One-To-One Mappings <oneToOneMappings>
Overview
The <oneToOneMappings> element of the <iisClientCertificateMappingAuthentication> element maps individual client certificates to individual user accounts on a one-to-one basis. These one-to-one certificate mappings can be used in place of the more commonly used methods of authentication, such as Windows authentication or Basic authentication.
Note
One-to-one certificate mappings differ from many-to-one certificate mappings, which can map multiple certificates to a single user account.
Compatibility
| Version | Notes |
|---|---|
| IIS 10.0 | The <oneToOneMappings> element was not modified in IIS 10.0. |
| IIS 8.5 | The <oneToOneMappings> element was not modified in IIS 8.5. |
| IIS 8.0 | The <oneToOneMappings> element was not modified in IIS 8.0. |
| IIS 7.5 | The <oneToOneMappings> element was not modified in IIS 7.5. |
| IIS 7.0 | The <oneToOneMappings> element of the <iisClientCertificateMappingAuthentication> element was introduced in IIS 7.0. |
| IIS 6.0 | The <oneToOneMappings> element replaces the IIS 6.0 IIsCertMapper metabase object. |
Setup
The <iisClientCertificateMappingAuthentication> element is not available on the default installation of IIS 7 and later. To install it, use the following steps.
Windows Server 2012 or Windows Server 2012 R2
- On the taskbar, click Server Manager.
- In Server Manager, click the Manage menu, and then click Add Roles and Features.
- In the Add Roles and Features wizard, click Next. Select the installation type and click Next. Select the destination server and click Next.
- On the Server Roles page, expand Web Server (IIS), expand Web Server, expand Security, and then select IIS Client Certificate Mapping Authentication. Click Next.
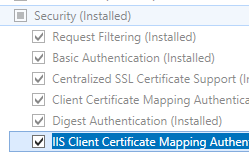 .
. - On the Select features page, click Next.
- On the Confirm installation selections page, click Install.
- On the Results page, click Close.
Windows 8 or Windows 8.1
- On the Start screen, move the pointer all the way to the lower left corner, right-click the Start button, and then click Control Panel.
- In Control Panel, click Programs and Features, and then click Turn Windows features on or off.
- Expand Internet Information Services, expand World Wide Web Services, expand Security, and then select IIS Client Certificate Mapping Authentication.
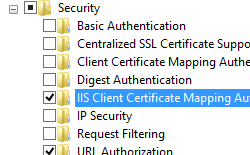
- Click OK.
- Click Close.
Windows Server 2008 or Windows Server 2008 R2
- On the taskbar, click Start, point to Administrative Tools, and then click Server Manager.
- In the Server Manager hierarchy pane, expand Roles, and then click Web Server (IIS).
- In the Web Server (IIS) pane, scroll to the Role Services section, and then click Add Role Services.
- On the Select Role Services page of the Add Role Services Wizard, select IIS Client Certificate Mapping Authentication, and then click Next.
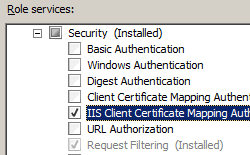
- On the Confirm Installation Selections page, click Install.
- On the Results page, click Close.
Windows Vista or Windows 7
- On the taskbar, click Start, and then click Control Panel.
- In Control Panel, click Programs and Features, and then click Turn Windows Features on or off.
- Expand Internet Information Services, then select IIS Client Certificate Mapping Authentication, and then click OK.
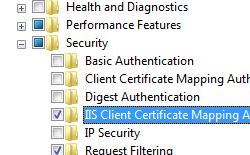
How To
There is no user interface for configuring IIS Client Certificate Mapping authentication for IIS 7. For examples of how to configure IIS Client Certificate Mapping authentication programmatically, see the Code Samples section of this document.
Configuration
Attributes
None.
Child Elements
| Element | Description |
|---|---|
add |
Optional element. Adds a one-to-one mapping to the collection of one-to-one mappings. |
clear |
Optional element. Removes all references to one-to-one mappings from the one-to-one mappings collection. |
Configuration Sample
The following configuration sample enables IIS Client Certificate Mapping authentication using one-to-one certificate mapping for the Default Web Site, creates a singe one-to-one certificate mapping for a user account, and configures the site to require SSL and to negotiate client certificates.
<location path="Default Web Site">
<system.webServer>
<security>
<access sslFlags="Ssl, SslNegotiateCert" />
<authentication>
<windowsAuthentication enabled="false" />
<anonymousAuthentication enabled="false" />
<digestAuthentication enabled="false" />
<basicAuthentication enabled="false" />
<iisClientCertificateMappingAuthentication enabled="true"
oneToOneCertificateMappingsEnabled="true">
<oneToOneMappings>
<add enabled="true"
userName="administrator"
password="[enc:57686f6120447564652c2049495320526f636b73:enc]"
certificate="Base64-Encoded-Certificate-Data" />
</oneToOneMappings>
</iisClientCertificateMappingAuthentication>
</authentication>
</security>
</system.webServer>
</location>
How to retrieve Base-64 encoded string from a client certificate
Note
To retrieve a Base-64 encoded certificate data for all of the samples in this topic, you can export a certificate using the following steps:
Click Start, then Run.
Enter MMC, and then click OK.
When the Microsoft Management Console opens, click File, then Add/Remove Snap-ins.
In the Add or Remove Snap-ins dialog box:
- Highlight Certificates in the list of available snap-ins, then click Add.
- Choose to manage certificates for My user account, then click Finish.
- Click OK to close the dialog box.
In the Microsoft Management Console:
- Expand Certificates - Current User, then Personal, then Certificates.
- In the list of certificates, right-click the certificate that you want to export, then click All Tasks, and then click Export.
When the Certificate Export Wizard opens:
- Click Next.
- Choose No, do not export the private key, then click Next.
- Choose Base-64 encoded X.509 9 (.CER) for the export format, then click Next.
- Choose to save the certificate to your desktop as MyCertificate.cer, then click Next.
- Click Finish; you should see a dialog box that says the export was successful.
Close the Microsoft Management Console.
Open the MyCertificate.cer file that you exported using Windows Notepad:
- Remove "-----BEGIN CERTIFICATE-----" from the start of the text.
- Remove "-----END CERTIFICATE-----" from the end of the text.
- Concatenate all the lines into a single line of text - this is the Base-64 encoded certificate data that you will use for all of the samples in this topic.
Sample Code
The following code samples enable IIS Client Certificate Mapping authentication using one-to-one certificate mapping for the Default Web Site, create a single one-to-one certificate mapping for a user account, and configure the site to require SSL and to negotiate client certificates.
Note
To retrieve the Base-64 encoded certificate data for the code samples listed below, you can export a certificate using the steps listed in the Configuration Details section of this document.
AppCmd.exe
Note
Because of characters in certificate strings that cannot be parsed by AppCmd.exe, you should not use AppCmd.exe to configure IIS one-to-one certificate mappings.
C#
using System;
using System.Text;
using Microsoft.Web.Administration;
internal static class Sample
{
private static void Main()
{
using (ServerManager serverManager = new ServerManager())
{
Configuration config = serverManager.GetApplicationHostConfiguration();
ConfigurationSection iisClientCertificateMappingAuthenticationSection = config.GetSection("system.webServer/security/authentication/iisClientCertificateMappingAuthentication", "Default Web Site");
iisClientCertificateMappingAuthenticationSection["enabled"] = true;
iisClientCertificateMappingAuthenticationSection["oneToOneCertificateMappingsEnabled"] = true;
ConfigurationElementCollection oneToOneMappingsCollection = iisClientCertificateMappingAuthenticationSection.GetCollection("oneToOneMappings");
ConfigurationElement addElement = oneToOneMappingsCollection.CreateElement("add");
addElement["enabled"] = true;
addElement["userName"] = @"Username";
addElement["password"] = @"Password";
addElement["certificate"] = @"Base-64-Encoded-Certificate-Data";
oneToOneMappingsCollection.Add(addElement);
ConfigurationSection accessSection = config.GetSection("system.webServer/security/access", "Default Web Site");
accessSection["sslFlags"] = @"Ssl, SslNegotiateCert";
serverManager.CommitChanges();
}
}
}
VB.NET
Imports System
Imports System.Text
Imports Microsoft.Web.Administration
Module Sample
Sub Main()
Dim serverManager As ServerManager = New ServerManager
Dim config As Configuration = serverManager.GetApplicationHostConfiguration
Dim iisClientCertificateMappingAuthenticationSection As ConfigurationSection = config.GetSection("system.webServer/security/authentication/iisClientCertificateMappingAuthentication", "Default Web Site")
iisClientCertificateMappingAuthenticationSection("enabled") = True
iisClientCertificateMappingAuthenticationSection("oneToOneCertificateMappingsEnabled") = True
Dim oneToOneMappingsCollection As ConfigurationElementCollection = iisClientCertificateMappingAuthenticationSection.GetCollection("oneToOneMappings")
Dim addElement As ConfigurationElement = oneToOneMappingsCollection.CreateElement("add")
addElement("enabled") = True
addElement("userName") = "Username"
addElement("password") = "Password"
addElement("certificate") = "Base-64-Encoded-Certificate-Data"
oneToOneMappingsCollection.Add(addElement)
Dim accessSection As ConfigurationSection = config.GetSection("system.webServer/security/access", "Default Web Site")
accessSection("sslFlags") = "Ssl, SslNegotiateCert"
serverManager.CommitChanges()
End Sub
End Module
JavaScript
var adminManager = new ActiveXObject('Microsoft.ApplicationHost.WritableAdminManager');
adminManager.CommitPath = "MACHINE/WEBROOT/APPHOST";
var iisClientCertificateMappingAuthenticationSection = adminManager.GetAdminSection("system.webServer/security/authentication/iisClientCertificateMappingAuthentication", "MACHINE/WEBROOT/APPHOST/Default Web Site");
iisClientCertificateMappingAuthenticationSection.Properties.Item("enabled").Value = true;
iisClientCertificateMappingAuthenticationSection.Properties.Item("oneToOneCertificateMappingsEnabled").Value = true;
var oneToOneMappingsCollection = iisClientCertificateMappingAuthenticationSection.ChildElements.Item("oneToOneMappings").Collection;
var addElement = oneToOneMappingsCollection.CreateNewElement("add");
addElement.Properties.Item("enabled").Value = true;
addElement.Properties.Item("userName").Value = "Username";
addElement.Properties.Item("password").Value = "Password";
addElement.Properties.Item("certificate").Value = "Base-64-Encoded-Certificate-Data";
oneToOneMappingsCollection.AddElement(addElement);
var accessSection = adminManager.GetAdminSection("system.webServer/security/access", "MACHINE/WEBROOT/APPHOST/Default Web Site");
accessSection.Properties.Item("sslFlags").Value = "Ssl, SslNegotiateCert";
adminManager.CommitChanges();
VBScript
Set adminManager = WScript.CreateObject("Microsoft.ApplicationHost.WritableAdminManager")
adminManager.CommitPath = "MACHINE/WEBROOT/APPHOST"
Set iisClientCertificateMappingAuthenticationSection = adminManager.GetAdminSection("system.webServer/security/authentication/iisClientCertificateMappingAuthentication", "MACHINE/WEBROOT/APPHOST/Default Web Site")
iisClientCertificateMappingAuthenticationSection.Properties.Item("enabled").Value = True
iisClientCertificateMappingAuthenticationSection.Properties.Item("oneToOneCertificateMappingsEnabled").Value = True
Set oneToOneMappingsCollection = iisClientCertificateMappingAuthenticationSection.ChildElements.Item("oneToOneMappings").Collection
Set addElement = oneToOneMappingsCollection.CreateNewElement("add")
addElement.Properties.Item("enabled").Value = True
addElement.Properties.Item("userName").Value = "Username"
addElement.Properties.Item("password").Value = "Password"
addElement.Properties.Item("certificate").Value = "Base-64-Encoded-Certificate-Data"
oneToOneMappingsCollection.AddElement(addElement)
Set accessSection = adminManager.GetAdminSection("system.webServer/security/access", "MACHINE/WEBROOT/APPHOST/Default Web Site")
accessSection.Properties.Item("sslFlags").Value = "Ssl, SslNegotiateCert"
adminManager.CommitChanges()
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for