Events
Power BI DataViz World Championships
Feb 14, 4 PM - Mar 31, 4 PM
With 4 chances to enter, you could win a conference package and make it to the LIVE Grand Finale in Las Vegas
Learn moreThis browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Multi-tenancy is the most common app scenario and the one which is used for apps distributed using Microsoft AppSource, but you can also use multi-tenancy without listing your application with Microsoft AppSource.
Each Microsoft Dataverse organization is associated with an Microsoft Entra ID tenant. Your web application or service is registered with its own Microsoft Entra ID tenant.
In this scenario any Dataverse tenant can potentially use your multi-tenant application after an administrator grants consent for the application to access data.
To create and test a multi-tenant application that uses server-to-server (S2S) authentication you will need:
An Microsoft Entra ID tenant you will use to publish your application or service.
Two (2) Dataverse subscriptions
The application you will create must be registered with the Microsoft Entra ID tenant you will use when you publish the application.
At a high level, the process consists of:
You will create a multi-tenant web application or service which uses Microsoft Entra ID as the authentication provider.
Exactly how you do this will not be the focus of this topic. There are a number of ways you can approach this and make choices that fit your requirements or preferences. See the following links for more information and samples:
Microsoft Entra ID requires the following values to register your application:
| Value | Description |
|---|---|
| Application ID URI | The identifier for an application. This value is sent to Microsoft Entra ID during authentication to indicate which application the caller wants a token for. Additionally, this value is included in the token so that the application knows it was the intended target. |
| Reply URL and Redirect URI | In the case of a Web API or web application, the Reply URL is the location to which Microsoft Entra ID will send the authentication response, including a token if authentication was successful. |
| Client ID | The ID for an application, which is generated by Microsoft Entra ID when the application is registered. When requesting an authorization code or token, the client ID and key are sent to Microsoft Entra ID during authentication. |
| Key | The key that is sent along with a client ID when authenticating to Microsoft Entra ID to call a web API . |
When the application is registered it will be assigned an Microsoft Entra ID Object Id, a unique identifier for the registered application.
If you create a new ASP.NET MVC application with Visual Studio you will have options to specify that the application will support the multi-tenant functionality. The template for an MVC application provides the option to specify what kind of authentication occurs. You will have the option to choose the authentication method by configuring the properties of your project when you create it. The following diagram shows the options available:
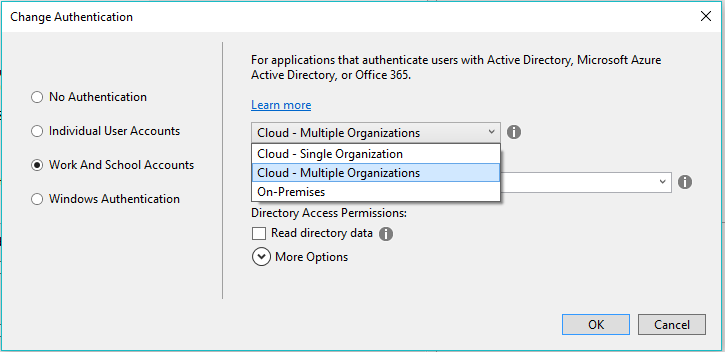
When you configure a project with these options it will be configured to use OWIN middleware and scaffolding for a basic application that supports this scenario. With some basic modifications it can be adapted to work with Dataverse.
In the process of creating and registering your application for development you will most likely use https://localhost as the Sign-on URL and Reply URL values so you can test and debug your application locally before publishing. You will need to change these values before you publish your app.
When you register your app you must generate a key, also known as a ClientSecret. These keys can be configured for a 1 or 2-year duration. As the host of the application you must treat this value like a password and it is your responsibility to manage renewal of the keys before they expire. You may want to use Key Vault. More information: https://azure.microsoft.com/services/key-vault/
This is the reason why your Dataverse tenant must be associated with your Microsoft Entra ID tenant. If your Microsoft Entra ID tenant is not associated with a Dataverse tenant, you will not be able to perform the following steps.
When your application accesses the Dataverse data of one of the subscribers of your application, it will require an application user in the subscriber’s Dataverse organization. Like any Dataverse user, this application user must be associated with at least one security role which defines the data the user is able to access.
The SystemUser Table has three new columns to store this data.
| Schema Name | Display Name | Type | Description |
|---|---|---|---|
| ApplicationId | Application ID | UniqueidentifierType | The identifier for the application. This is used to access data in another application. |
| ApplicationIdUri | Application ID URI | StringType | The URI used as a unique logical identifier for the external app. This can be used to validate the application |
| AzureActiveDirectoryObjectId | Azure AD Object ID | UniqueidentifierType | This is the application directory object Id. |
This systemuser``AzureActiveDirectoryObjectId property value must be a reference to the Microsoft Entra ID Object Id of your registered application. This reference will be set in Dataverse when the application user is created based on the ApplicationId value.
Note
When you are initially developing your application with your own Dataverse tenant and the Microsoft Entra ID tenant associated with it, you can simply create the application user because the registered application is already part of your Microsoft Entra ID tenant.
However, in order to create the application user in a different organization for testing, or whenever a subscriber will use your application, they must first grant consent for your application, so the steps in the process are different. See Test your application using a separate Dynamics 365 tenant for more information.
In the next step you will create a Dataverse application user. The privileges and access rights for this user will be defined by a custom security role you set. Before you create the application user, you must create a custom security role so you can associate the user to it. More information: Create or edit a security role
Note
The application user cannot be associated with one of the default Dataverse security roles. You must create a custom security role to associate with the application user.
The interactive procedure to create an unlicensed application user is described in this article Create an application user. After creating the application user, associate the user with the custom security role you created in Create a security role for the application user.
More information: Manage application users in the Power Platform admin center
Because the application has been registered with your Microsoft Entra ID tenant and the application user in your development organization is already configured, you can continue to develop your application against your own Dataverse tenant. But this is not a valid test of the multi-tenant capability. You need to test your application on a separate Dataverse tenant.
Before you test your application with a separate Dataverse tenant, an administrator for the Microsoft Entra ID tenant must grant consent for the application. The administrator grants consent by navigating to the application using a browser. The first time they access the application, they will see a dialog like this:
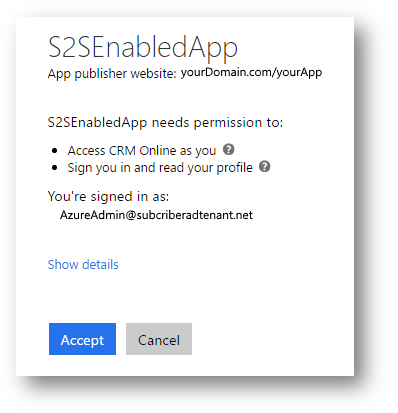
When they grant consent, your registered application will be added to the Microsoft Entra ID Enterprise applications list and it is available to the users of the Microsoft Entra ID tenant.
Only after an administrator has granted consent, you must then create the application user in the subscriber’s Dataverse tenant. You can manually create the application user using the steps described in Manually create a Dynamics 365 application user.
For initial tests you may want to manually perform these steps. When you are ready to make your application or service available to subscribers you will want to have a more efficient procedure. This is covered in the next section.
After subscribers grant consent to your application or service you will need an easy, reliable way for them to add the application user and any other required components to their Dataverse organization.
You must include a custom security role which defines what privileges your application requires and then make sure that the application user is associated to that custom security role. Because a custom security role can be included in a solution, you should prepare a managed solution which contains the definition of the custom security role and any other solution components your application requires.
For information about creating custom security roles, see
For information about creating a Dataverse solution, see the following topics:
However, the application user cannot be included with a solution so you will need to provide a way to create this application user and associate it with the custom security role.
There are several ways that you can achieve this, including writing your own program using the web services and having the subscriber run the program.
The Dynamics 365 Package Deployer is an application which can be used to prepare a package to automate transferring solutions and data to a different Dataverse organization. More information: Create packages for the Package Deployer
Use single-tenant server-to-server authentication
Build web applications using server-to-server (S2S) authentication
Authenticate with Microsoft Dataverse web services
Events
Power BI DataViz World Championships
Feb 14, 4 PM - Mar 31, 4 PM
With 4 chances to enter, you could win a conference package and make it to the LIVE Grand Finale in Las Vegas
Learn moreTraining
Module
Ontdek hoe Microsoft Entra Externe ID veilige, naadloze aanmeldingservaringen voor uw consumenten en zakelijke klanten kan bieden. Verken het maken van tenants, app-registratie, stroomaanpassing en accountbeveiliging.
Certification
Microsoft Certified: Power Platform Developer Associate - Certifications
Laat zien hoe u zakelijke taken en processen vereenvoudigt, automatiseert en transformeert met behulp van Microsoft Power Platform Developer.