Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Applies to:
Onboarding
If you're new to Microsoft Defender XDR and Defender Experts for Hunting:
Upon getting your welcome email, select Log into Microsoft Defender XDR.
Sign in if you already have a Microsoft account. If none, create one.
The Microsoft Defender XDR quick tour gets you familiar with the security suite, where the capabilities are and how important they are. Select Take a quick tour.
Read the short descriptions about what the Microsoft Defender Experts service is and the capabilities it provides. Select Next. You see the welcome page:
Receive Defender Experts Notifications
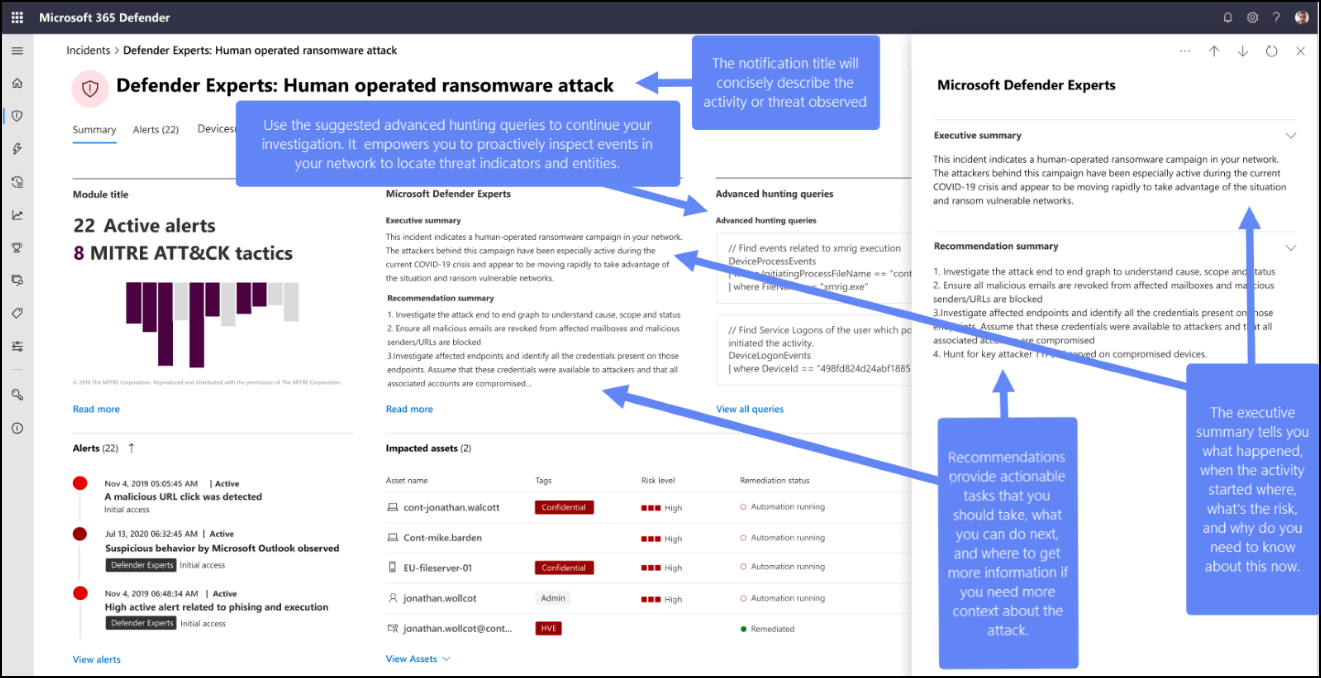
The Defender Experts Notifications service includes:
- Threat monitoring and analysis, reducing dwell time and the risk to your business
- Hunter-trained artificial intelligence to discover and target both known attacks and emerging threats
- Identification of the most pertinent risks, helping SOCs maximize their effectiveness
- Help in scoping compromises and as much context as can be quickly delivered to enable a swift SOC response
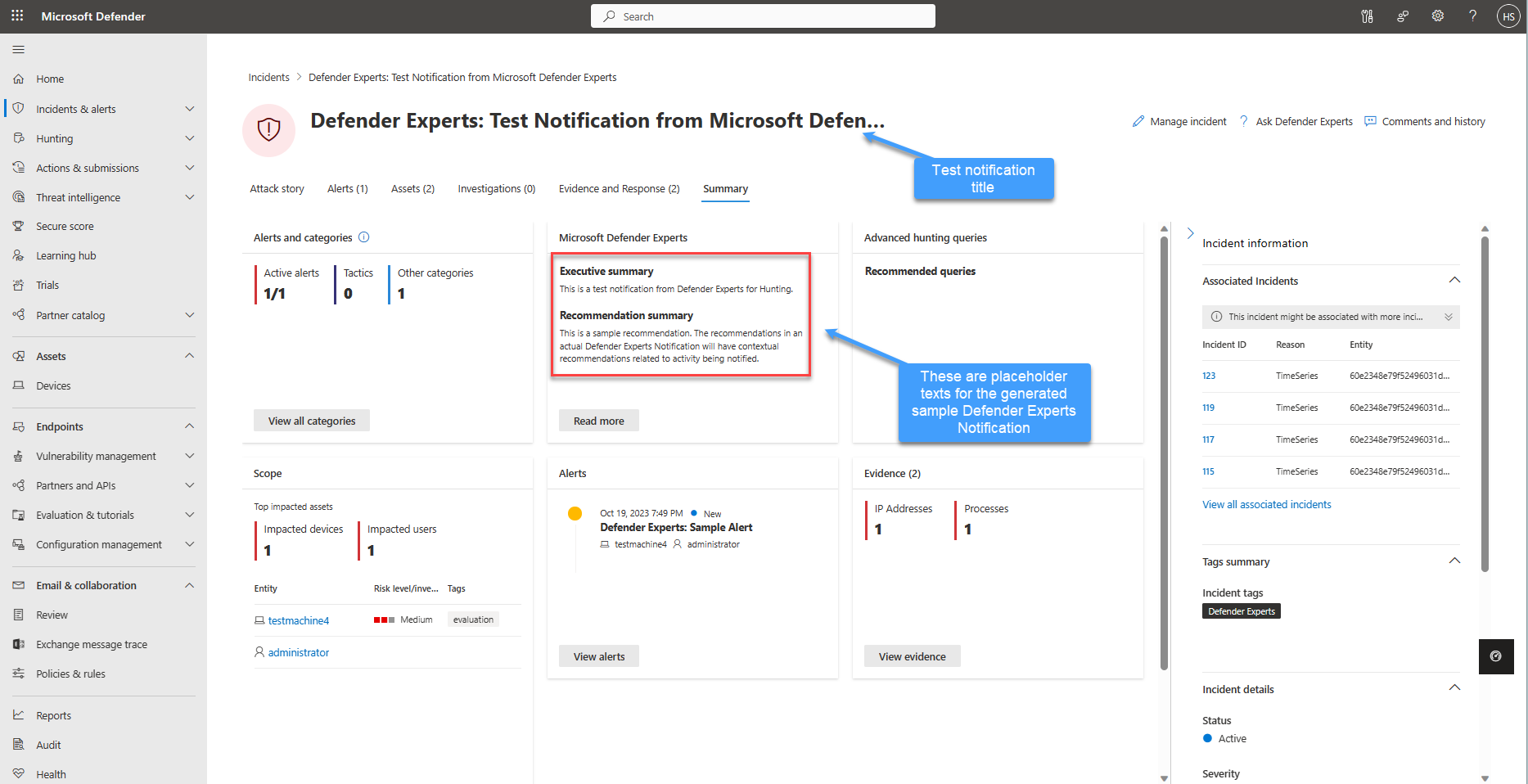
Refer to the following screenshot to see a sample Defender Experts Notification:
Where to find Defender Experts Notifications
You can receive Defender Experts Notifications from Defender Experts through the following mediums:
- The Microsoft Defender portal's Incidents page
- The Microsoft Defender portal's Alerts page
- OData alerting API and REST API
- DeviceAlertEvents table in Advanced hunting
- Your email if you configure an email notifications rule
Filter to view just the Defender Experts Notifications
You can filter your incidents and alerts if you want to only see the Defender Experts Notifications among the many alerts. To do so:
- On the navigation menu, go to Incidents & alerts > Incidents > select the
 icon.
icon. - Scroll down to Service/detection sources then select the Microsoft Defender Experts checkboxes under Microsoft Defender for Endpoint and Microsoft Defender XDR.
- Select Apply.
Set up Defender Experts email notifications
You can set up Microsoft Defender XDR to notify you or your staff with an email about new incidents or updates to existing incidents, including those observed by Microsoft Defender Experts. Learn more about getting incident notifications by email.
- In the Microsoft Defender XDR navigation pane, select Settings > Microsoft Defender XDR > Email notifications > Incidents.
- Update your existing email notification rules or create a new one. For more information, see Auditing.
- On the rule's Notification settings page, make sure to configure the following:
- Source – Choose Microsoft Defender Experts under Microsoft Defender XDR and Microsoft Defender for Endpoint.
- Alert severity – Choose the alert severities that will trigger an incident notification. For example, if you only want to be informed about high-severity incidents, select High.
Generate sample Defender Experts Notifications
You can generate a sample Defender Experts Notification to start experiencing the Defender Experts for Hunting service without having to wait for an actual critical activity to happen in your environment. Generating a sample notification also lets you test the email notifications you might have previously configured in the Microsoft Defender portal for this service, as well as test the configuration of playbooks (if configured for such notifications) and rules in your Security Information and Event Management (SIEM) environment.
A sample Defender Experts Notification shows up in your Incidents page with the title Defender Experts: Test Notification from Microsoft Defender Experts. The contents of the notification are placeholder texts, while the other elements such as alerts are randomly generated from events present in your tenant and aren't actually impacted.
To generate a sample notification:
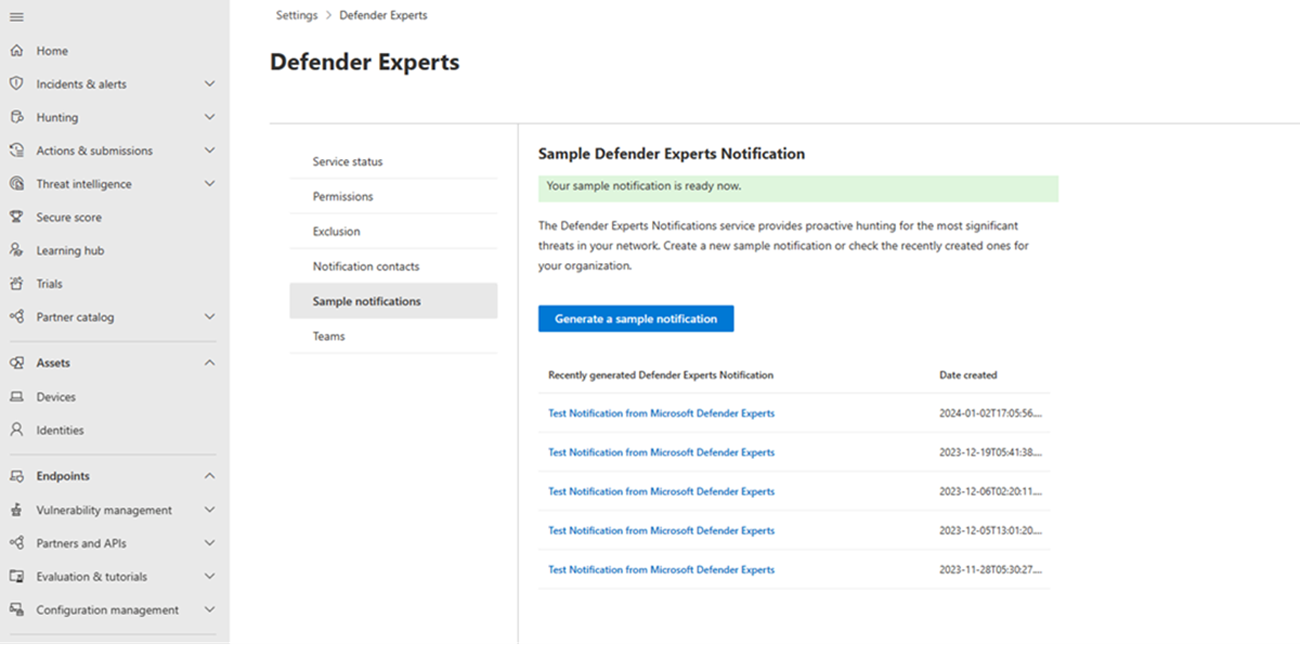
In your Microsoft Defender XDR navigation pane, go to Settings > Defender Experts and then select Sample notifications.
Select Generate a sample notification. A green status message appears, confirming that your sample notification is ready for review.
Under Recently generated Defender Experts Notification, select a link from the list to view its corresponding generated sample notification. The most recent sample appears on the top of the list. Selecting a link redirects you to the Incidents page.
Next step
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender XDR Tech Community.