Events
Apr 9, 3 PM - Apr 10, 12 PM
Code the Future with AI and connect with Java peers and experts at JDConf 2025.
Register NowThis browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Claims-aware apps perform a redirection to the Security Token Service (STS). The STS requests credentials from the user in exchange for a token and then redirects the user to the application. There are a few ways to enable application proxy to work with these redirects. Use this article to configure your deployment for claims-aware apps.
The STS that the claims-aware app redirects to must be available outside of your on-premises network. Expose it through a proxy or by allowing outside connections.
You can configure Active Directory Federation Services for claims-aware apps in one of two ways. The first is by using custom domains. The second is with WS-Federation.
If all the internal URLs for your applications are fully qualified domain names (FQDNs), then you can configure custom domains for your applications. Use the custom domains to create external URLs that are the same as the internal URLs. When your external URLs match your internal URLs, then the STS redirections work whether your users are on-premises or remote.
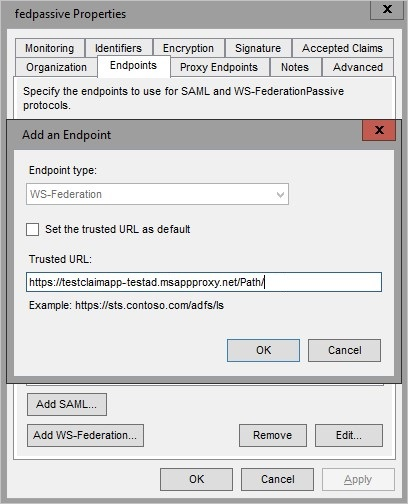
Open Active Directory Federation Services management.
Go to Relying Party Trusts, right-click on the app you're publishing with application proxy, and choose Properties.

On the Endpoints tab, under Endpoint type, select WS-Federation.
Under Trusted URL, enter the URL you entered in the application proxy under External URL and select OK.
Events
Apr 9, 3 PM - Apr 10, 12 PM
Code the Future with AI and connect with Java peers and experts at JDConf 2025.
Register NowTraining
Module
Implement and monitor the integration of enterprise apps for SSO - Training
Deploying and monitoring enterprise applications to Azure solutions can ensure security. Explore how to deploy on-premises and cloud based apps to users.
Certification
Microsoft Certified: Identity and Access Administrator Associate - Certifications
Demonstrate the features of Microsoft Entra ID to modernize identity solutions, implement hybrid solutions, and implement identity governance.
Documentation
Custom domains in Microsoft Entra application proxy - Microsoft Entra ID
Configure and manage custom domains in Microsoft Entra application proxy.
Complex applications for Microsoft Entra application proxy - Microsoft Entra ID
Understand complex applications in Microsoft Entra application proxy.
Remove personal data - Microsoft Entra application proxy - Microsoft Entra ID
Remove personal data from connectors installed on devices for Microsoft Entra application proxy.