Events
Mar 17, 9 PM - Mar 21, 10 AM
Join the meetup series to build scalable AI solutions based on real-world use cases with fellow developers and experts.
Register nowThis browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Developers need to debug and test cloud apps on their local workstation. When an app runs on a developer's workstation during local development, it must still authenticate to any Azure services used by the app. This article covers how to set up dedicated application service principal objects to be used during local development.
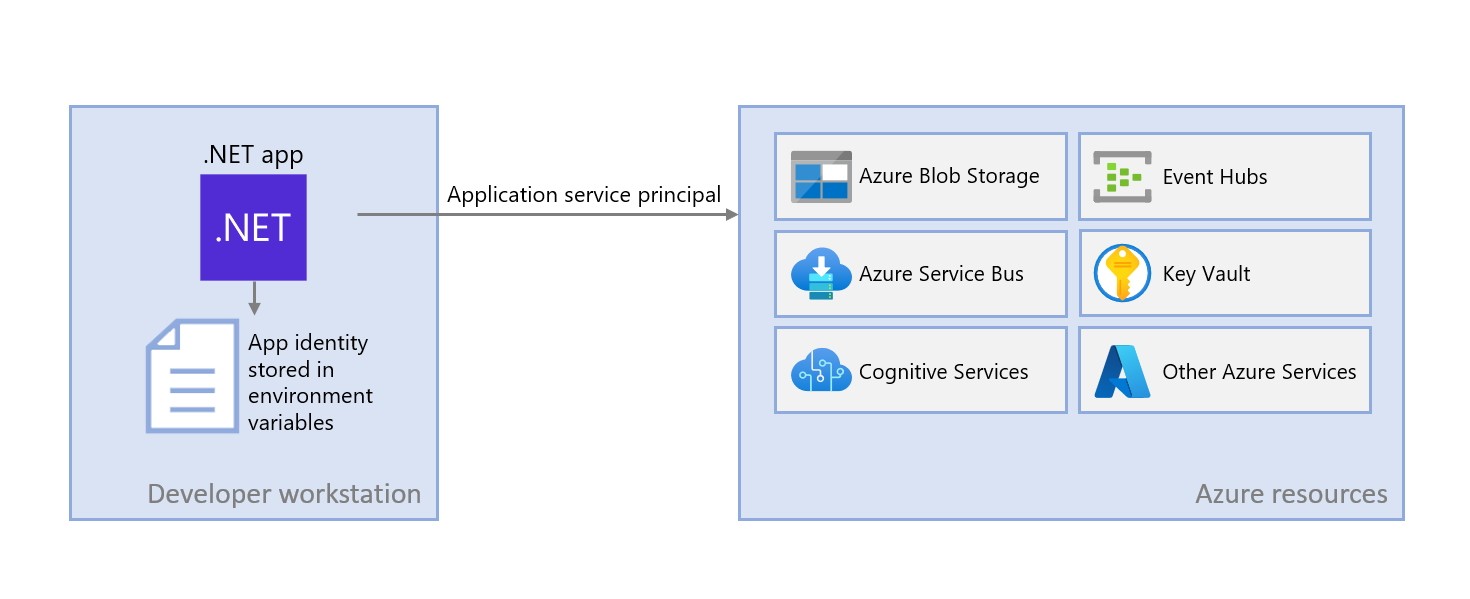
Dedicated application service principals for local development allow you to follow the principle of least privilege during app development. Since permissions are scoped to exactly what's needed for the app during development, app code is prevented from accidentally accessing an Azure resource intended for use by a different app. This also prevents bugs from occurring when the app is moved to production because the app was over-privileged in the dev environment.
An application service principal is set up for the app when the app is registered in Azure. When registering an app for local development, it's recommended to:
During local development, environment variables are set with the application service principal's identity. The Azure Identity library reads these environment variables and uses this information to authenticate the app to the Azure resources it needs.
Application service principal objects are created with an app registration in Azure. This can be done using either the Azure portal or Azure CLI.
Sign in to the Azure portal and follow these steps.
Since there are typically multiple developers who work on an app, it's recommended to create a Microsoft Entra group to encapsulate the roles (permissions) the app needs in local development rather than assigning the roles to individual service principal objects. This approach offers the following advantages:
Next, determine what roles (permissions) your app needs on what resources and assign those roles to your app. In this example, the roles will be assigned to the Microsoft Entra group created in step 2. Groups can be assigned a role at a resource, resource group, or subscription scope. This example shows how to assign roles at the resource group scope, since most apps group all their Azure resources into a single resource group.
At runtime, DefaultAzureCredential looks for the service principal information in a collection of environment variables. There are multiple ways to configure environment variables when working with .NET, depending on your tooling and environment.
Regardless of the approach you choose, configure the following environment variables when working with a service principal:
AZURE_CLIENT_ID → The app ID value.AZURE_TENANT_ID → The tenant ID value.AZURE_CLIENT_SECRET → The password/credential generated for the app.When working locally with Visual Studio, environment variables can be set in the launchsettings.json file in the Properties folder of your project. When the app starts up, these values are pulled in automatically. Keep in mind, these configurations don't travel with your app when it's deployed, so you need to set up environment variables on your target hosting environment.
"profiles": {
"SampleProject": {
"commandName": "Project",
"dotnetRunMessages": true,
"launchBrowser": true,
"applicationUrl": "https://localhost:7177;http://localhost:5177",
"environmentVariables": {
"ASPNETCORE_ENVIRONMENT": "Development",
"AZURE_CLIENT_ID": "00000000-0000-0000-0000-000000000000",
"AZURE_TENANT_ID":"11111111-1111-1111-1111-111111111111",
"AZURE_CLIENT_SECRET": "=abcdefghijklmnopqrstuvwxyz"
}
},
"IIS Express": {
"commandName": "IISExpress",
"launchBrowser": true,
"environmentVariables": {
"ASPNETCORE_ENVIRONMENT": "Development",
"AZURE_CLIENT_ID": "00000000-0000-0000-0000-000000000000",
"AZURE_TENANT_ID": "11111111-1111-1111-1111-111111111111",
"AZURE_CLIENT_SECRET": "=abcdefghijklmnopqrstuvwxyz"
}
}
}
DefaultAzureCredential is an opinionated, ordered sequence of mechanisms for authenticating to Microsoft Entra ID. Each authentication mechanism is a class derived from the TokenCredential class and is known as a credential. At runtime, DefaultAzureCredential attempts to authenticate using the first credential. If that credential fails to acquire an access token, the next credential in the sequence is attempted, and so on, until an access token is successfully obtained. In this way, your app can use different credentials in different environments without writing environment-specific code.
To use DefaultAzureCredential, add the Azure.Identity and optionally the Microsoft.Extensions.Azure packages to your application:
In a terminal of your choice, navigate to the application project directory and run the following commands:
dotnet add package Azure.Identity
dotnet add package Microsoft.Extensions.Azure
Azure services are accessed using specialized client classes from the various Azure SDK client libraries. These classes and your own custom services should be registered so they can be accessed via dependency injection throughout your app. In Program.cs, complete the following steps to register a client class and DefaultAzureCredential:
Azure.Identity and Microsoft.Extensions.Azure namespaces via using directives.Add-prefixed extension method.DefaultAzureCredential to the UseCredential method.For example:
using Microsoft.Extensions.Azure;
using Azure.Identity;
builder.Services.AddAzureClients(clientBuilder =>
{
clientBuilder.AddBlobServiceClient(
new Uri("https://<account-name>.blob.core.windows.net"));
clientBuilder.UseCredential(new DefaultAzureCredential());
});
An alternative to UseCredential is to instantiate DefaultAzureCredential directly:
using Azure.Identity;
builder.Services.AddSingleton<BlobServiceClient>(_ =>
new BlobServiceClient(
new Uri("https://<account-name>.blob.core.windows.net"),
new DefaultAzureCredential()));
When the preceding code runs on your local development workstation, it looks in the environment variables for an application service principal or at locally installed developer tools, such as Visual Studio, for a set of developer credentials. Either approach can be used to authenticate the app to Azure resources during local development.
When deployed to Azure, this same code can also authenticate your app to other Azure resources. DefaultAzureCredential can retrieve environment settings and managed identity configurations to authenticate to other services automatically.
.NET feedback
.NET is an open source project. Select a link to provide feedback:
Events
Mar 17, 9 PM - Mar 21, 10 AM
Join the meetup series to build scalable AI solutions based on real-world use cases with fellow developers and experts.
Register nowTraining
Module
Introduction to using Managed Identity to authenticate to Azure OpenAI with .NET - Training
How to implement role based access control and managed identity authentication to Azure OpenAI with .NET.
Certification
Microsoft Certified: Azure Developer Associate - Certifications
Build end-to-end solutions in Microsoft Azure to create Azure Functions, implement and manage web apps, develop solutions utilizing Azure storage, and more.
Documentation
Authenticate .NET apps to Azure using developer accounts - .NET
Learn how to authenticate your application to Azure services when using the Azure SDK for .NET during local development using developer accounts.
How to authenticate .NET applications with Azure services - .NET
Learn how to authenticate a .NET app with Azure services by using classes in the Azure Identity library.
Authenticate to Azure resources from .NET apps hosted on-premises - .NET
This article describes how to authenticate your application to Azure services when using the Azure SDK for .NET in on-premises hosted apps.