Use Azure Firewall policy to define a rule hierarchy
Security administrators need to manage firewalls and ensure compliance across on-premises and cloud deployments. A key component is the ability to provide application teams with flexibility to implement CI/CD pipelines to create firewall rules in an automated way.
Azure Firewall policy allows you to define a rule hierarchy and enforce compliance:
- Provides a hierarchical structure to overlay a central base policy on top of a child application team policy. The base policy has a higher priority and runs before the child policy.
- Use an Azure custom role definition to prevent inadvertent base policy removal and provide selective access to rule collection groups within a subscription or resource group.
Solution overview
The high-level steps for this example are:
- Create a base firewall policy in the security team resource group.
- Define IT security-specific rules in the base policy. This adds a common set of rules to allow/deny traffic.
- Create application team policies that inherit the base policy.
- Define application team-specific rules in the policy. You can also migrate rules from pre-existing firewalls.
- Create Microsoft Entra custom roles to provide fine grained access to rule collection group and add roles at a Firewall Policy scope. In the following example, Sales team members can edit rule collection groups for the Sales teams Firewall Policy. The same applies to the Database and Engineering teams.
- Associate the policy to the corresponding firewall. An Azure firewall can have only one assigned policy. This requires each application team to have their own firewall.
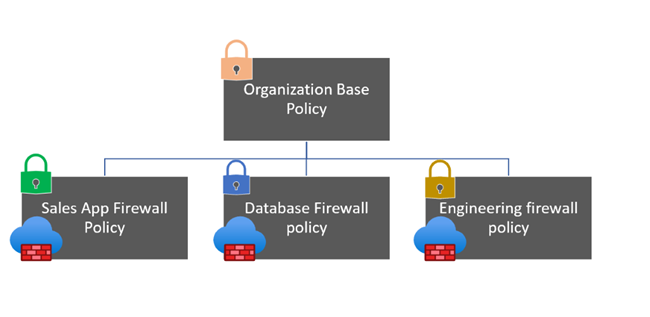
Create the firewall policies
- A base firewall policy.
Create policies for each of the application teams:
- A Sales firewall policy. The Sales firewall policy inherits the base firewall policy.
- A Database firewall policy. The Database firewall policy inherits base firewall policy.
- An Engineering firewall policy. The Engineering firewall policy also inherits the base firewall policy.
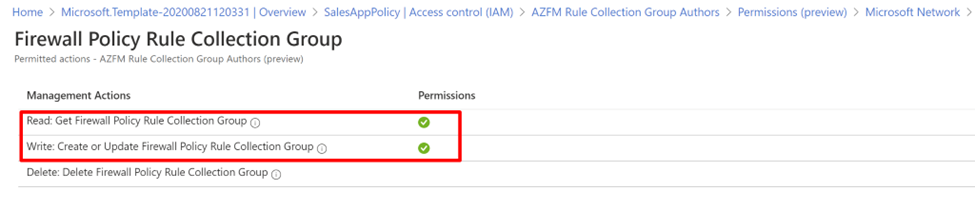
Create custom roles to access the rule collection groups
Custom roles are defined for each application team. The role defines operations and scope. The application teams are allowed to edit rule collection groups for their respective applications.
Use the following high-level procedure to define custom roles:
Get the subscription.
Select-AzSubscription -SubscriptionId xxxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxxxxRun the following command.
Get-AzProviderOperation "Microsoft.Support/*" | FT Operation, Description -AutoSizeUse the Get-AzRoleDefinition command to output the Reader role in JSON format.
Get-AzRoleDefinition -Name "Reader" | ConvertTo-Json | Out-File C:\CustomRoles\ReaderSupportRole.jsonOpen the ReaderSupportRole.json file in an editor.
Here's the JSON output. For information about the different properties, see Azure custom roles.
{
"Name": "Reader",
"Id": "acdd72a7-3385-48ef-bd42-f606fba81ae7",
"IsCustom": false,
"Description": "Lets you view everything, but not make any changes.",
"Actions": [
"*/read"
],
"NotActions": [],
"DataActions": [],
"NotDataActions": [],
"AssignableScopes": [
"/"
]
}
Edit the JSON file to add the
*/read", "Microsoft.Network/*/read", "Microsoft.Network/firewallPolicies/ruleCollectionGroups/writeoperation to the Actions property. Be sure to include a comma after the read operation. This action allows the user to create and update rule collection groups.
In AssignableScopes, add your subscription ID with the following format.
/subscriptions/xxxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxxxxYou must add explicit subscription IDs. Otherwise, you aren't allowed to import the role into your subscription.
Delete the Id property line and change the IsCustom property to true.
Change the Name and Description properties to AZFM Rule Collection Group Author and Users in this role can edit Firewall Policy rule collection groups
Your JSON file should look similar to the following example:
{
"Name": "AZFM Rule Collection Group Author",
"IsCustom": true,
"Description": "Users in this role can edit Firewall Policy rule collection groups",
"Actions": [
"*/read",
"Microsoft.Network/*/read",
"Microsoft.Network/firewallPolicies/ruleCollectionGroups/write"
],
"NotActions": [
],
"DataActions": [
],
"NotDataActions": [
],
"AssignableScopes": [
"/subscriptions/xxxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxxxx"]
}
To create the new custom role, use the New-AzRoleDefinition command and specify the JSON role definition file.
New-AzRoleDefinition -InputFile "C:\CustomRoles\RuleCollectionGroupRole.json
List custom roles
To list all the custom roles, you can use the Get-AzRoleDefinition command:
Get-AzRoleDefinition | ? {$_.IsCustom -eq $true} | FT Name, IsCustom
You can also see the custom roles in the Azure portal. Go to your subscription, select Access control (IAM), Roles.
For more information, see Tutorial: Create an Azure custom role using Azure PowerShell.
Add users to the custom role
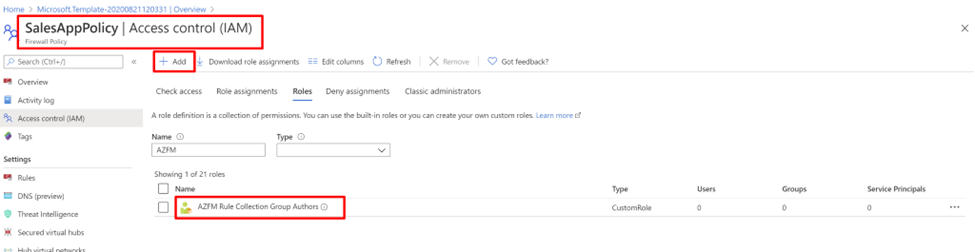
On the portal, you can add users to the AZFM Rule Collection Group Authors role and provide access to the firewall policies.
- From the portal, select the Application team firewall policy (for example, SalesAppPolicy).
- Select Access Control.
- Select Add role assignment.
- Add users/user groups (for example, the Sales team) to the role.
Repeat this procedure for the other firewall policies.
Summary
Firewall Policy with custom roles now provides selective access to firewall policy rule collection groups.
Users don’t have permissions to:
- Delete the Azure Firewall or firewall policy.
- Update firewall policy hierarchy or DNS settings or threat intelligence.
- Update firewall policy where they aren't members of AZFM Rule Collection Group Author group.
Security administrators can use base policy to enforce guardrails and block certain types of traffic (for example ICMP) as required by their enterprise.
Next steps
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for