Stop cookie replay attacks with IP binding
Important
This content is archived and is not being updated. For the latest documentation, go to What is Microsoft Dataverse?. For the latest release plans, go to Dynamics 365 and Microsoft Power Platform release plans.
| Enabled for | Public preview | General availability |
|---|---|---|
| Users by admins, makers, or analysts |  Aug 25, 2022
Aug 25, 2022 |
 Jan 25, 2023
Jan 25, 2023 |
Business value
As an administrator, you'll be able to safeguard your Dataverse platform from cookie replay attacks coming from different computers or IP addresses.
Feature details
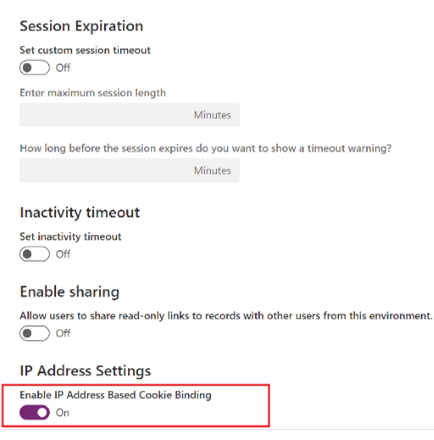
You can stop cookie replay attacks by binding the IP address of the computer with a cookie to block unauthorized access to Dataverse. You can apply this control when needed to help keep your organization secure. This vulnerability can only be exploited if the device is compromised or a man-in-the-middle attack happens, and the browser’s valid cookie is copied by a malicious user. This valid cookie can only be replayed until it expires.
For example, a user copies a valid browser cookie from one computer using publicly available tools and tries to replay the same cookie from a different computer using any publicly available tool. The cookie IP binding feature will evaluate the IP address of the cookie origin in real time and will prompt the user with a message if the IP address of the cookie origin is different than the IP address of request being made.

Today, cookie binding with an IP address doesn't exist, but in 2022 release wave 2, administrators will be able to use cookie IP binding in the Power Platform admin center to block cookie replay attacks.
See also
Announcing Public Preview of IP based cookie binding in Dataverse (blog)