4.1 Interactive Logon Using Smart Cards
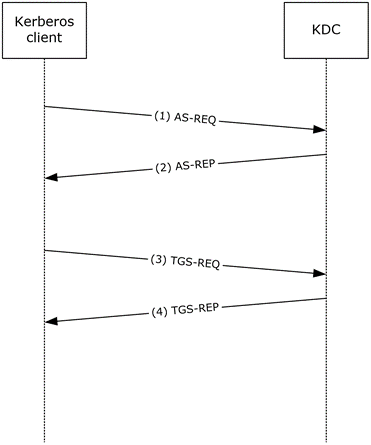
Figure 1: Interactive logon
Step 1: A user attempts to log on to a client. At the logon screen, the user selects the certificate and types the PIN. Using the PIN to unlock the smart card, the client generates an AS-REQ with PA-PK-AS-REQ pre-authentication data ([RFC4556] section 3.2.1) and sends the request to the KDC.
Step 2: The KDC validates the AS-REQ ([RFC4120] section 3.1.2), including verifying the user's signature and validating certificate ([RFC4556] section 3.2.2). If the AS-REQ is valid, the KDC generates an AS-REP ([RFC4556] section 3.2.3), with a PAC ([MS-KILE] section 3.3.5.3.2) in the authorization_data field of the TGT, and sends the reply to the client.
Step 3: The client validates the AS-REP ([RFC4556] section 3.2.4). For interactive logons, the client runtime requests authentication to host/hostname.domain, where hostname is the actual name of the client machine, and domain is the domain or realm of the client machine. If the AS-REP is valid, the client generates a TGS-REQ based on the TGT that is obtained in step 2 to obtain a service ticket for host/hostname.domain ([RFC4120] section 3.3.1) and sends the request to the KDC.
Step 4: The KDC validates the TGS-REQ ([RFC4120] section 3.3.2) ([MS-KILE] section 3.3.5.7.1). If the TGS-REQ is valid, the KDC adds Domain Local Groups to the PAC ([MS-KILE] section 3.3.5.7.3), generates a TGS-REP ([RFC4120] section 3.3.3), and sends the reply to the client.
The client validates the TGS-REP ([MS-KILE] section 3.3.4). If the TGS-REP is valid, the service ticket is then interpreted by the Kerberos runtime within the local workstation.
The following fields from the KERB_VALIDATION_INFO field of the PAC ([MS-PAC] Section 2.5) are required by the interactive logon client runtime to authorize the user for local interactive logon, and to establish the necessary management profile for the user:
LogonTime
LogoffTime
KickOffTime
PasswordLastSet
PasswordCanChange
EffectiveName
FullName
LogonScript
ProfilePath
HomeDirectory
HomeDirectoryDrive
LogonCount
BadPasswordCount
LogonServer
LogonDomainName
UserAccountControl