Enhance security posture with security recommendations
Use Microsoft Defender for IoT's security recommendations to enhance your network security posture across unhealthy devices in your network. Lower your attack surface by creating actionable, prioritized mitigation plans that address the unique challenges in OT/IoT networks.
Important
The Recommendations page is currently in PREVIEW. See the Supplemental Terms of Use for Microsoft Azure Previews for additional legal terms that apply to Azure features that are in beta, preview, or otherwise not yet released into general availability.
View security recommendations
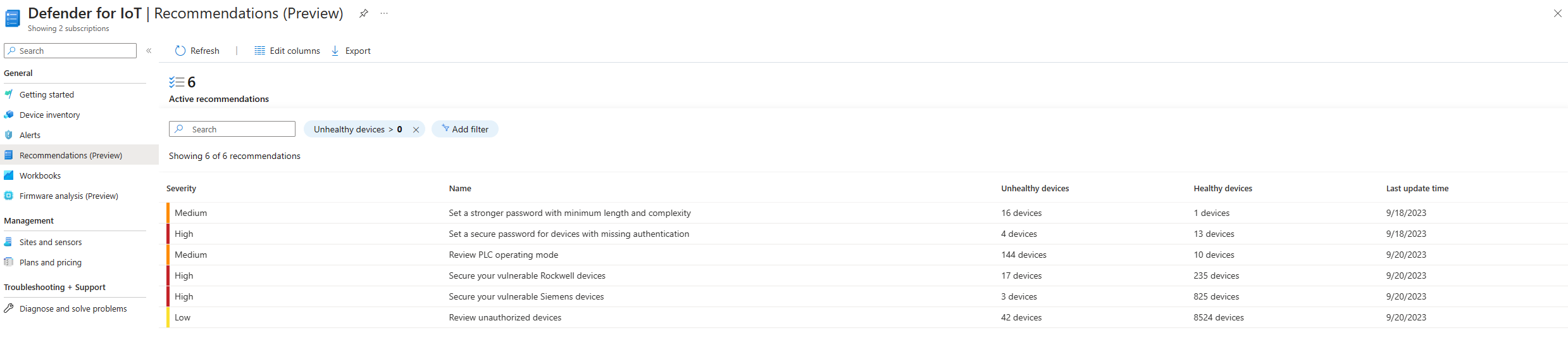
View all current recommendations for your organization on the Defender for IoT Recommendations page on the Azure portal. For example:
The Active recommendations widget indicates the number of recommendations that represent actionable steps you can currently take on unhealthy devices. We recommend reviewing unhealthy devices regularly, taking recommended actions, and keeping the number of active recommendations as low as possible.
Note
Only recommendations that are relevant to your environment are shown in the grid, with at least one healthy or unhealthy device found. You won't see recommendations that aren't related to any devices in your network.
Recommendations are shown in a grid with details in the following columns:
| Column name | Description |
|---|---|
| Severity | Indicates the urgency of the suggested mitigation step. |
| Name | The recommendation's name, which indicates a summary of the suggested mitigation step. |
| Unhealthy devices | The number of detected devices where the recommended step is relevant. |
| Healthy devices | The number of detected devices where the recommended step is covered and no action is required. |
| Last update time | The last time the recommendation was triggered on a detected device. |
Do either of the following to modify the recommendation data listed:
- Select
 Edit columns to add or remove columns from the grid.
Edit columns to add or remove columns from the grid. - Filter the list by entering a keyword from the recommendation name in the Search box, or select Add filter to filter the grid by any of the recommendation columns.
To export a CSV file of all recommendations for your network, select  Export.
Export.
View recommendation details
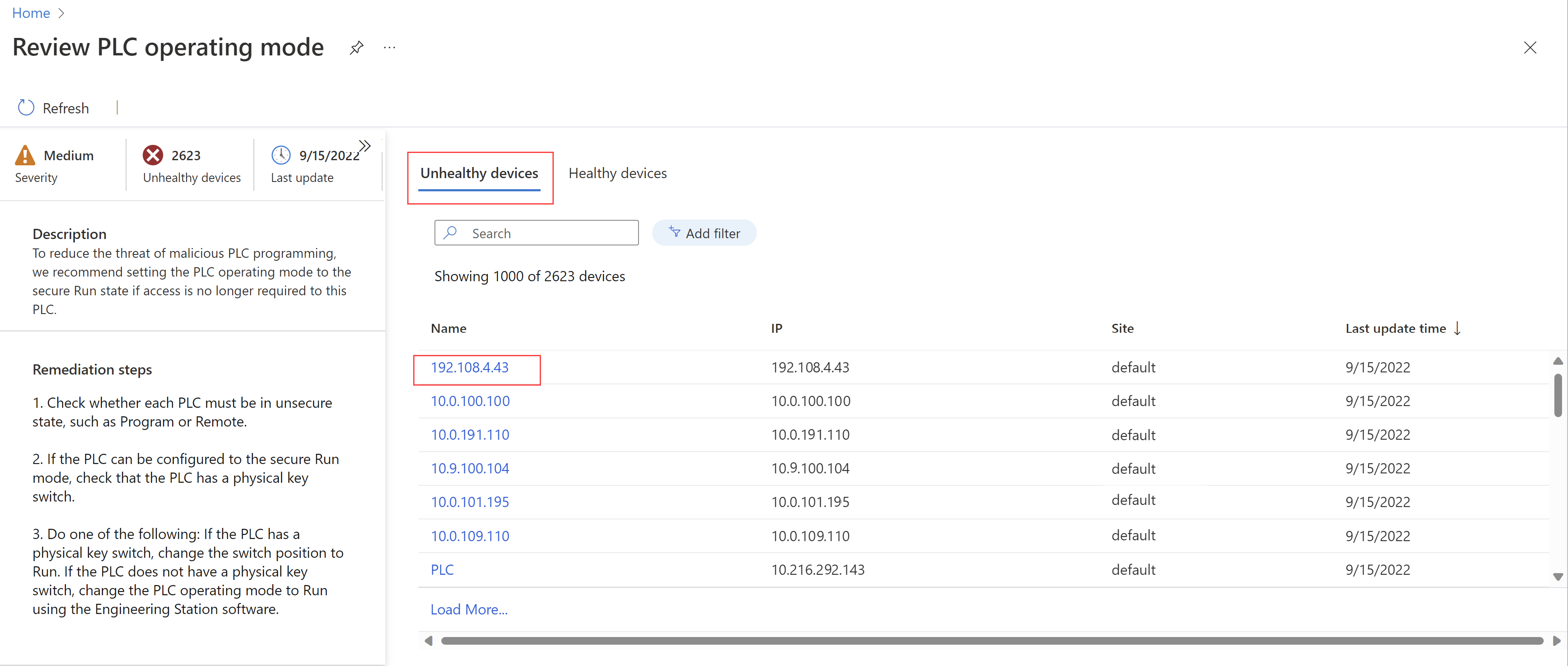
Select a specific recommendation in the grid to drill down for more details. The recommendation name is shown as the page's title. Details with the recommendation's severity, number of unhealthy devices detected, and last update date and time in widgets on the left.
The left pane also shows the following information:
- Description: More context for the recommended mitigation step
- Remediation steps: The full list of mitigation steps recommended for unhealthy devices
Switch between the Unhealthy devices and Healthy devices tabs to review the statuses of detected devices in your network for the selected recommendation.
For example:
View recommendation details by device
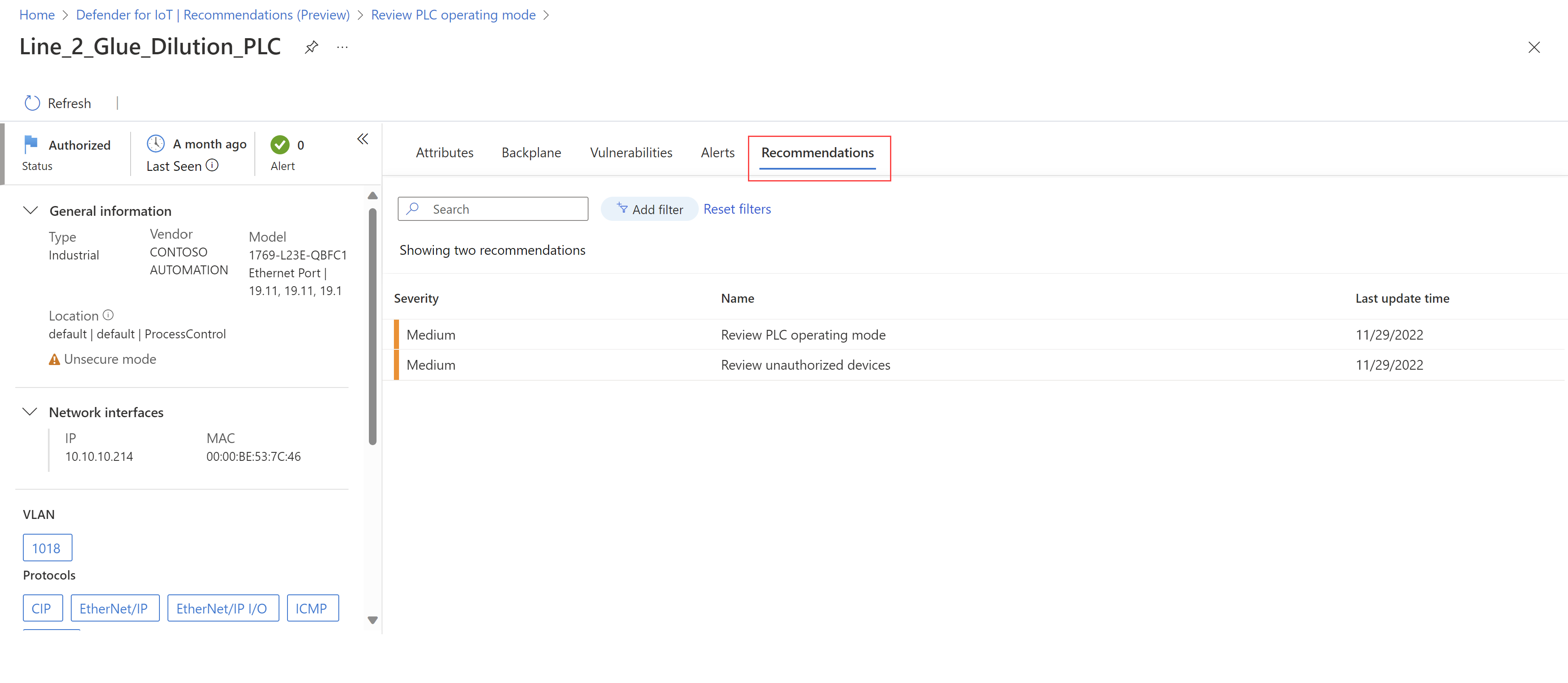
You might want to review all recommendations for a specific device in order to handle them all together.
Recommendations are also listed on the Device details page for each detected device, accessed either from the Device inventory page, or from the list of healthy or unhealthy devices on a recommendation details page.
On a device details page, select the Recommendations tab to view a list of security recommendations specific for the selected device.
For example:
Supported security recommendations
The following recommendations are displayed for OT devices in the Azure portal:
| Name | Description |
|---|---|
| OT network sensors | |
| Review PLC operating mode | Devices with this recommendation are found with PLCs set to unsecure operating mode states. We recommend setting PLC operating modes to the Secure Run state if access is no longer required to the PLC to reduce the threat of malicious PLC programming. |
| Review unauthorized devices | Devices with this recommendation must be identified and authorized as part of the network baseline. We recommend taking action to identify any indicated devices. Disconnect any devices from your network that remain unknown even after investigation to reduce the threat of rogue or potentially malicious devices. |
| Secure your vulnerable <vendor> devices | Devices with this recommendation are found with one or more vulnerabilities with a critical severity and are organized by vendor. We recommend that you follow the steps listed by the device vendor or CISA (Cybersecurity & Infrastructure Agency). To see required remediation steps: 1. Choose a device from the list of unhealthy devices to see its full list of vulnerabilities. 2. From the Vulnerabilities tab, choose the link in the Name column for the critical CVE you're mitigating. Full details are opened in the NVD (National Vulnerability Database). 3. Scroll to the NVD References to Advisories, Solutions, and Tools section and choose any of the listed links for more information. An advisory page opens, either from the vendor or from CISA. 4. Find and perform the remediation steps listed for your scenario. Some vulnerabilities can't be remediated with a patch. |
| Set a secure password for devices with missing authentication | Devices with this recommendation are found without authentication based on successful sign-ins. We recommend that you enable authentication, and that you set a stronger password with minimum length and complexity. |
| Set a stronger password with minimum length and complexity | Devices with this recommendation are found with weak passwords based on successful sign-ins. We recommend that you change the device password to a password that has eight or more characters and that contains characters from 3 of the following categories: - Uppercase letters - Lowercase letters - Special characters - Numbers (0-9) |
| Disable insecure administration protocol | Devices with this recommendation are exposed to malicious threats because they use Telnet, which isn't a secured and encrypted communication protocol. We recommend that you switch to a more secure protocol, such as SSH, disable the server altogether, or apply network access restrictions. |
Other recommendations you may see in the Recommendations page are relevant for the Defender for IoT micro agent.
The following Defender for Endpoint recommendations are relevant for Enterprise IoT customers and are available in Microsoft 365 Defender only:
- Require authentication for VNC management interface
- Disable insecure administration protocol – Telnet
- Remove insecure administration protocols SNMP V1 and SNMP V2
- Require authentication for VNC management interface
For more information, see Security recommendations.
Next steps
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for