STEP 1: Configure your network environment to ensure connectivity with Defender for Endpoint service
Applies to:
- Microsoft Defender for Endpoint Plan 1
- Microsoft Defender for Endpoint Plan 2
- Microsoft Defender XDR
Want to experience Defender for Endpoint? Sign up for a free trial.
Important
Some information in this article relates to a prereleased product which may be substantially modified before it's commercially released. Microsoft makes no warranties, expressed or implied, with respect to the information provided here.
Before you onboard devices to Defender for Endpoint, make sure your network is configured to connect to the service. The first step of this process involves adding URLs to the allowed domains list if your proxy server or firewall rules prevent access to Defender for Endpoint. This article also includes information about proxy and firewall requirements for older versions of Windows client and Windows Server.
Enable access to Microsoft Defender for Endpoint service URLs in the proxy server
By default, if a proxy or firewall is blocking all traffic and allowing only specific domains, then add the domains listed in the downloadable sheet to the allowed domains list.
The following downloadable spreadsheet lists the services and their associated URLs that your network must be able to connect. Ensure there are no firewall or network filtering rules to deny access for these URLs. Optionally, you may need to create an allow rule specifically for them.
Note
(Applies to public preview)
- As part of the preview, certain Defender for Endpoint services are consolidated behind the URL:
*.endpoint.security.microsoft.com. You have the option to use the reduced set of URLs in Microsoft Defender XDR for Defender for Endpoint. You also have the new option of configuring allow lists using static Defender for Endpoint dedicated IP ranges. For more information, see onboarding devices using streamlined method and review the updated list in the preceding table. - To use the new onboarding method, devices must meet specific prerequisites and use a new onboarding package. For more information, see prerequisites. You can migrate previously onboarded devices. See, migrating devices to streamlined connectivity.
- Certain services are not included in this consolidation. You must verify that you maintain connectivity with the required services. For details on services not included in the consolidation, see the streamlined URL sheet or onboarding devices using streamlined method.
- Devices running the MMA agent are not supported under streamlined solution and must be onboarded using the down-level method. For a list of required URLs, see the MMA tab in the streamlined URL list. Devices running legacy Windows version 1607, 1703, 1709, or 1803 can onboard using the new onboarding package but still require a longer list of URLs. For more information, see the preceding table.
| Spreadsheet of domains list | Description |
|---|---|
| Microsoft Defender for Endpoint consolidated URL list (NEW - Streamlined) |
IMPORTANT: Currently in public preview. Spreadsheet of consolidated URLs for streamlining device connectivity. Download the spreadsheet here. Applicable OS: For complete list, see streamlined connectivity. - Windows 10 1809+ - Windows 11 - Windows Server 2019 - Windows Server 2022 - Windows Server 2012 R2, Windows Server 2016 R2 running Defender for Endpoint modern unified solution (requires installation through MSI). - macOS supported versions running 101.23102.* + - Linux supported versions running 101.23102.* + Minimum component versions: - Antimalware client: 4.18.2211.5 - Engine: 1.1.19900.2 - Security intelligence: 1.391.345.0 - Xplat version: 101.23102.* + - Sensor/ KB version: >10.8040.*/ March 8, 2022+ If you are moving previously onboarded devices to the streamlined approach, see Migrating device connectivity. |
| Microsoft Defender for Endpoint URL list for commercial customers (Standard) | Spreadsheet of specific DNS records for service locations, geographic locations, and OS for commercial customers. Download the spreadsheet here. Microsoft Defender for Endpoint Plan 1 and Plan 2 share the same proxy service URLs. |
| Microsoft Defender for Endpoint URL list for Gov/GCC/DoD | Spreadsheet of specific DNS records for service locations, geographic locations, and OS for Gov/GCC/DoD customers. Download the spreadsheet here. |
Note
- Windows 10 version 1607, 1703, 1709, 1803 (RS1-RS4) are supported on the onboarding package but require a longer URL list (see updated URL sheet). These versions do not support reonboarding (must be fully offboarded first).
- Devices running on Windows 7, Windows 8.1, Windows Server 2008 R2 MMA, Servers not upgraded to Unified Agent (MMA) will need to continue using MMA onboarding method.
If a proxy or firewall has HTTPS scanning (SSL inspection) enabled, exclude the domains listed in the above table from HTTPS scanning.
In your firewall, open all the URLs where the geography column is WW. For rows where the geography column isn't WW, open the URLs to your specific data location. To verify your data location setting, see Verify data storage location and update data retention settings for Microsoft Defender for Endpoint. Don't exclude the URL *.blob.core.windows.net from any kind of network inspection. Instead, exclude only the blob URLs that are specific to MDE and listed in the spreadsheet of domains list.
Note
Applies to standard set of URLS:
Windows devices running with version 1803 or earlier needs settings-win.data.microsoft.com.
URLs that include v20 in them are only needed if you have Windows devices running version 1803 or later. For example, us-v20.events.data.microsoft.com is needed for a Windows device running version 1803 or later and onboarded to US Data Storage region.
If a proxy or firewall is blocking anonymous traffic from the Defender for Endpoint sensor and it's connecting from system context, it's important to make sure anonymous traffic is permitted in your proxy or firewall for the previously listed URLs.
Note
Microsoft does not provide a proxy server. These URLs are accessible via the proxy server that you configure.
Important
In compliance with Defender for Endpoint security and compliance standards, your data will be processed and stored in accordance with your tenant's physical location. Based on client location, traffic may flow through any of these IP regions (which correspond to Azure datacenter regions). For more information, see Data storage and privacy.
Microsoft Monitoring Agent (MMA) - proxy and firewall requirements for older versions of Windows client or Windows Server
Note
(Applies to public preview)
Services using MMA-based solutions are not able to leverage the new streamlined connectivity solution (consolidated URL and option to use static IPs). For Windows Server 2016 and Windows Server 2012 R2, you will need to update to the new unified solution.
The information in the list of proxy and firewall configuration information is required to communicate with Log Analytics agent (often referred to as Microsoft Monitoring Agent) for previous versions of Windows, such as Windows 7 SP1, Windows 8.1, and Windows Server 2008 R2*.
| Agent Resource | Ports | Direction | Bypass HTTPS inspection |
|---|---|---|---|
*.ods.opinsights.azure.com |
Port 443 | Outbound | Yes |
*.oms.opinsights.azure.com |
Port 443 | Outbound | Yes |
*.blob.core.windows.net |
Port 443 | Outbound | Yes |
*.azure-automation.net |
Port 443 | Outbound | Yes |
Note
These connectivity requirements apply to the previous Microsoft Defender for Endpoint of Windows Server 2016, and Windows Server 2012 R2 that requires MMA. Instructions to onboard these operating systems with the new unified solution are at Onboard Windows servers, or migrate to the new unified solution at Server migration scenarios in Microsoft Defender for Endpoint.
Note
As a cloud-based solution, the IP range can change. It's recommended, you move to DNS resolving setting.
Onboard devices without Internet access
For devices with no direct internet connection, the use of a proxy solution is the recommended approach. For older Windows devices onboarded using the previous, MMA-based solution the use of the OMS gateway solution provides an alternative approach.
Note
(Applies to public preview)
With this preview, you can leverage firewall devices with static IP ranges. For more information, see: Streamlined device connectivity and streamlined URL list.
For more information about onboarding methods, see the following articles:
Important
- Microsoft Defender for Endpoint is a Cloud security solution. "Onboard devices without Internet access" means that Internet access for the endpoints must be configured through a proxy. Microsoft Defender for Endpoint does not support endpoints without direct or proxy Internet access. System wide proxy configuration recommended.
- Windows or Windows Server in disconnected environments must be able to update Certificate Trust Lists offline via an internal file or web server.
- For more information about updating CTLs offline, see Configure a file or web server to download the CTL files.
Devices running Windows 10 or later, Windows Server 2012 R2 or later, Linux and macOS
Depending on the operating system, the proxy to be used for Microsoft Defender for Endpoint can be configured automatically, typically by using autodiscovery or an autoconfig file, or statically specific to Defender for Endpoint services running on the device.
- For Windows devices, see Configure device proxy and Internet connectivity settings
- For Linux devices, see Configure Microsoft Defender for Endpoint on Linux for static proxy discovery
- For macOS devices, see Microsoft Defender for Endpoint on Mac
Windows devices running the previous MMA-based solution
Note
- An OMS gateway server cannot be used as proxy for disconnected Windows or Windows Server devices when configured via 'TelemetryProxyServer' registry or GPO.
- For Windows or Windows Server - while you may use TelemetryProxyServer, it must point to a standard proxy device or appliance.
- Set up Azure Log Analytics (formerly known as OMS Gateway) to act as proxy or hub:
- Azure Log Analytics Agent
- Install and configure Microsoft Monitoring Agent (MMA) point to Defender for Endpoint Workspace key & ID
Onboard previous versions of Windows
Note
Any client that has no access to the internet cannot be onboarded to Microsoft Defender Endpoint. A client must either have access to the required URLs directly, or it must have access via a proxy or firewall.
As part of the streamlined preview, you can now leverage IP addresses as alternatives to certain Defender for Endpoint service URLs.
Confirm Microsoft Monitoring Agent (MMA) Service URL Requirements
See the following guidance to eliminate the wildcard (*) requirement for your specific environment when using the Microsoft Monitoring Agent (MMA) for previous versions of Windows.
Onboard a previous operating system with the Microsoft Monitoring Agent (MMA) into Defender for Endpoint (for more information, see Onboard previous versions of Windows on Defender for Endpoint and Onboard Windows servers).
Ensure the machine is successfully reporting into the Microsoft Defender portal.
Run the TestCloudConnection.exe tool from
C:\Program Files\Microsoft Monitoring Agent\Agentto validate the connectivity, and to get the required URLs for your specific workspace.Check the Microsoft Defender for Endpoint URLs list for the complete list of requirements for your region (refer to the Service URLs Spreadsheet).
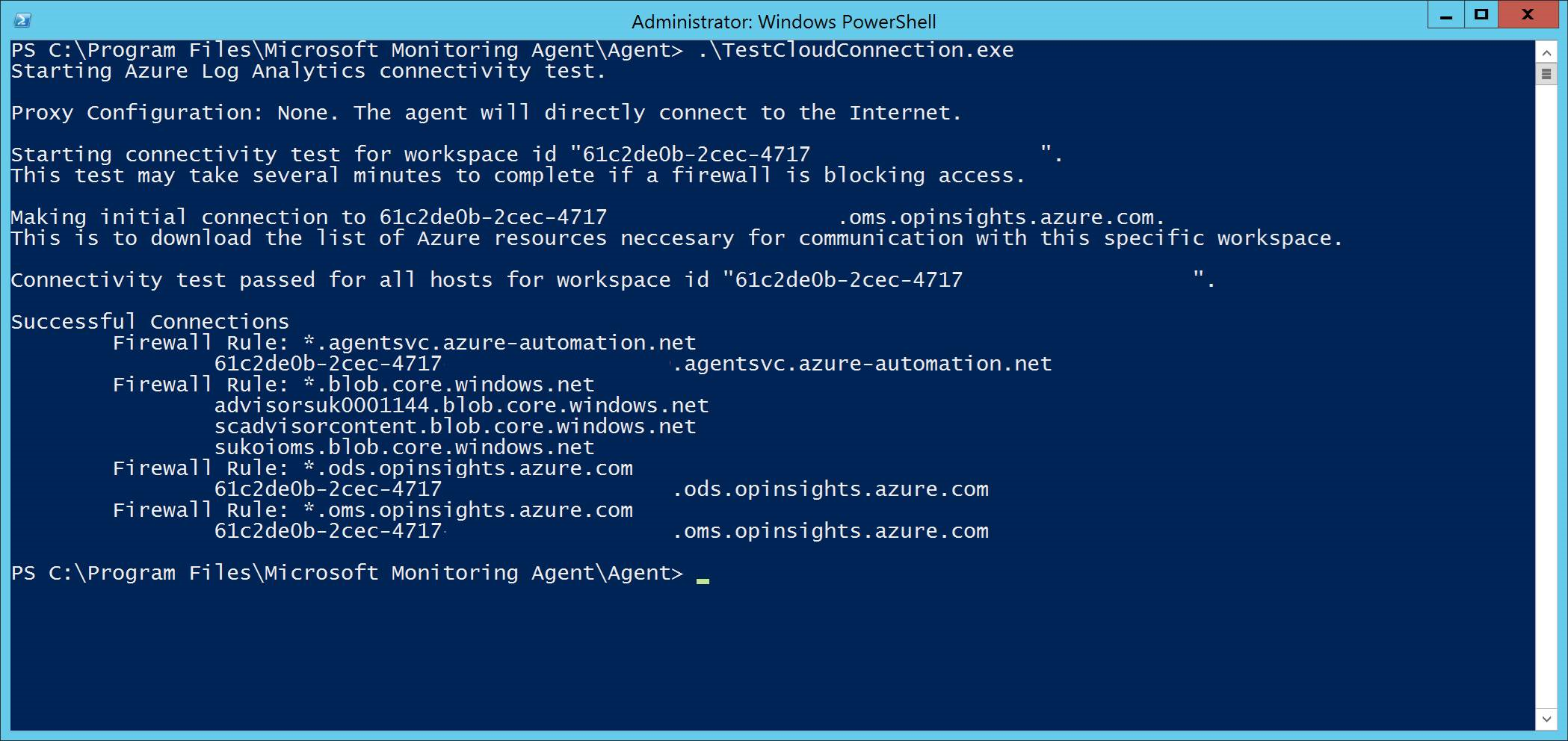
The wildcards (*) used in *.ods.opinsights.azure.com, *.oms.opinsights.azure.com, and *.agentsvc.azure-automation.net URL endpoints can be replaced with your specific Workspace ID. The Workspace ID is specific to your environment and workspace. It can be found in the Onboarding section of your tenant within the Microsoft Defender portal.
The *.blob.core.windows.net URL endpoint can be replaced with the URLs shown in the "Firewall Rule: *.blob.core.windows.net" section of the test results.
Note
In the case of onboarding via Microsoft Defender for Cloud, multiple workspaces can be used. You will need to perform the TestCloudConnection.exe procedure on the onboarded machine from each workspace (to determine, if there are any changes to the *.blob.core.windows.net URLs between the workspaces).
Next step
STEP 2: Configure your devices to connect to the Defender for Endpoint service using a proxy
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for