Microsoft Flow supports Intune
Important
This content is archived and is not being updated. For the latest documentation, see Microsoft Dynamics 365 product documentation. For the latest release plans, see Dynamics 365 and Microsoft Power Platform release plans.
We have now shipped a new version of the Microsoft Flow mobile application for Apple iOS and Android that supports Microsoft Application Management (MAM) without device enrollment. Using MAM allows IT administrators to create and enforce mobile data policies to safeguard company data.
Support for Intune is important
Whether a customer has adopted a Bring Your Own Device (BYOD) strategy or is providing employees with a corporate phone, they are looking for more control over the data that resides on a mobile device. Organizations may want to restrict how data moves on the device and ensure the data is removed, should the employee leave the organization.
MAM definition
MAM allows organizations to create policies that govern how an application is used within a tenant. This can include enforcing app data encryption, limiting the ability to copy/extract data to only approved applications or enforcing a PIN on a device.
Your device doesn't need to be enrolled
Intune MAM without enrollment does not require a user to enroll their device in Intune MAM. However, the Company Portal application needs to be installed on the device to enforce policies. A user does not need to sign in to the Company Portal application for MAM to function. The Company Portal application can be downloaded from the Apple and Android app stores.

Required version of the Microsoft Flow mobile app
Version 2.31.0 of the app is required. Our deployments for iOS have reached 100% coverage to all regions. For Android, we are staging our rollout so there may be a delay in this version of the app being available.
Set up a MAM policy
An administrator can create policies from the Azure portal. For this example, we will create an App protection policy that enforces a flow user to require a PIN when using the Microsoft Flow mobile application.
From the Azure portal, navigate to Intune App Protection.
Select App protection policies – Create Policy.
An Add a policy form will appear that requires a Name, Description, and Platform.
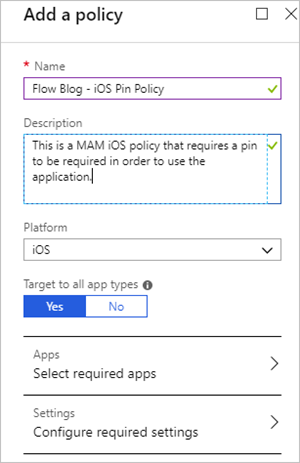
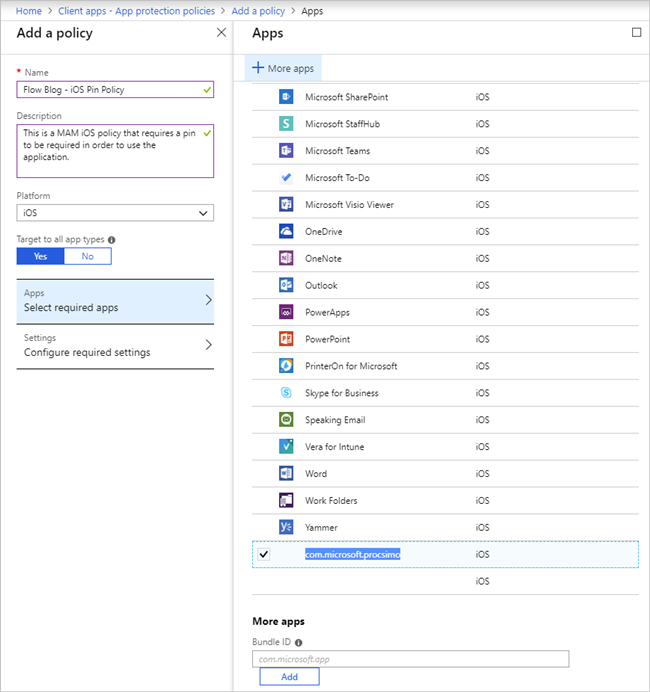
We now need to select an application that we want to manage. Currently, the Microsoft Flow application can be identified as one of the following:
- com.microsoft.procsimo (iOS)
- com.microsoft.flow (Android)
Note
A more friendly “Microsoft Flow” display name will appear in this experience later this month.
Ensure the appropriate application is selected based upon the platform that you are targeting. If you do not find it in the list of apps, search for it by typing the appropriate value into the Bundle ID field. Select the Add button to add this application as a required app, and then select Select to complete this configuration.
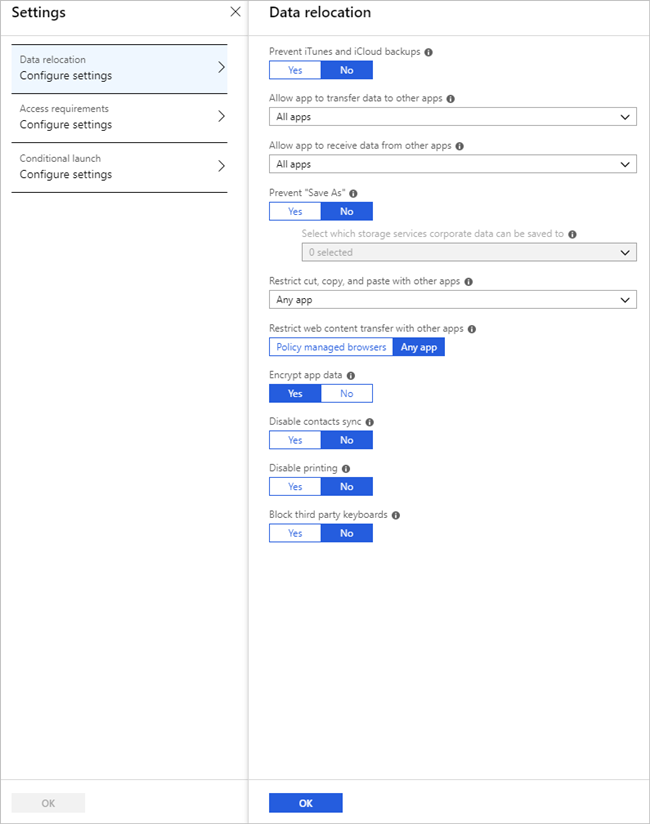
We now need to define our policy that will impose specific application behaviors by selecting Configure required settings.
Within the Configure required settings experience, there are three areas that we need to configure: Data relocation, Access requirements, and Conditional launch. Let’s start with the Data relocation settings. Since the Microsoft Flow app is not used to generate local data, we can use the default policy.
Note
This policy has been used as an example. Please modify it to meet your organization’s needs.
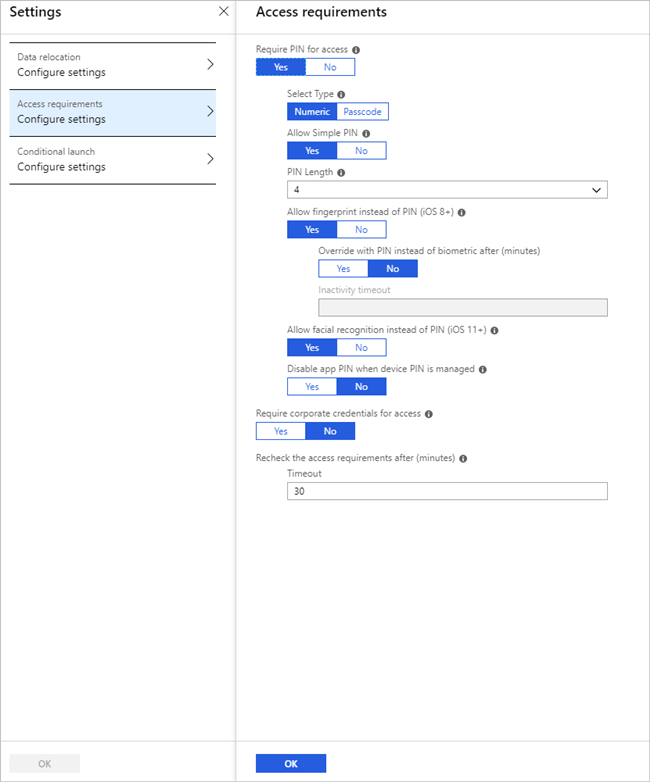
Next, we are going to focus on Access requirements and can establish a policy like the one below. Once we are done configuring our Access requirements, we can select the OK button.
Note
When testing, you can lower the Recheck the access requirements after (minutes) setting to reduce the amount of time you need to wait for a prompt.
In addition, we can also provide a Conditional launch configuration. For the purposes of this example, we will keep the default policy and you can select OK to complete this interaction.
Select OK to close the Settings panel.
Select Create to finalize the policy.
Within our policy list, we should now see the policy that we just created.
We now need to assign the Azure AD groups for which this policy should apply. We can assign access by selecting our policy and then by selecting Assignments.
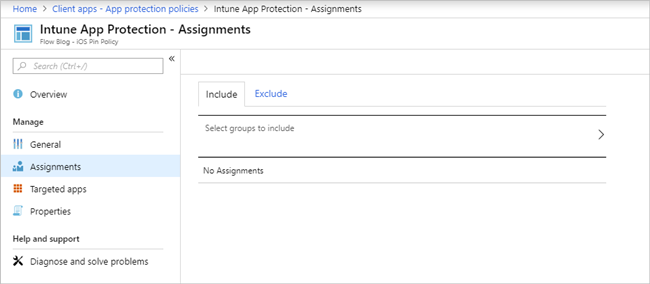
To select an Azure AD group, select Select groups to include, and then select the appropriate group. For this example, we have created an Azure AD group and included members for whom we want these policies applied.
Testing
We can now go ahead and test our MAM policy by signing in to the Microsoft Flow mobile app and following these instructions:
Ensure you have the latest version of the iOS or Android app (version 2.31.0 or later).
Close the Microsoft Flow mobile app.
Launch Microsoft Flow mobile app.
You should be prompted with the following message:
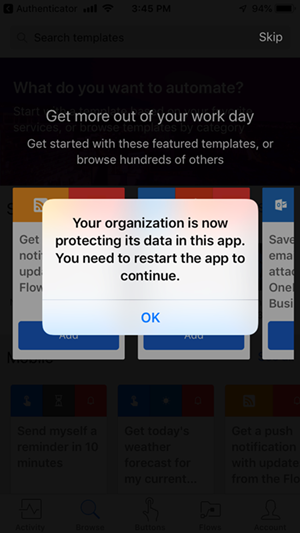
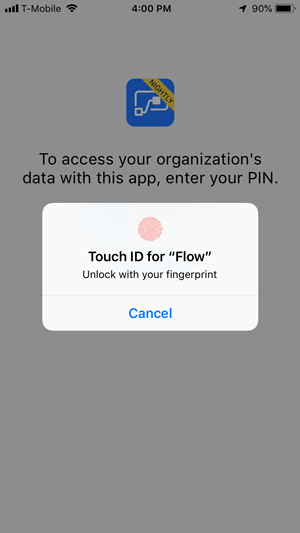
Since we opted to allow fingerprints when we created our policy, we can provide our fingerprint.
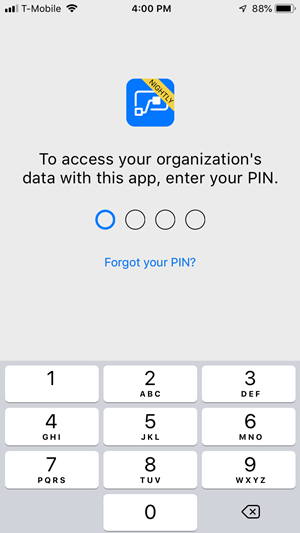
Otherwise, a user will be required to set up and provide a PIN number.
Conclusion
MAM support has been a key ask by our customers who are using Intune App Protection to manage company data on mobile devices. By providing this support, we are aligning with Microsoft customer promises to ensure that organizations have a consistent way to manage their mobile data.