Events
Mar 17, 11 PM - Mar 21, 11 PM
Join the meetup series to build scalable AI solutions based on real-world use cases with fellow developers and experts.
Register nowThis browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Azure DevOps Services
This article shows how to connect your Azure DevOps organization to Microsoft Entra ID. You can sign in with the same credentials that you use with Microsoft services. Add members to your Azure DevOps organization who are already a part of your work organization. You can also enforce policies for accessing your team's critical resources and key assets.
For more information about using Microsoft Entra ID with Azure DevOps, see the conceptual overview.
| Category | Requirements |
|---|---|
| Permissions | Member of the Project Collection Administrators group. Organization owners are automatically members of this group. |
| Access levels | - Member in the destination Microsoft Entra ID. For more information, see how to convert a Microsoft Entra guest into a member. - Member or a guest in the source Microsoft Entra ID. |
| User management | - 100 or fewer users in your organization. If your organization has more than 100 users, contact Support to resolve any disconnected users. You can map them to their Microsoft Entra identities in the new tenant. - Don't add the users from the destination Microsoft Entra ID into the Azure DevOps organization. - Delete unwanted users from your organization. For example, you can remove a user who left the company and is no longer an employee. - Inform users of the upcoming change. There's no downtime during this change, but users are affected. Let them know before you begin that there's a short series of steps they need to complete. As your company transitions from Microsoft account (MSA) to Microsoft Entra identities, your users' benefits continue with their new identity, as long as their emails match. - Compare your Azure DevOps email list with your Microsoft Entra ID email list. Create a Microsoft Entra ID email address entry for every user who's in the Azure DevOps organization and not in the Microsoft Entra ID. Afterward, you can invite users as guests who don't have Microsoft Entra ID email addresses. |
| SSH keys | Request that SSH keys get manually cleared by Support before you switch directories. Find the steps for how to recreate SSH keys further in this article. For more information, see the FAQ. |
Note
Ensure you're using Microsoft Entra Public. Connecting Azure DevOps Services organizations to Microsoft Entra Government and accessing Azure DevOps Services with user accounts from Microsoft Entra Government isn't supported.
To connect your organization to Microsoft Entra ID, do the following steps:
Sign in to your organization (https://dev.azure.com/{yourorganization}).
Select ![]() Organization settings.
Organization settings.
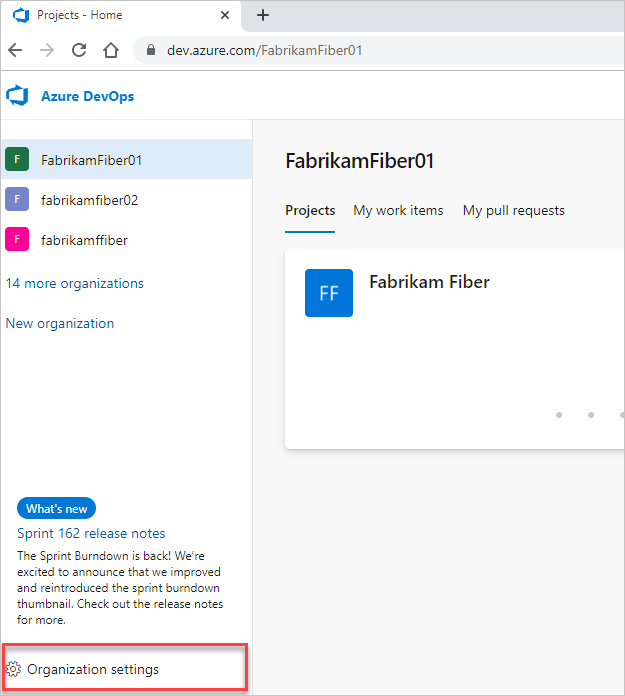
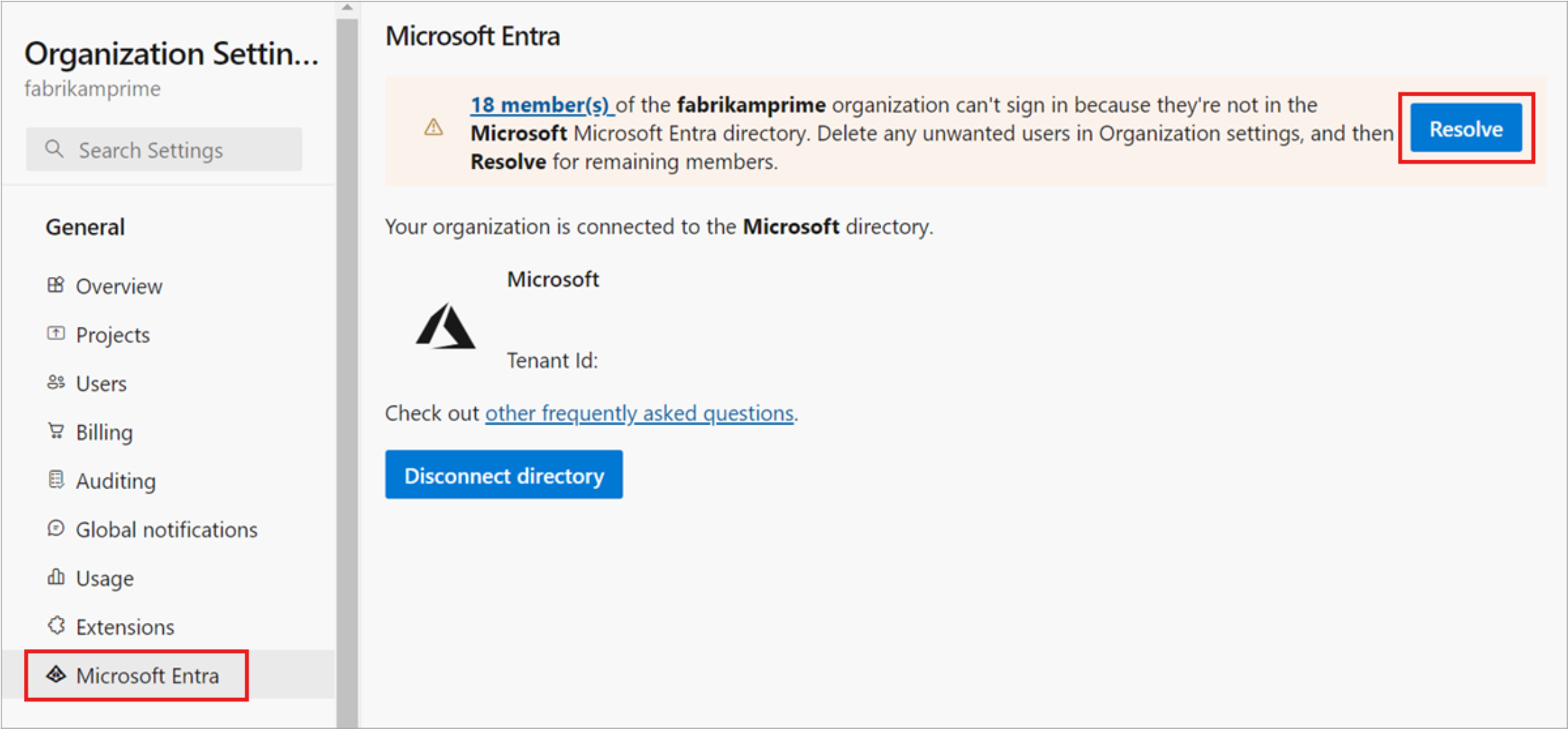
Select Microsoft Entra ID, and then select Connect directory.
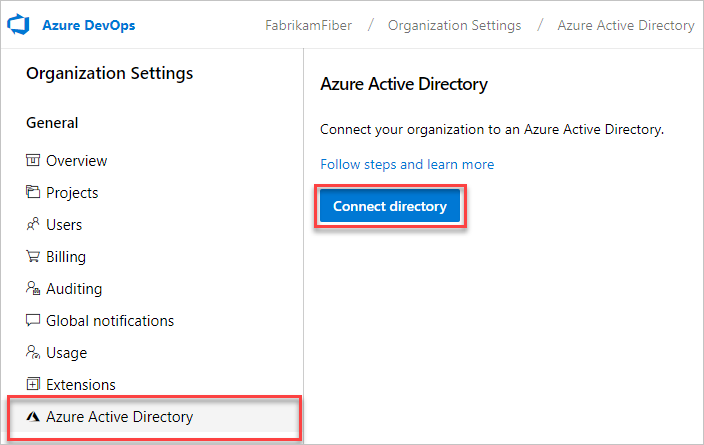
Select a directory from the dropdown menu, and then select Connect.
If you can't find your directory, contact your Microsoft Entra administrator and request that they add you as a member to the Microsoft Entra ID.
Select Sign out.
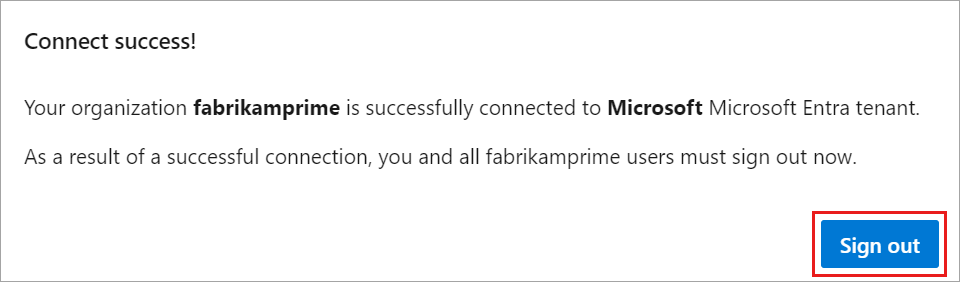
Your organization is connected to your Microsoft Entra ID.
Confirm that the process is complete. Sign out, and then open your browser in a private session and sign in to your organization with your Microsoft Entra ID or work credentials.
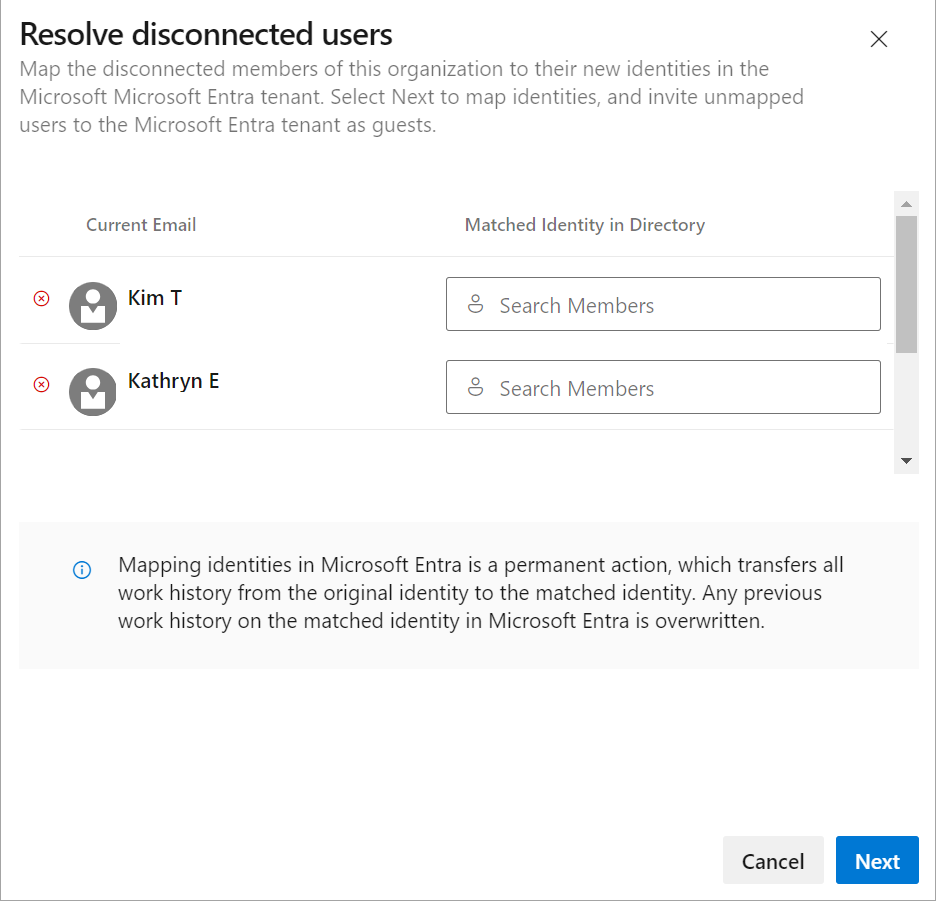
Sign back in to Azure DevOps and map any disconnected members to their Microsoft Entra identities. Or, you can invite them as guests into the Microsoft Entra ID. For more information, see the FAQs.
When you inform your users of the completed change, provide them with the following tasks to do:
Sign out of Azure DevOps.
Clear browser cache. If you use Visual Studio or the Git command-line too, clear the cache for the Git Credential Manager. Delete the %LocalAppData%\GitCredentialManager\tenant.cache file on each client machine.
Sign in to Azure DevOps using Microsoft Entra ID or work credentials.
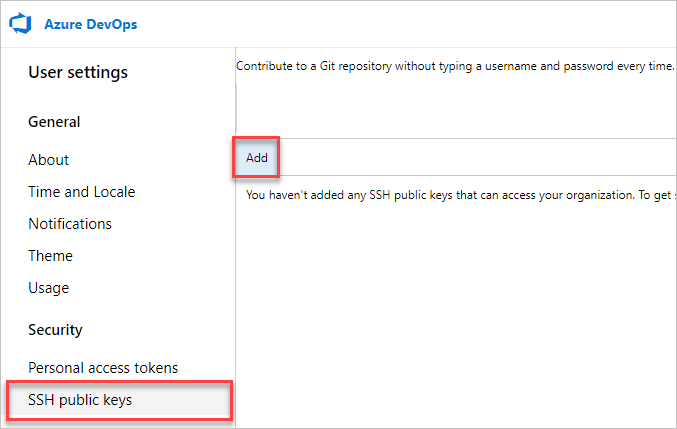
Reconfigure any personal access tokens (PATs) or SSH keys, if necessary.

Rename your Microsoft account (MSA). Rename your MSA to a different email that doesn't conflict with your Microsoft Entra identity. Doing so ensures that you aren't prompted to choose between accounts.
(Optional) Adjust your visual Studio (VS) subscription. If the UPN used inside your organization changed, adjust your Visual Studio subscription. You can reassign the subscription to your new UPN, or set that UPN as the alternate account inside the subscription. For more information, see how to add an alternate account to your subscription.
Events
Mar 17, 11 PM - Mar 21, 11 PM
Join the meetup series to build scalable AI solutions based on real-world use cases with fellow developers and experts.
Register nowTraining
Module
Explore Microsoft Entra ID - Training
This module introduces students to the concepts of Microsoft Entra ID.
Certification
Microsoft Certified: Identity and Access Administrator Associate - Certifications
Demonstrate the features of Microsoft Entra ID to modernize identity solutions, implement hybrid solutions, and implement identity governance.
Documentation
Access via Microsoft Entra FAQs
Learn the answers to frequently asked questions (FAQs), like how to understand Microsoft Entra groups, add users, connect to, disconnect from, or switch your directory.
Access your organization with Microsoft Entra ID - Azure DevOps Services
About user authentication, and controlling conditional access to your organization with a Microsoft Entra tenant.
Manage access with Microsoft Entra groups - Azure DevOps Services
Learn how to control who can access Azure DevOps with Microsoft Entra groups