Limit the port range when using RDP Shortpath for public networks
By default, RDP Shortpath for public networks uses an ephemeral port range of 49152 to 65535 to establish a direct path between server and client. However, you may want to configure your session hosts to use a smaller, predictable port range.
You can set a smaller default range of ports 38300 to 39299, or you can specify your own port range to use. When enabled on your session hosts, the Remote Desktop client will randomly select the port from the range you specify for every connection. If this range is exhausted, clients will fall back to using the default port range (49152-65535).
When choosing the base and pool size, consider the number of ports you choose. The range must be between 1024 and 49151, after which the ephemeral port range begins.
Prerequisites
A client device running the Remote Desktop client for Windows, version 1.2.3488 or later. Currently, non-Windows clients aren't supported.
Internet access for both clients and session hosts. Session hosts require outbound UDP connectivity from your session hosts to the internet. For more information you can use to configure firewalls and Network Security Group, see Network configurations for RDP Shortpath.
Enable a limited port range
To enable a limited port range when using RDP Shortpath for public networks, you can use Group Policy, either centrally from your domain for session hosts that are joined to an Active Directory (AD) domain, or locally for session hosts that are joined to Microsoft Entra ID.
Download the Azure Virtual Desktop administrative template and extract the contents of the .cab file and .zip archive.
Depending on whether you want to configure Group Policy centrally from your domain, or locally for each session host:
AD Domain:
Copy and paste the terminalserver-avd.admx file to the Central Store for your domain, for example
\\contoso.com\SYSVOL\contoso.com\policies\PolicyDefinitions, where contoso.com is your domain name. Then copy the en-us\terminalserver-avd.adml file to theen-ussubfolder.Open the Group Policy Management Console (GPMC) and create or edit a policy that targets your session hosts.
Locally:
Copy and paste the terminalserver-avd.admx file to
%windir%\PolicyDefinitions. Then copy the en-us\terminalserver-avd.adml file to theen-ussubfolder.Open the Local Group Policy Editor on the session host.
Browse to Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Azure Virtual Desktop. You should see policy settings for Azure Virtual Desktop, as shown in the following screenshot:
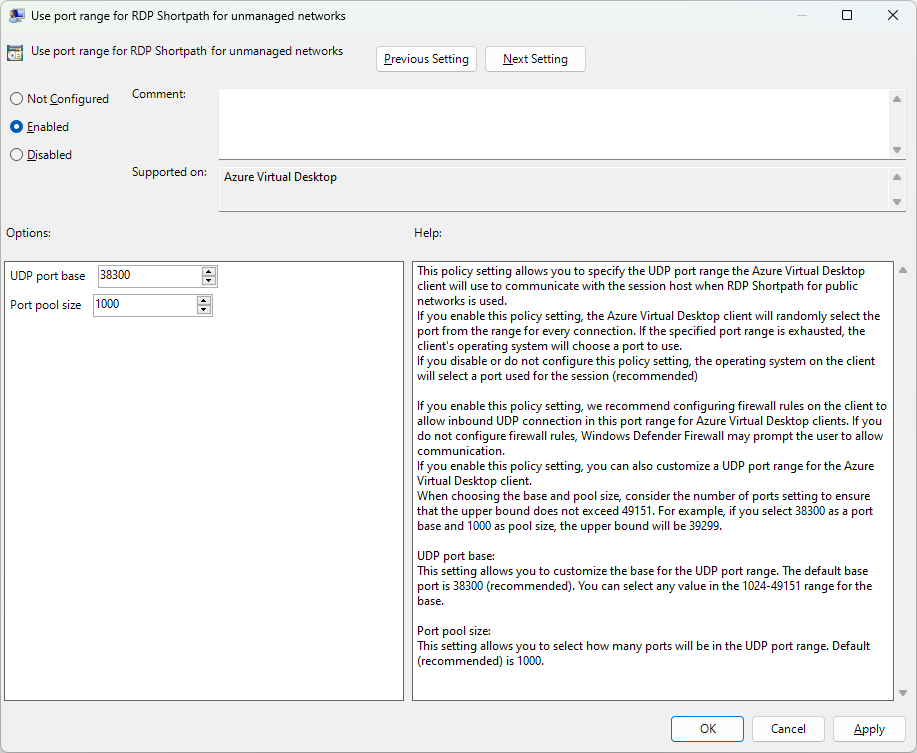
Open the policy setting Use port range for RDP Shortpath for unmanaged networks and set it to Enabled. For UDP base port, specify the port number to begin the range. For Port pool size, specify the number of sequential ports that will be in the range. For example, if you specify 38300 as the UDP base port and 1000 as the Port pool size, the upper port number will be 39299.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for