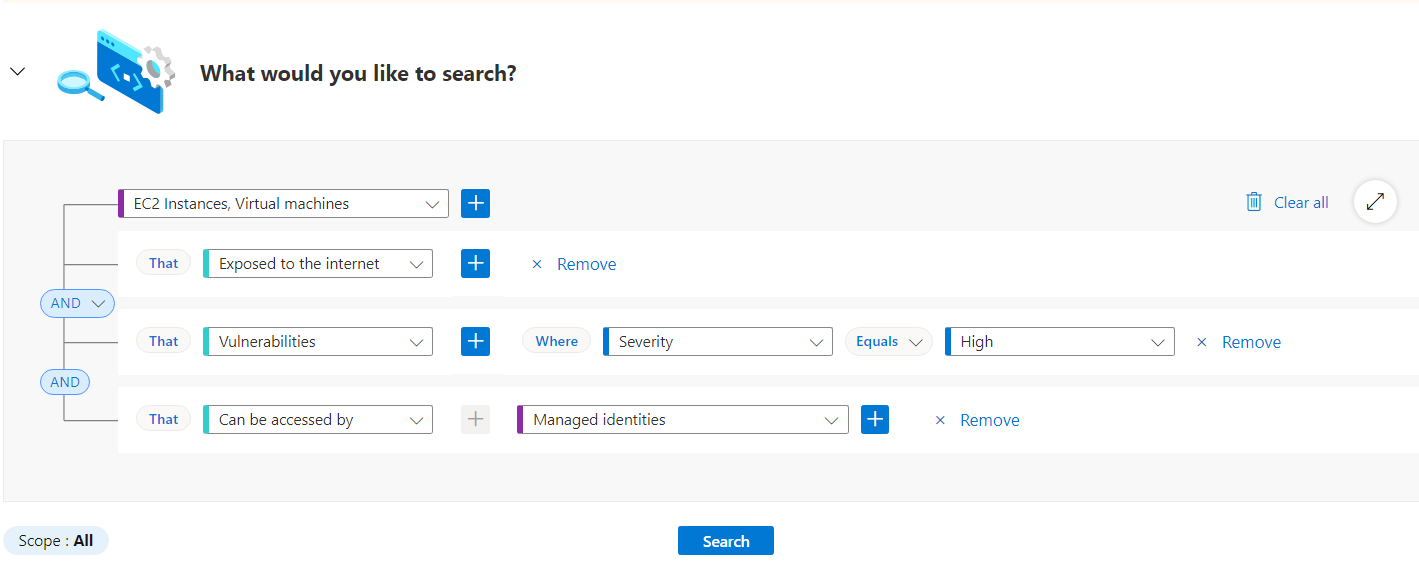
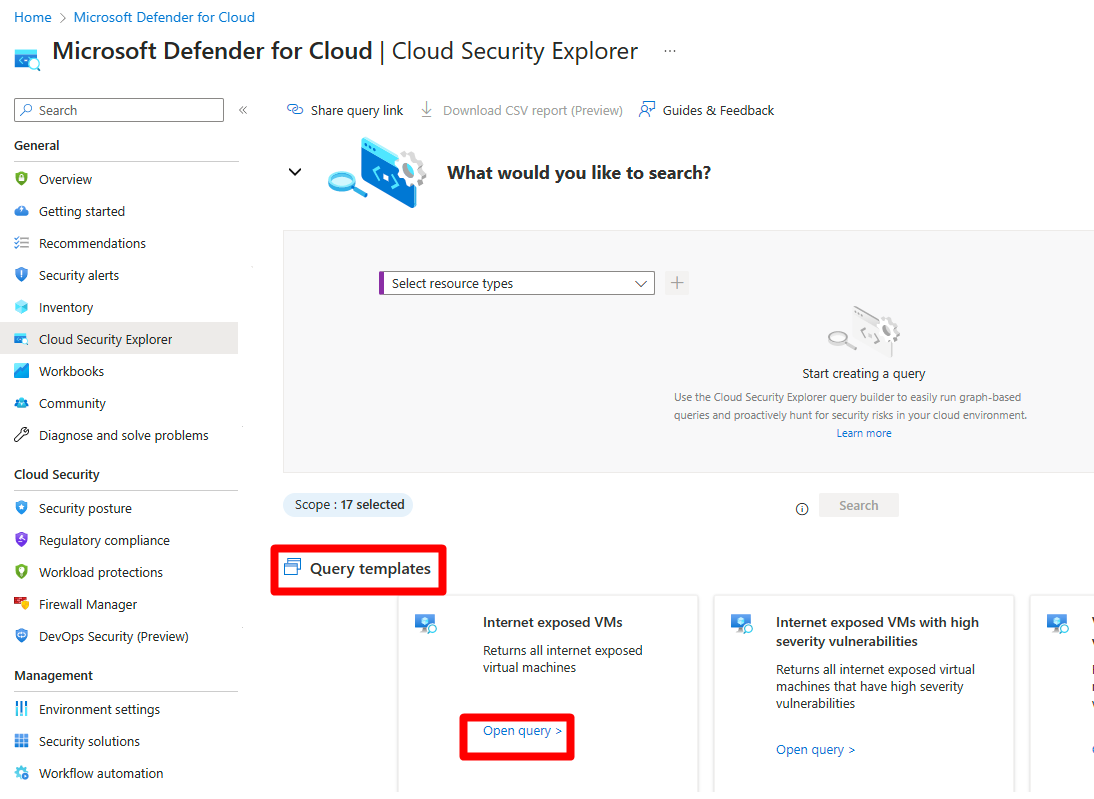
Build a query with the cloud security explorer
The cloud security explorer allows you to build queries that can proactively hunt for security risks in your environments with dynamic and efficient features such as:
Multi-cloud and multi-resource queries - The entity selection control filters are grouped and combined into logical control categories to assist you in building queries across cloud environments and across resources simultaneously.
Custom Search - Use the dropdown menus to apply filters to build your query.
Query templates - Use any of the available prebuilt query templates to more efficiently build your query.
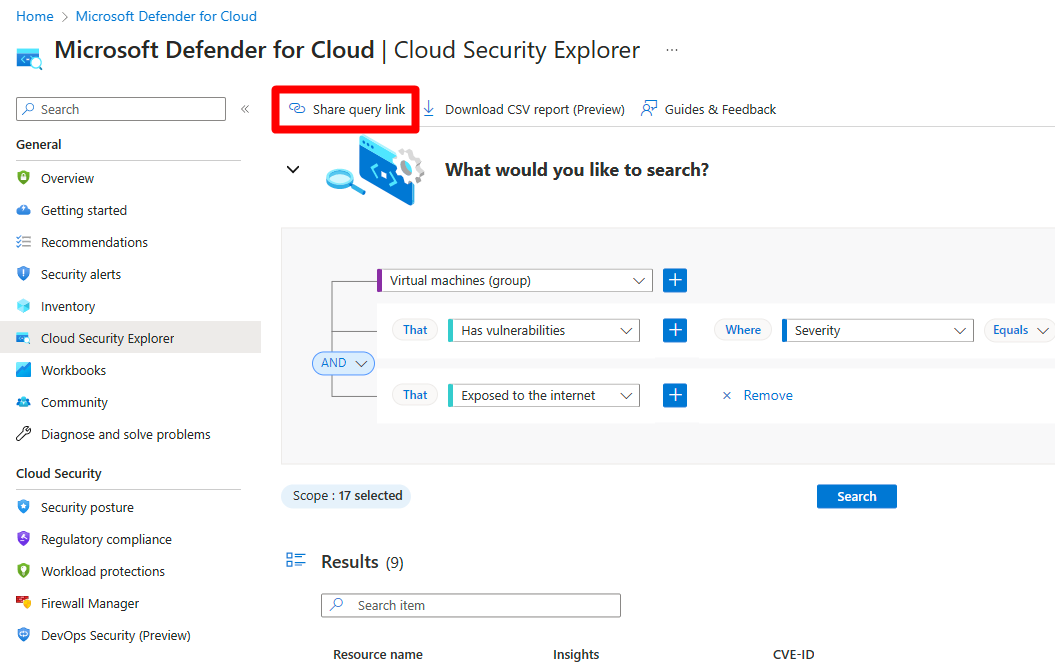
Share query link - Copy and share a link of your query with other people.
To build a query:
Sign in to the Azure portal.
Navigate to Microsoft Defender for Cloud > Cloud Security Explorer.
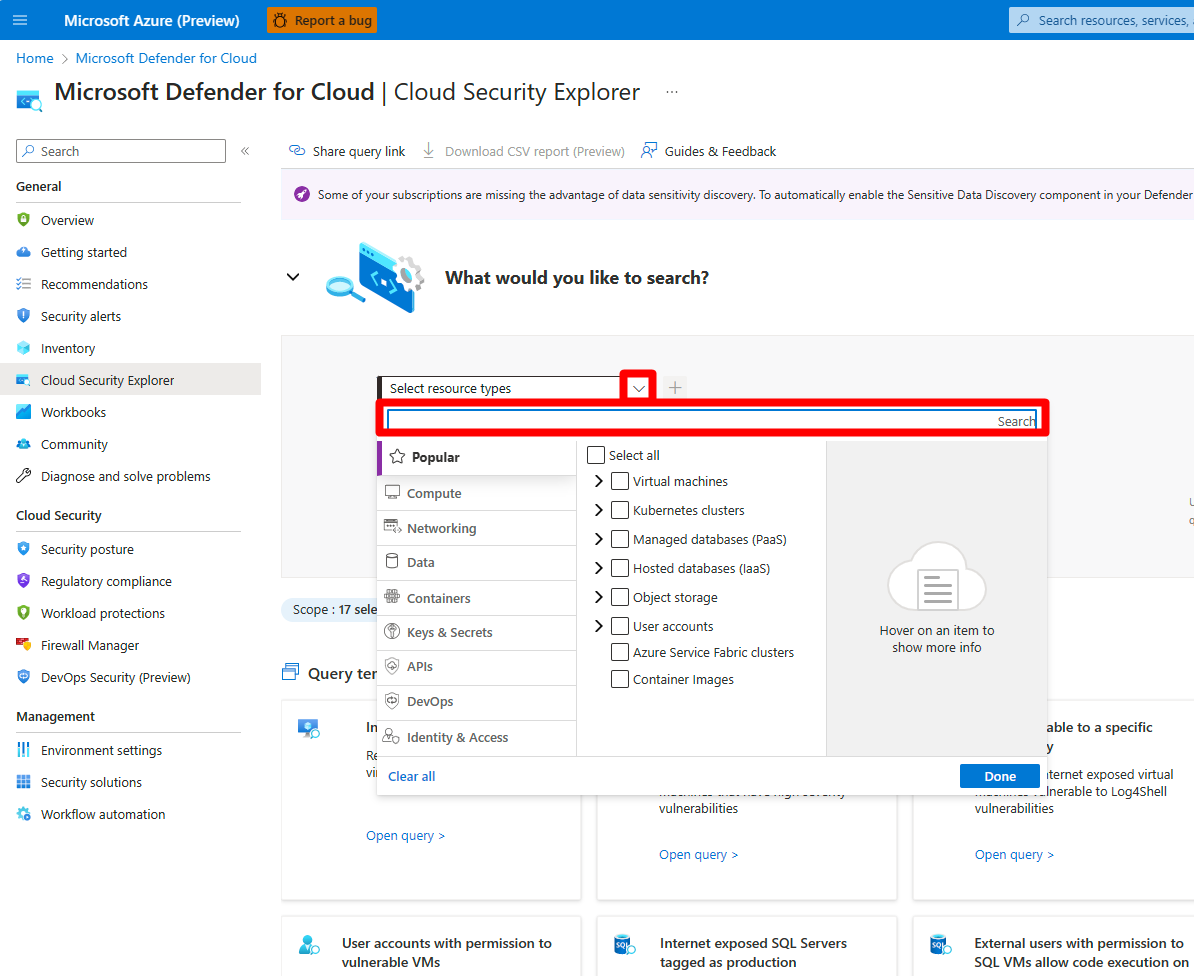
Search for and select a resource from the drop-down menu.
Select + to add other filters to your query.
Add subfilters as needed.
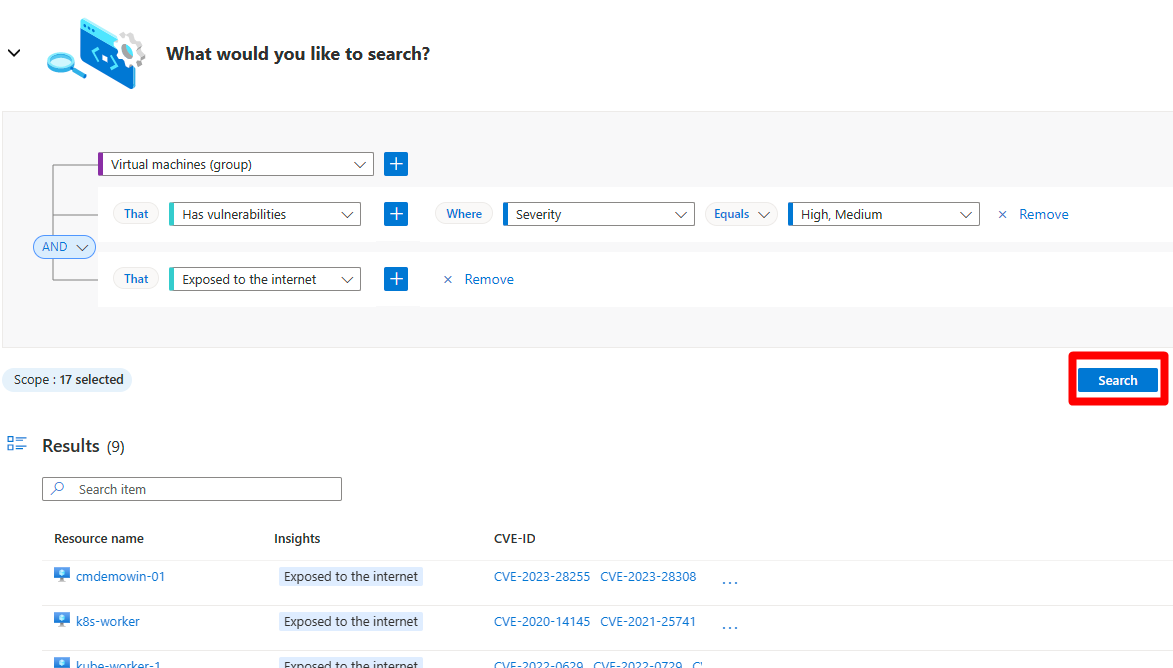
After building your query, select Search to run the query.
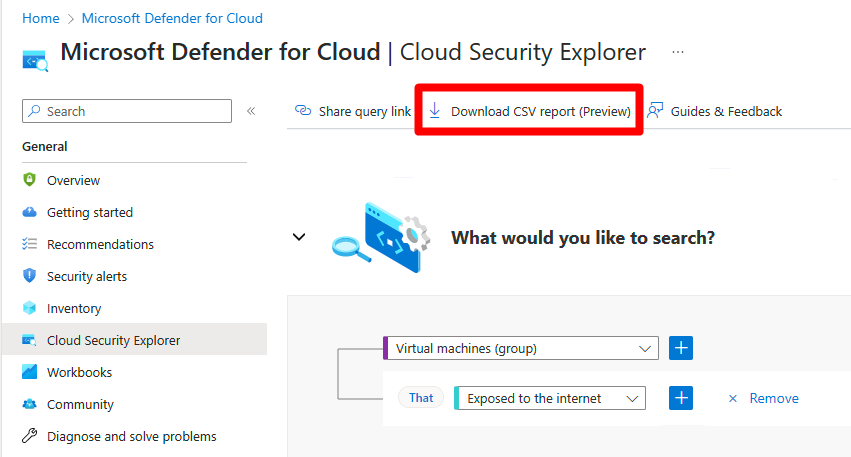
If you want to save a copy of your results locally, you can select the Download CSV report button to save a copy of your search results as a CSV file.
Query templates
Query templates are preformatted searches using commonly used filters. Use one of the existing query templates from the bottom of the page by selecting Open query.
You can modify any template to search for specific results by changing the query and selecting Search.
Share a query
Use the query link to share a query with other people. After creating a query, select Share query link. The link is copied to your clipboard.
Next step
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for