How to use Power Automate Connector to set up a Flow for events
Applies to:
- Microsoft Defender for Endpoint Plan 1
- Microsoft Defender for Endpoint Plan 2
- Microsoft Defender XDR
Want to experience Microsoft Defender for Endpoint? Sign up for a free trial.
Automating security procedures is a standard requirement for every modern Security Operations Center (SOC). For SOC teams to operate in the most efficient way, automation is a must. Use Microsoft Power Automate to help you create automated workflows and build an end-to-end procedure automation within a few minutes. Microsoft Power Automate supports different connectors that were built exactly for that.
Use this article to guide you in creating automations that are triggered by an event, such as when a new alert is created in your tenant. Microsoft Defender API has an official Power Automate Connector with many capabilities.
Note
For more information about premium connectors licensing prerequisites, see Licensing for premium connectors.
Usage example
The following example demonstrates how to create a Flow that is triggered anytime a new Alert occurs on your tenant. You'll be guided on defining what event starts the flow and what next action will be taken when that trigger occurs.
Log in to Microsoft Power Automate.
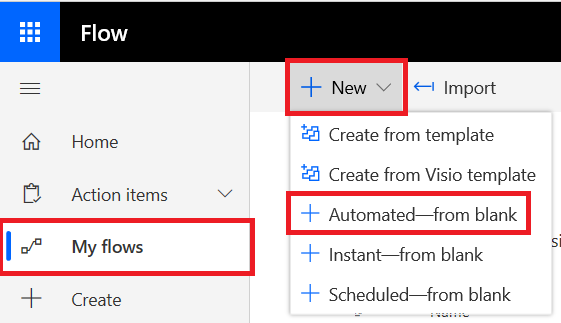
Go to My flows > New > Automated-from blank.
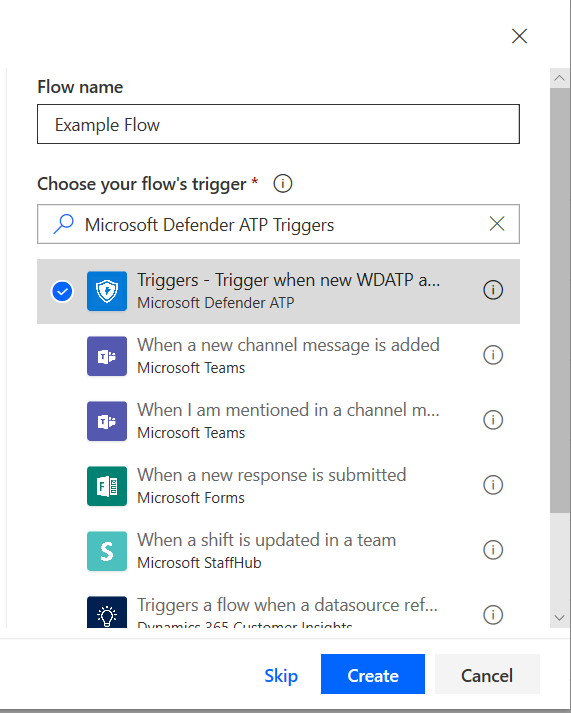
Choose a name for your Flow, search for "Microsoft Defender ATP Triggers" as the trigger, and then select the new Alerts trigger.
Now you have a Flow that is triggered every time a new Alert occurs.
All you need to do now is choose your next steps. For example, you can isolate the device if the Severity of the Alert is High and send an email about it. The Alert trigger provides only the Alert ID and the Machine ID. You can use the connector to expand these entities.
Get the Alert entity using the connector
Choose Microsoft Defender ATP for the new step.
Choose Alerts - Get single alert API.
Set the Alert ID from the last step as Input.
Isolate the device if the Alert's severity is High
Add Condition as a new step.
Check if the Alert severity is equal to High.
If yes, add the Microsoft Defender ATP - Isolate machine action with the Machine ID and a comment.
Add a new step for emailing about the Alert and the Isolation. There are multiple email connectors that are easy to use, such as Outlook or Gmail.
Save your flow.
You can also create a scheduled flow that runs Advanced Hunting queries and much more!
Related topic
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for