Use Trend Micro Mobile Security as a Service with Microsoft Intune
Control mobile device access to corporate resources using Conditional Access based on risk assessment conducted by Trend Micro Mobile Security as a Service, a mobile threat defense (MTD) solution that integrates with Microsoft Intune. Risk is assessed based on telemetry collected from devices protected by the Trend Micro Mobile Security as a Service, including:
- Malicious apps installed
- Malicious network behavior and profiles
- Operating system vulnerabilities
- Device misconfiguration
You can configure Conditional Access policies based on Trend Micro Mobile Security as a Service’s risk assessment, enabled through Intune device compliance policies for enrolled devices. You can set up your policies to allow or block noncompliant devices from accessing corporate resources based on detected threats.
Note
This Mobile Threat Defense vendor is not supported for unenrolled devices.
Supported platforms
- Android 7.0 and later
- iOS 11.0 and later
Prerequisites
- Microsoft Entra ID P1
- Microsoft Intune Plan 1 subscription
- Trend Micro account with administrative access to the Trend Micro Vision One console
How do Intune and the Trend Micro MTD connector help protect your company resources?
The Trend Micro Mobile Security as a Service mobile agent app for Android and iOS/iPadOS captures file system, network stack, device, and application telemetry where available, then sends the telemetry data to Trend Micro Mobile Security as a Service to assess the device's risk for mobile threats.
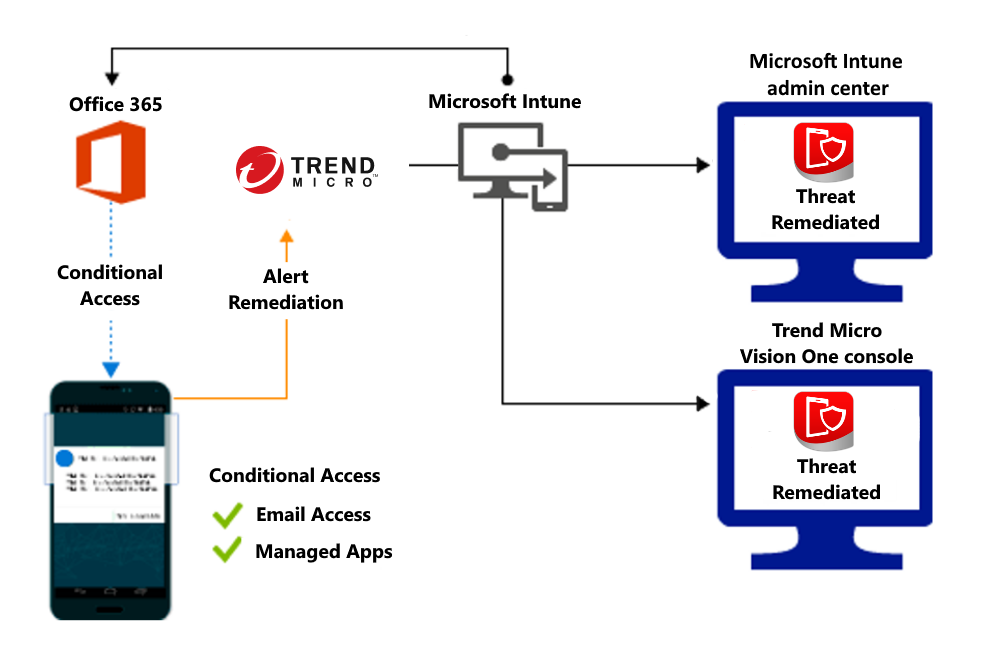
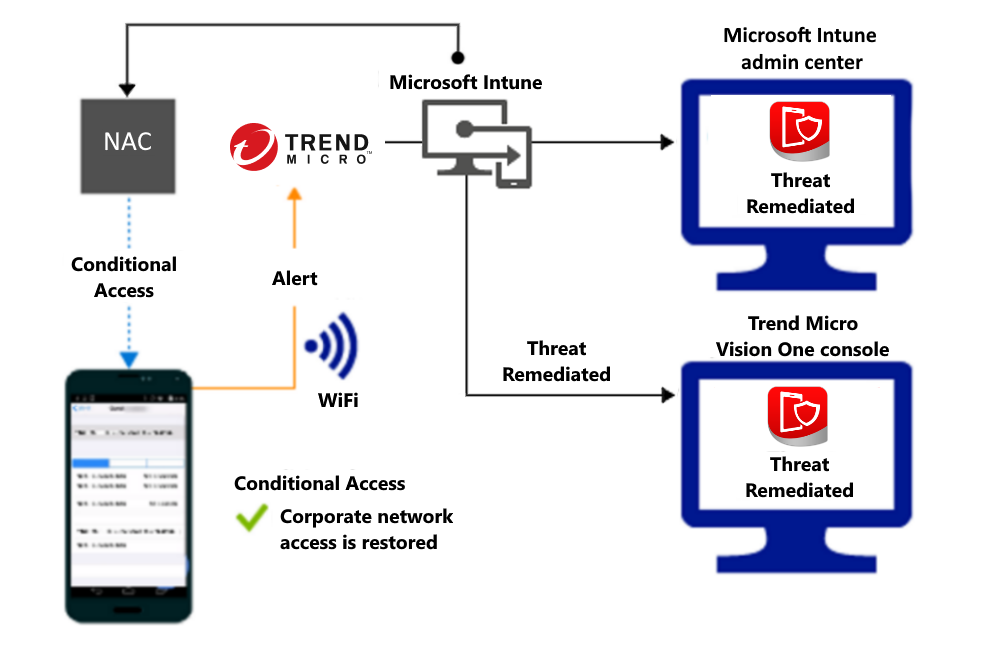
Support for enrolled devices - Intune device compliance policy includes a rule for MTD, which can use risk assessment information from Trend Micro. When the MTD rule is enabled, Intune evaluates device compliance with the policy that you enabled. If the device is found noncompliant, users are blocked access to corporate resources, such as Exchange Online and SharePoint Online. Users also receive guidance from the Trend Micro Mobile Security as a Service mobile agent app installed on their devices to resolve the issue and regain access to corporate resources. To support using Trend Micro with enrolled devices:
- Add MTD apps to devices (This is done automatically when setting up Trend Micro Mobile Security as a Service integration)
- Create a device compliance policy that supports MTD
- Enable the MTD connector in Intune
Sample scenarios
The following scenarios demonstrate the use of Trend Micro MTD when integrated with Intune:
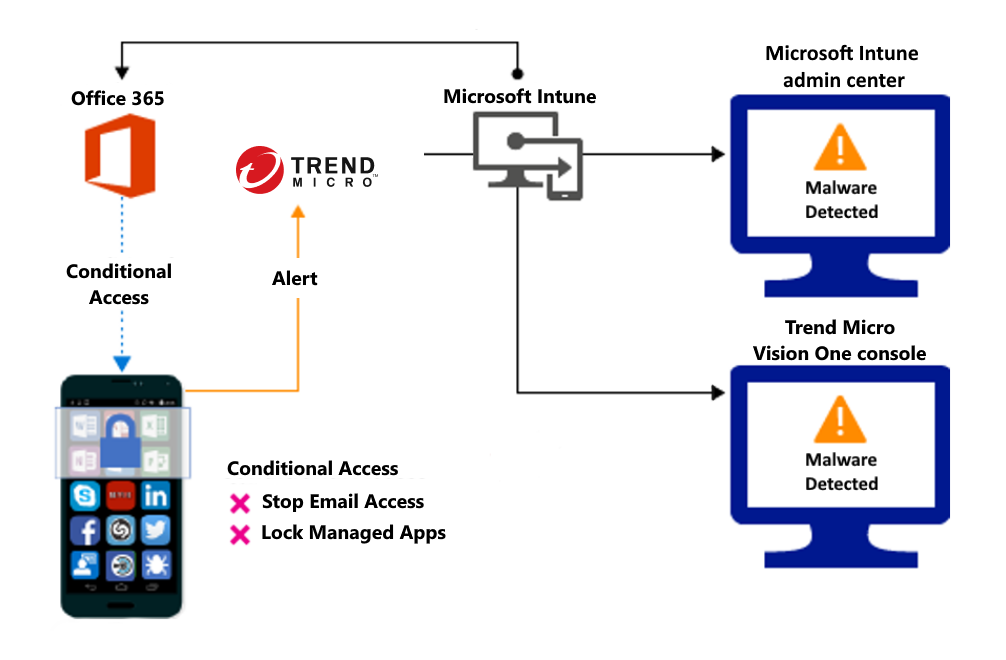
Control access based on threats from malicious apps
When malicious apps such as malware are detected on devices, you can block devices until the threat is resolved:
- Connecting to corporate e-mail
- Syncing corporate files with the OneDrive for Work app
- Accessing company apps
Block when malicious apps are detected:
Access granted on remediation:
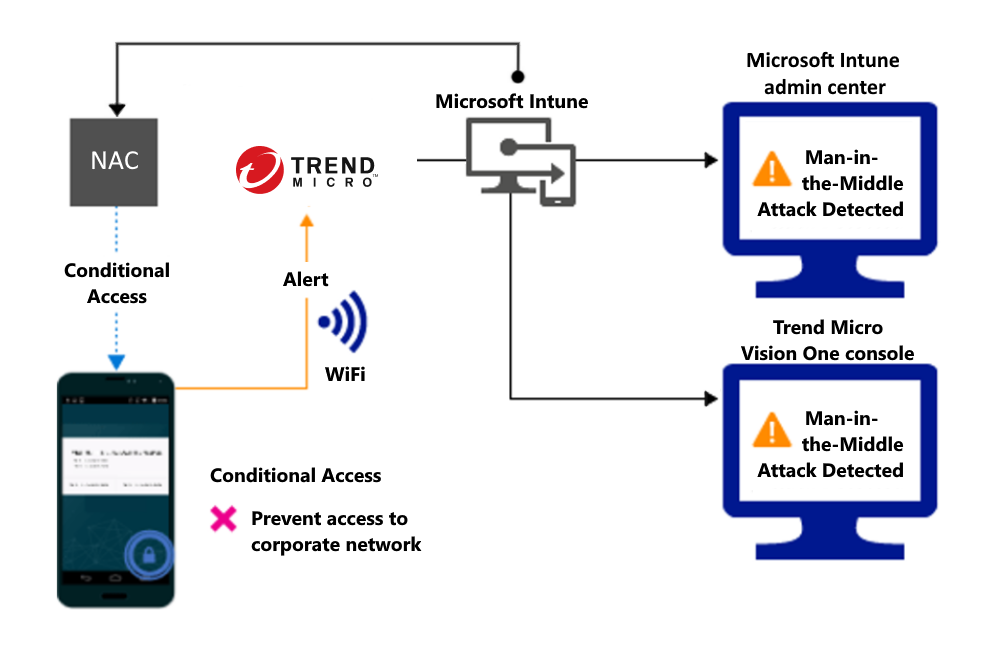
Control access based on threat to network
Detect threats like Man-in-the-middle in network, and protect access to Wi-Fi networks based on the device risk.
Block network access through Wi-Fi:
Access granted on remediation:
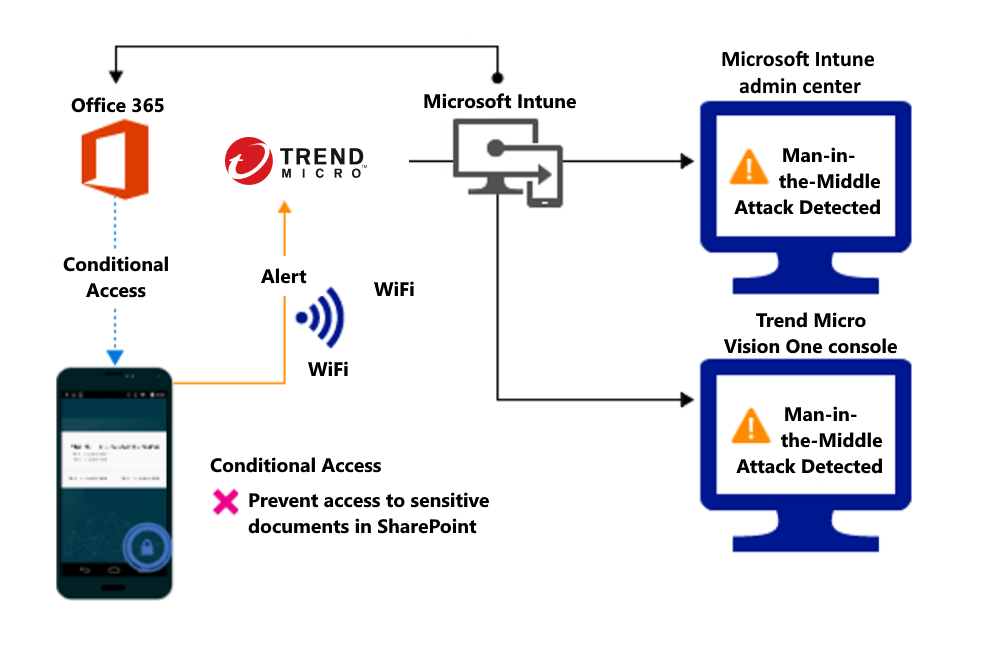
Control access to SharePoint Online based on threat to network
Detect threats like Man-in-the-middle in network and prevent synchronization of corporate files based on the device risk.
Block SharePoint Online when network threats are detected:
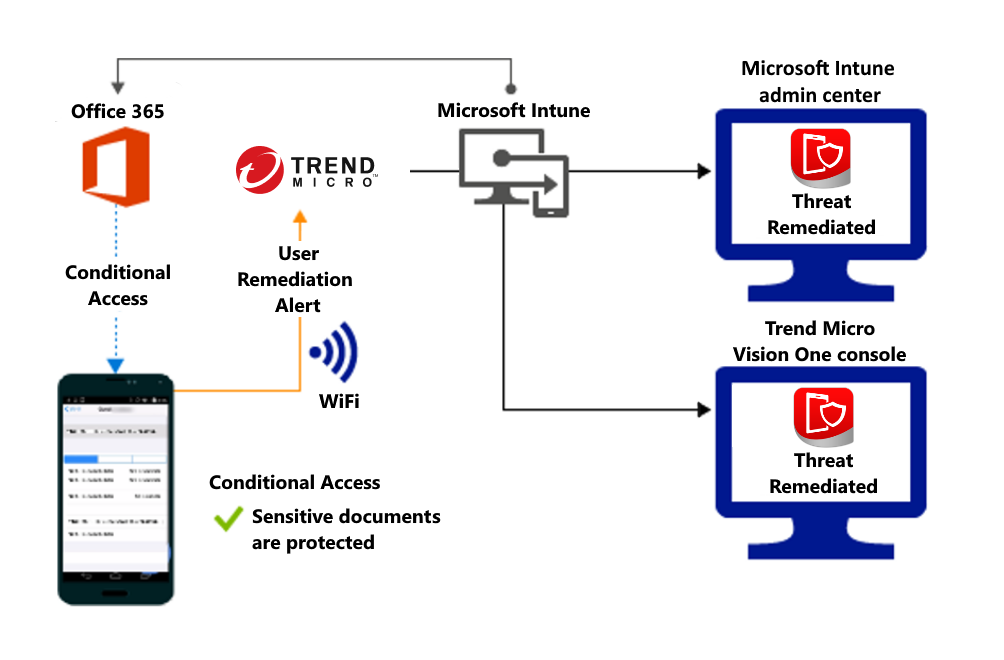
Access granted on remediation:
Next steps
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for